Aceid Cn Mod
Jan 26, 21How to make money in Red Dead online (EASY) 100% SAFE FREE MONEY NO BAN 100% SAFE Hack red dead online cheat engine No mod menuCHEAT ENGINE 👉https//www.

Aceid cn mod. 1 and that a = c(mod n) This problem has been solved!. = c (mod n), assuming that a, c, and n are integers with n > 1 and that a = c(mod n) This problem has been solved!. See the answer See the answer See the answer done loading Show transcribed image text.
= c (mod n), assuming that a, c, and n are integers with n >. See the answer See the answer See the answer done loading Show transcribed image text. 1 and that a = c(mod n) Question 10 (10 pts) Prove a?.
= c (mod n), assuming that a, c, and n are integers with n >. = c (mod n), assuming that a, c, and n are integers with n > 1 and that a = c(mod n) Question 10 (10 pts) Prove a?.

Sensors Free Full Text A Smartcard Based User Controlled Single Sign On For Privacy Preservation In 5g Iot Telemedicine Systems
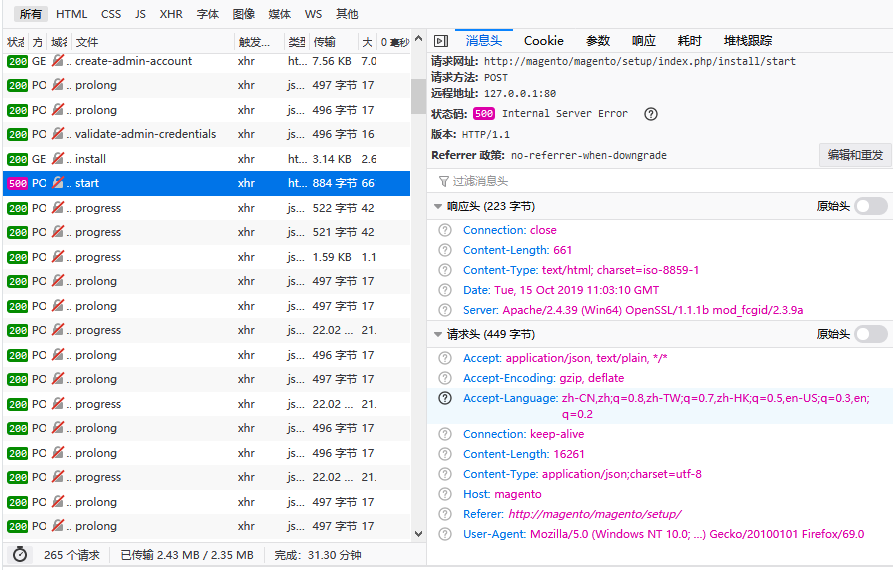
The Last Step Is 500 Errors When Installing Magent Magento Forums

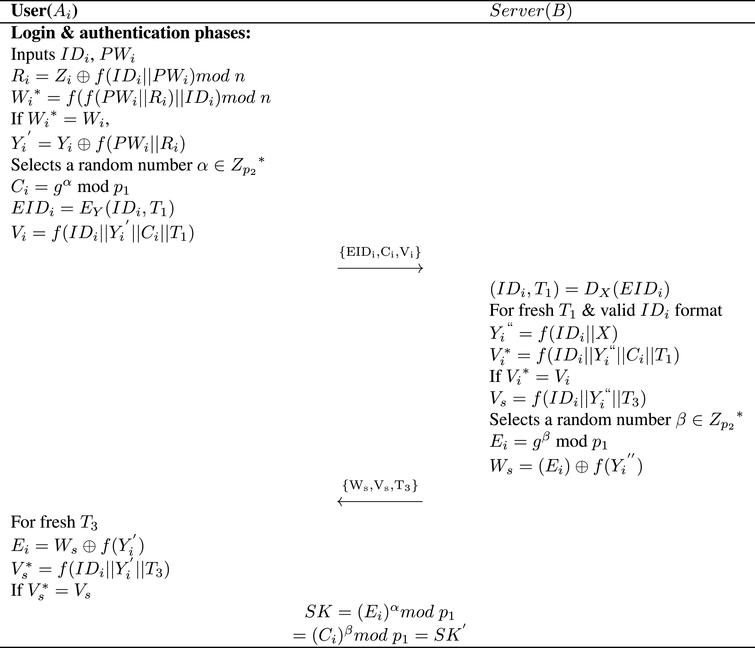
The Login And Key Agreement Stage Of The New Protocol Download Scientific Diagram
Aceid Cn Mod のギャラリー

Andreae Alciati I V C Emblemata E M B L E M A T A 34 Natura Embl E M A Xc V I I P A N A Coluntgentes Naturam Hoc

Cryptanalysis And Improvement Of A Robust Smart Card Based Remote User Password Authentication Scheme Kumari 14 International Journal Of Communication Systems Wiley Online Library
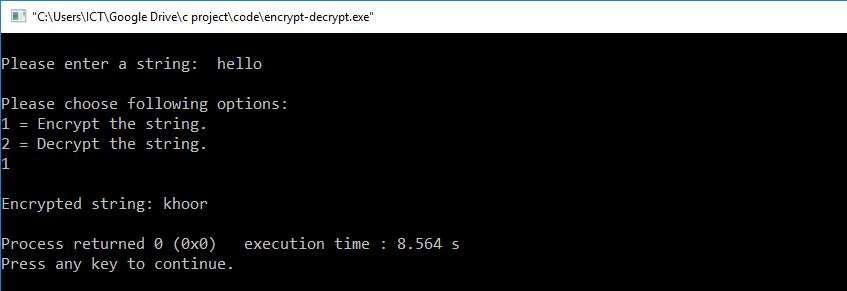
C Program To Encrypt And Decrypt The String Source Code

Cryptanalysis And Security Enhancement Of Zhu S Authentication Scheme For Telecare Medicine Information System Bin Muhaya 15 Security And Communication Networks Wiley Online Library
A Pkc Based User Authentication Scheme Without Smart Card Ios Press

A Two Factor Rsa Based Robust Authentication System For Multiserver Environments

The Physics Mechanisms Of The Weakly Coherent Mode In The Alcator C Mod Tokamak Physics Of Plasmas Vol 23 No 12

Linear Congruential Generator Wikipedia

Efficient Multi Factor User Authentication Protocol With Forward Secrecy For Real Time Data Access In Wsns
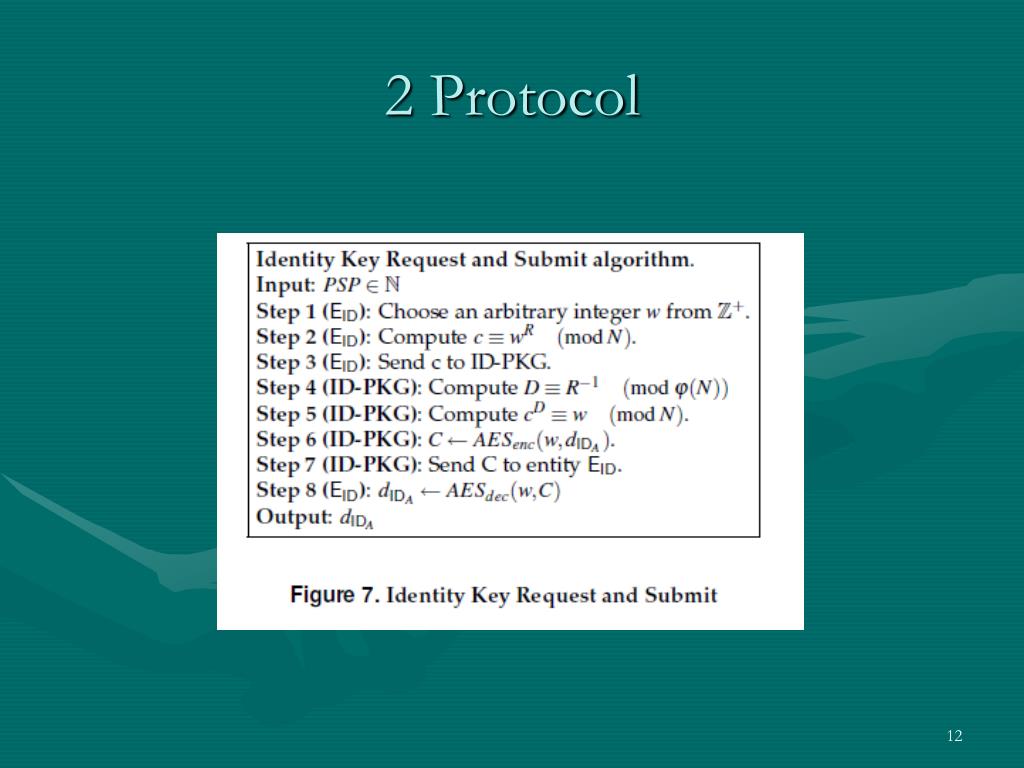
Ppt Identity Based Cryptography For Securing Mobile Phone Calls Powerpoint Presentation Id

Pdf A Lightweight Password Based Authentication Protocol Using Smart Card Semantic Scholar
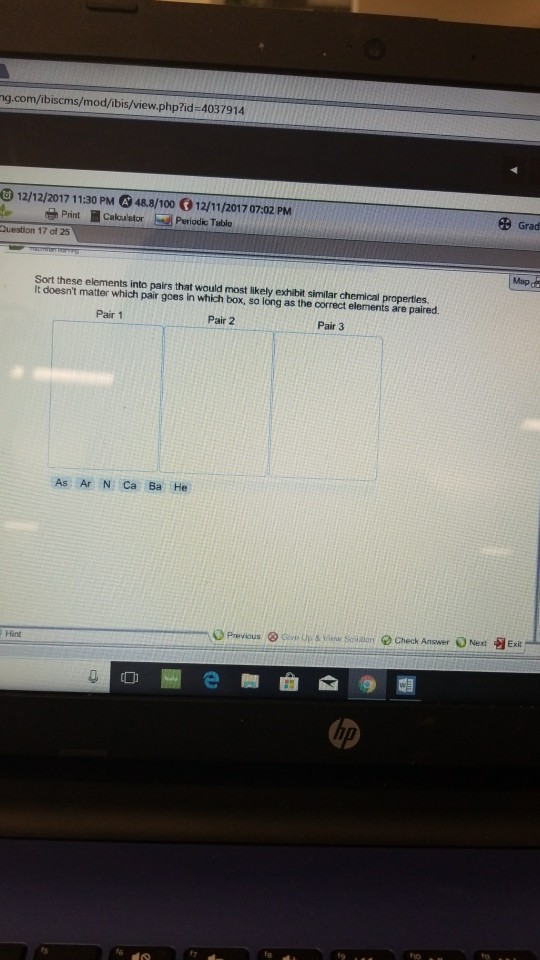
Solved G Com Ibiscms Mod Ibis View Php Id O 12 12 Chegg Com

Groups Rings And Field Lecture Notes Mathematics 6 Docsity

55btw Broadband Router To Enable Wireless Data Connectivity User Manual Ii Calamp

A Secure Remote User Mutual Authentication Scheme Using Smart Cards Vit University

Aircraft Wa638 1949 Gloster Meteor T 7 Mod C N G5 Photo By Chris Hall Photo Id Ac6262
T Mod Pathway A Reduced Sequence For Identification Of Gram Negative Urinary Tract Pathogens Abstract Europe Pmc
Godox Ad0 0ws Ttl Gn60 Hss Flash Built In 2 4g Nirkabel Dan Xpro C N F S O P Transmitter Untuk Canon Nikon Sony Olympus Shopee Indonesia

Pdf Two Factor Mutual Authentication Offloading For Mobile Cloud Computing Semantic Scholar

N 1 Sg Signature Sum Message Blocks Senders
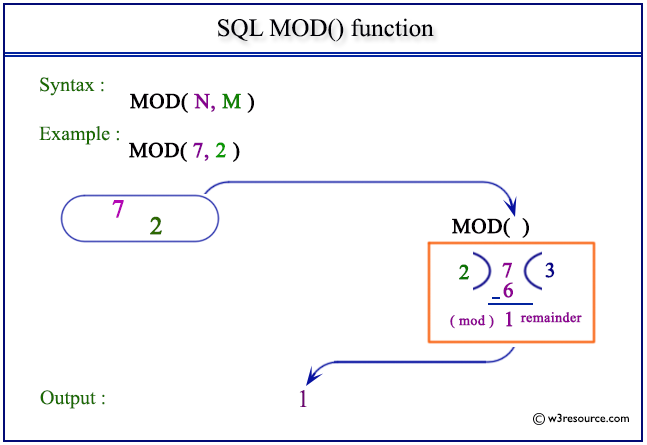
Sql Mod Function W3resource

Login And Authentication Phase Of The Proposed Scheme Download Scientific Diagram
Psm7a7ud Flexwave Prism Hdm 700 Lower Abc Upper C User Manual Rf Modules Installation Guide Adc Telecommunications

Aircraft G Bywd 00 Grob G 115e Tutor T1 C N 139 E Photo By Derek Flewin Photo Id Ac
Eid Ul Fitr1

The Auditing Process Of Yu Et Al S Scheme Download Scientific Diagram

6099s2c Lenovo Storwize V3700 2 5 Inch Storage Controller Unit Brand New Jp Ebay
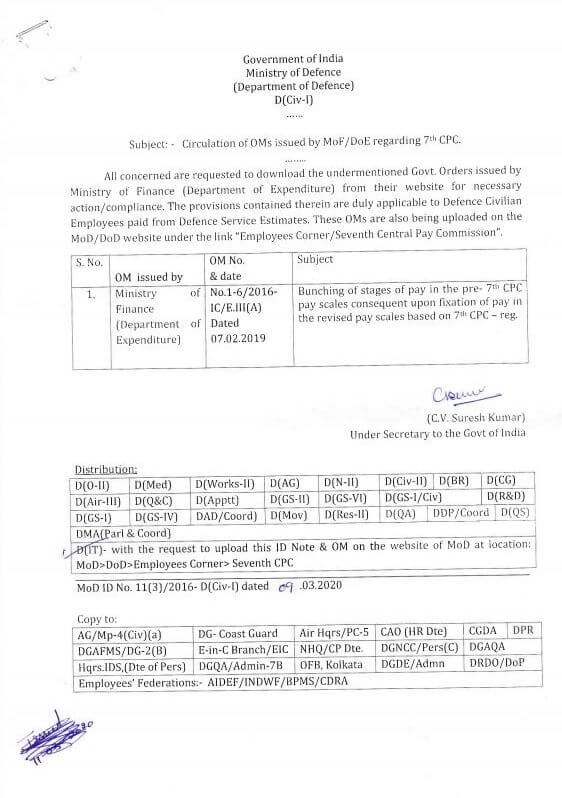
7th Cpc Pay Fixation Bunching Of Stages Of Pay In The Pre 7 Cpc Mod Order For Defence Civilian Employees Central Govt Employees 7th Pay Commission Staff News
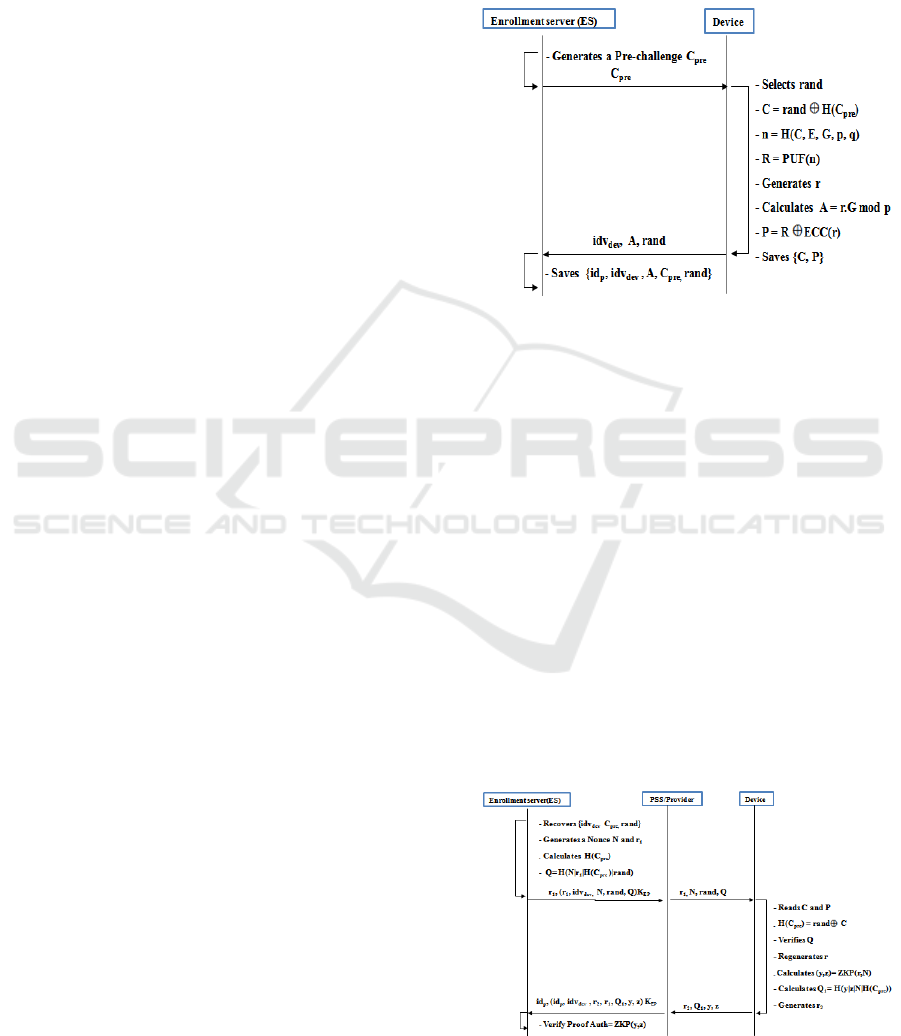
Secure Authentication Solution For Cloud Based Smart City Surveillance System Yosra Ben Dhief Yacine Djemaiel Slim Rekhis And Noureddine Boudriga Communication Networks And Security Research Lab University Of Carthage Tunisia Keywords

Resident Identity Card Wikipedia

Solved Notations Gn Is The Group Of Invertible Congruenc Chegg Com

Dynamic Id Based Remote User Authentication Scheme Using Elgamal Encryption System

Sagetech Avionics Receives Dod Aims Certification For Mode 5 Micro Iff Transponder For Drones Uav Dach E V
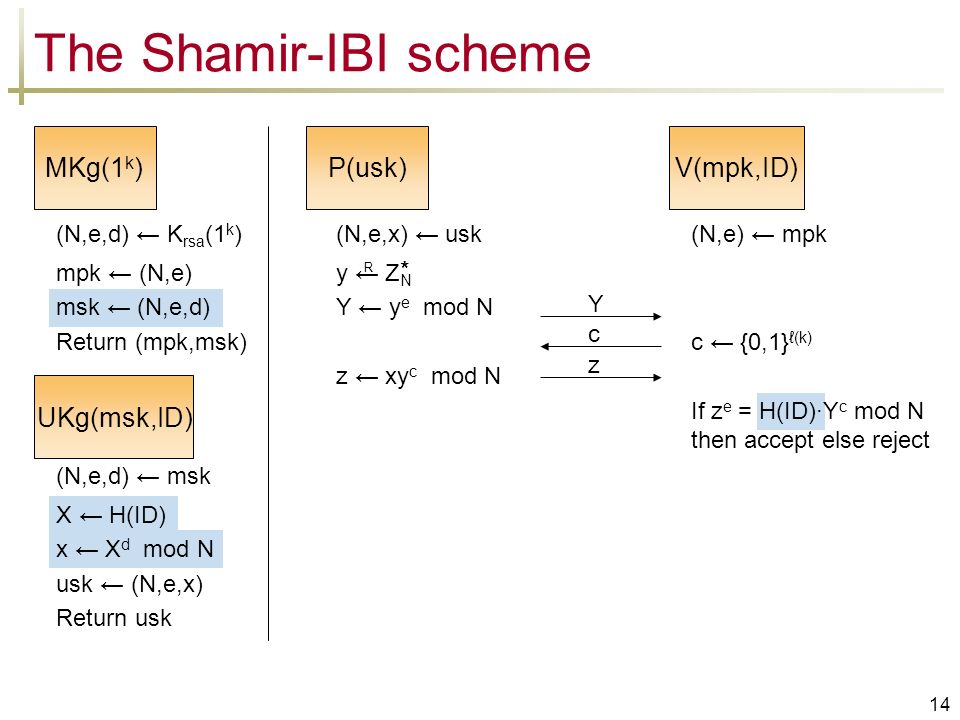
Security Proofs For Identity Based Identification And Signature Schemes Mihir Bellare University Of California At San Diego Usa Chanathip Namprempre Thammasat Ppt Download

Amazon Com Edgecore Networks Layer 3 Switch Ecs5610 52s Computers Accessories
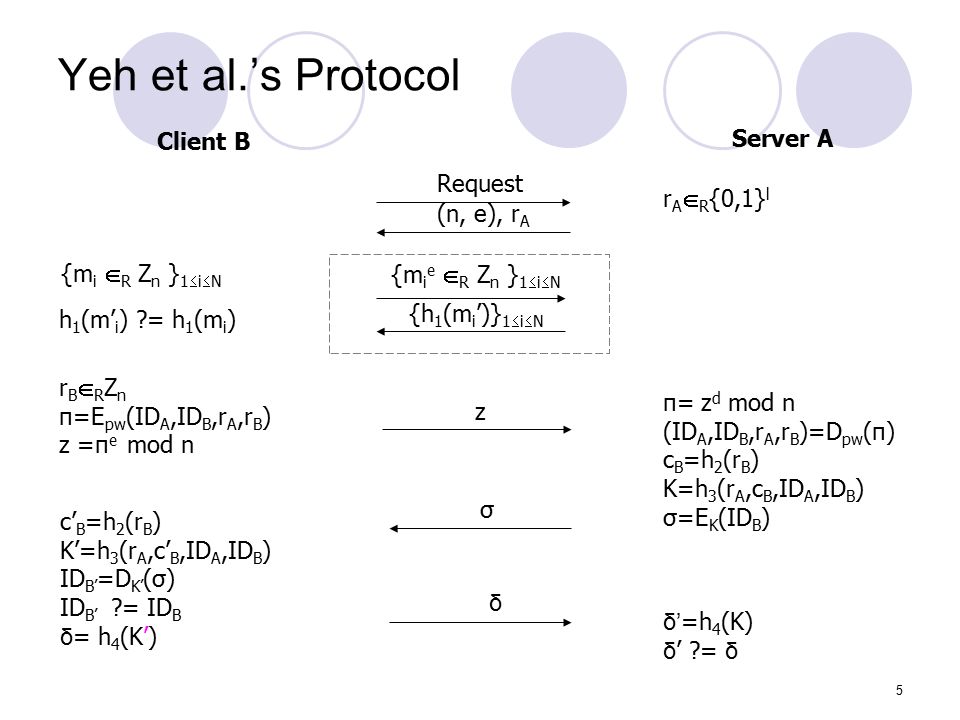
Rsa Based Password Authenticated Key Exchange Protocol Presenter Jung Wen Lo 駱榮問 Ppt Download
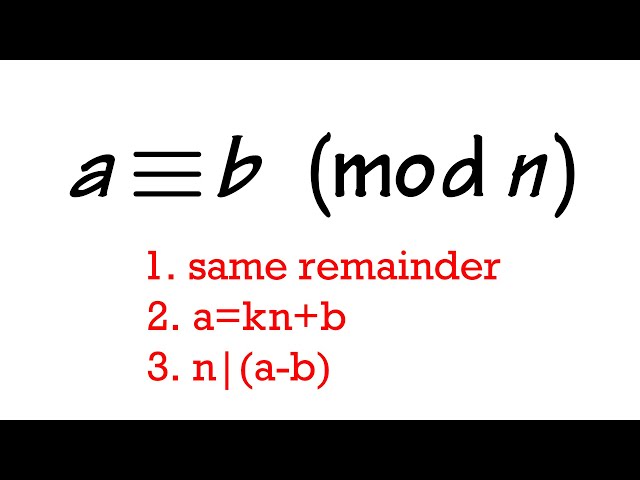
What Does A B Mod N Mean Basic Modular Arithmetic Congruence Youtube

A Secure And Efficient Ecc Based Anonymous Authentication Protocol

Characterization Of The Onset Of Ion Cyclotron Parametric Decay Instability Of Lower Hybrid Waves In A Diverted Tokamak Physics Of Plasmas Vol 21 No 6

Art Now Vol 4 Sendpoints Cn
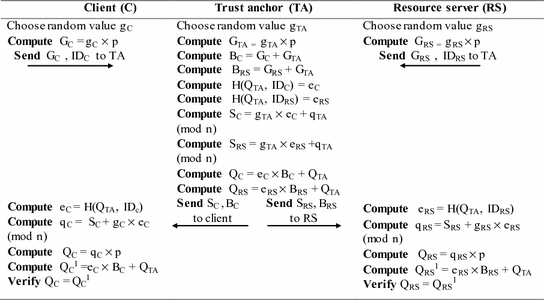
Energy Efficient Elliptic Curve Cryptography Based Dtls Key Establishment Protocol For Iot Communication Springerlink

Analysis And Improvement Of A Robust Smart Card Based Authentication Scheme For Multi Server Architecture Semantic Scholar
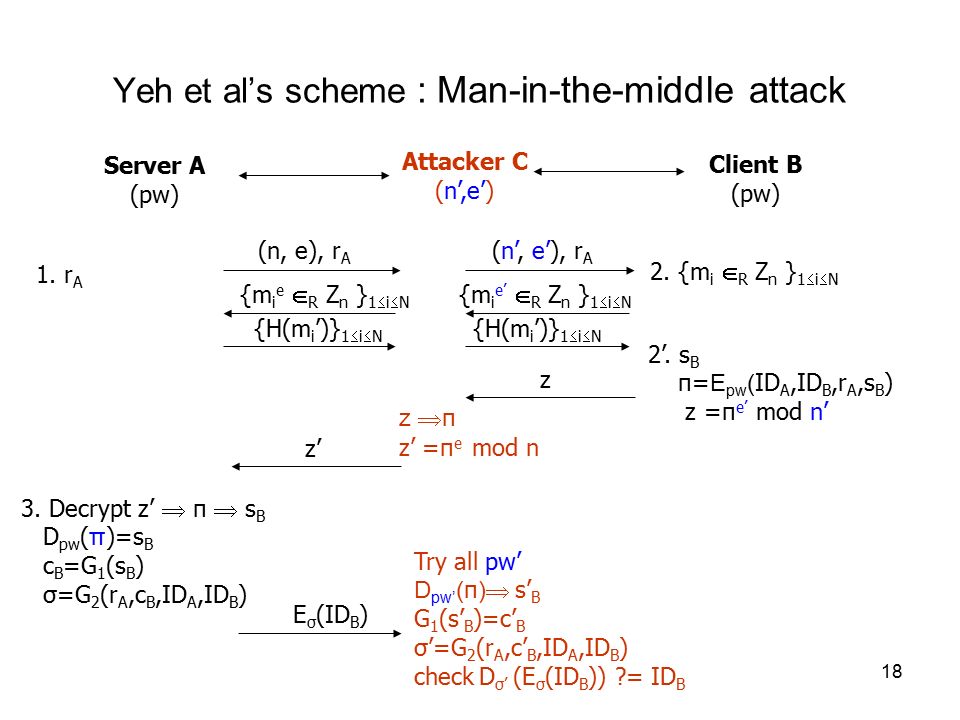
Rsa Based Password Authenticated Key Exchange Protocol Presenter Jung Wen Lo 駱榮問 Ppt Download

Presentation

Pdf Cryptanalysis Of Id Based Proxy Blind Signature Scheme Over Lattice
Some Attacks On Chikazawa Yamagishi Idbased Key Sharing

Pdf Fast Authenticated Key Establishment Protocols For Self Organizing Sensor Networks Semantic Scholar
Converting Devices To Usb Type C Youtube

Wholesale High Quality Lenovo Thinkpad Yoga 18 Laptop Buy Laptop Wholesale Laptop Thinkpad Yoga Product On Alibaba Com

Penman S Art Journal And Teachers Guide The Elblfkic Lioht Of The Wert Jvo Inshtuttoncan Guarantee To Its Patrons Better Results Ur Any Fiirth T Inforinntion You Deiire Iddre Penmans Art

Pdf A Robust Password Based Authentication Scheme For Heterogeneous Sensor Networks Semantic Scholar

P 15 Canadian Mathematical Bulletin Cambridge Core
Ppt Turbulence In Alcator C Mod And W7 As Plasmas During Confinement Transitions Powerpoint Presentation Id

Complex Number Wikipedia

19 Decide Whether Each Of The See How To Solve It At Qanda

Efficient Mobile Dynamic Id Authentication And Key Agreement Scheme Without Trusted Servers Lin 17 International Journal Of Communication Systems Wiley Online Library

Login And Authentication Phase Of Our Protocol Download Scientific Diagram
F567c Lp Ecos D Rbs4000c V3 25w Label Diagram Carta Intestata Cascina Costa Leonardo S P A

Mobiltesino Brand Design And Art Direction World Brand Design Society
Psm7a7ud Flexwave Prism Hdm 700 Lower Abc Upper C User Manual Rf Modules Installation Guide Adc Telecommunications
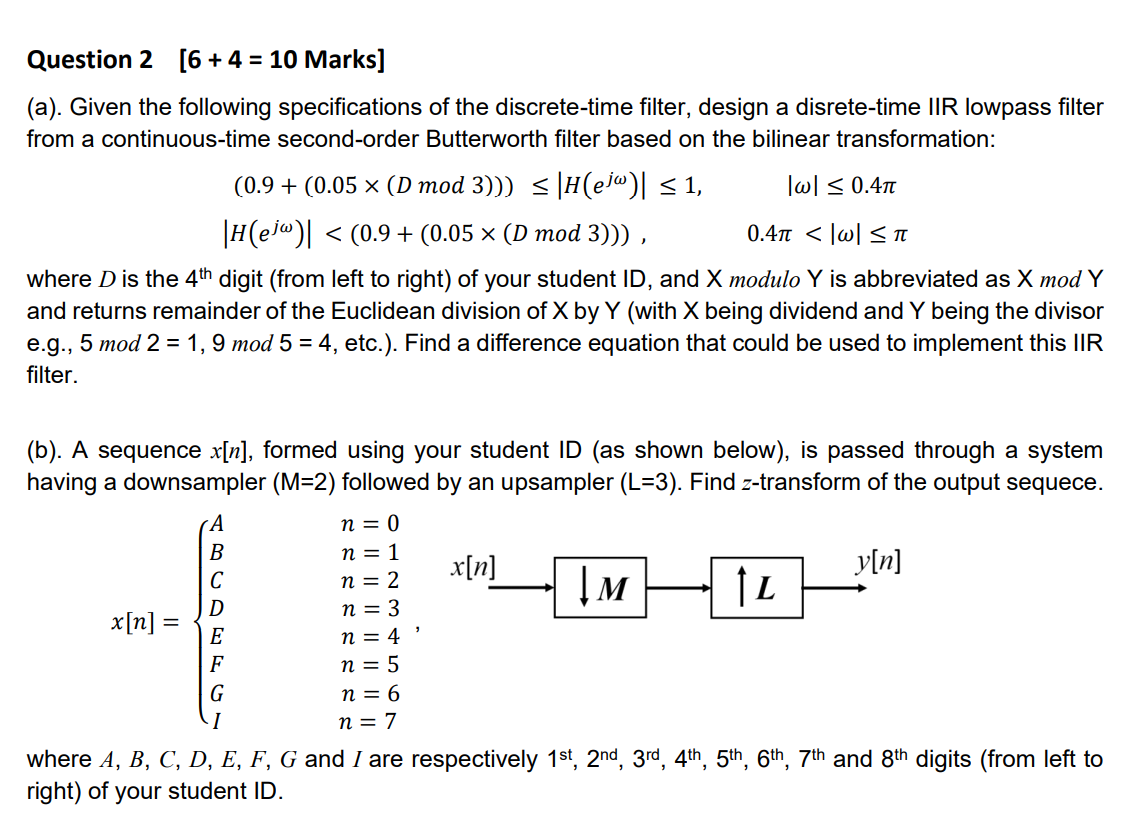
Question 2 6 4 10 Marks A Given The Follo Chegg Com
Plos One A Corpus Of Plant Disease Relations In The Biomedical Domain

Pdf Impersonation Attack On Eke Protocol Semantic Scholar

Eid Mubarak Ramadan Sofa Throw Cushion Cover Throw Pillow Case Cover Islam Decor Buy On Zoodmall Eid Mubarak Ramadan Sofa Throw Cushion Cover Throw Pillow Case Cover Islam Decor Best Prices Reviews

A Novel Lottery Protocol For Mobile Environments Sciencedirect

Cryptanalysis And Security Enhancement Of Zhu S Authentication Scheme For Telecare Medicine Information System Bin Muhaya 15 Security And Communication Networks Wiley Online Library
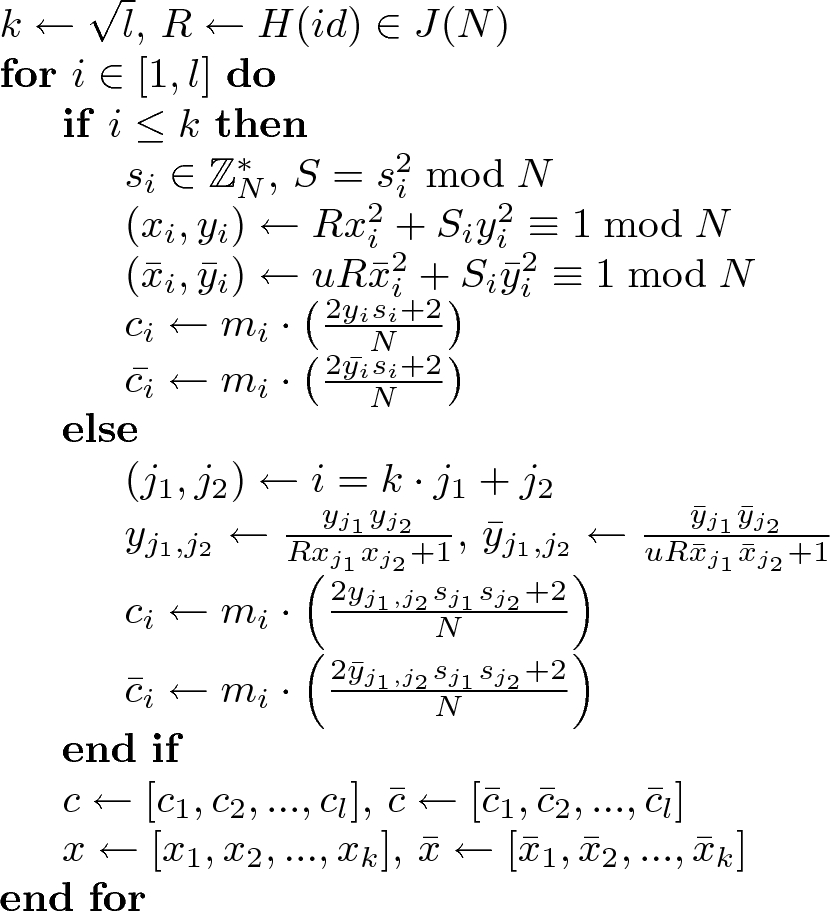
On The Security Of Jhanwar Barua Identity Based Encryption Scheme Springerlink

A Lightweight Password Based Authentication Protocol Using Smart Card Wang 17 International Journal Of Communication Systems Wiley Online Library

Aircraft N2341c 1953 Cessna 180 C N Photo By Doug Robertson Photo Id Ac
Psm7a7ud Flexwave Prism Hdm 700 Lower Abc Upper C User Manual Rf Modules Installation Guide Adc Telecommunications
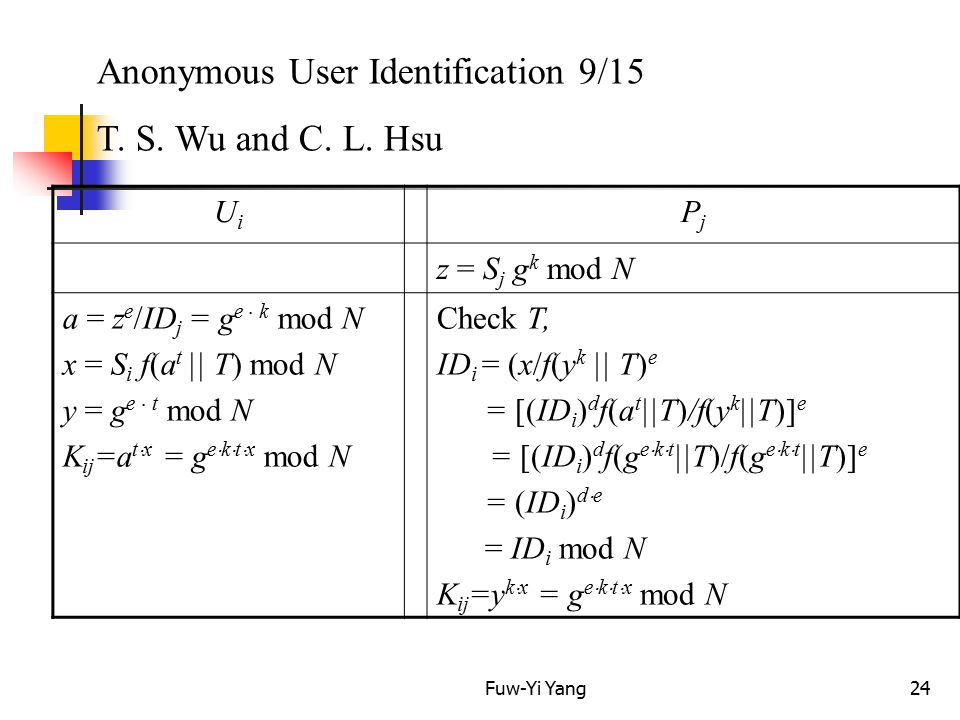
Fuw Yi Yang1 Public Key Cryptography 公開金鑰密碼department Of Computer Science And Information Engineering Chaoyang University Of Technology 朝陽科技大學資工系speaker Ppt Download

Eti Etimat 1n Installatie Automaat 1p N 16a C 6ka 1 Mod First Light

Read The Textto Answer The Qu See How To Solve It At Qanda
C Program To Encrypt And Decrypt The String Source Code
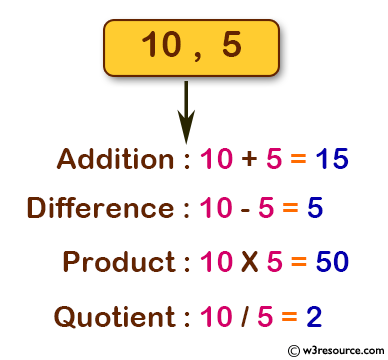
C Exercises Perform Addition Subtraction Multiplication And Division Of Two Numbers W3resource

Revised Anonymous Authentication Protocol For Adaptive Client Server Infrastructure Mahmood International Journal Of Communication Systems Wiley Online Library

Anonymous And Provably Secure Authentication Protocol Using Self Certified Cryptography For Wireless Sensor Networks Springerlink

Auditing Process Of Our Proposed Id Sepa Scheme Download Scientific Diagram

Activequiz Shortcut Links Jump To Dashbord Page Issue 56 Jhoopes Moodle Mod Activequiz Github

Resident Identity Card Wikipedia

Advisor Dr Chin Chen Chang Student Chia Chi Wu Date Jan Ppt Download




