Cn Java W
But because the certificate is for a subdomain name that's different than my server's machine (maps to the same IP address), I am getting the following error Caused by javaioIOException The https URL hostname does not match the Common Name.
Cn java w. The cin is a predefined object of istream class It is connected with the standard input device, which is usually a keyboard The cin is used in conjunction with stream extraction operator (>>) to read the input from a console Let's see the simple example of standard input stream (cin) #include More ›. Free Java Projects There are given a lot of free java projects developed in core java, servlet, jsp, struts, spring and hibernate technology We are providing all the projects for student purpose. View Muralidharan CN’s profile on LinkedIn, the world’s largest professional community Muralidharan has 1 job listed on their profile See the complete profile on LinkedIn and discover Muralidharan’s connections and jobs at similar companies.
0601 · Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability does not apply to Java deployments, typically in servers, that load and run only. Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability can also be exploited by using APIs in the specified Component, eg, through a web. Note Applies to client and server deployment of Java This vulnerability can be exploited through sandboxed Java Web Start applications and sandboxed Java applets It can also be exploited by supplying data to APIs in the specified Component without using sandboxed Java Web Start applications or sandboxed Java applets, such as through a web.
· Here’s a simple Java HTTPS client to demonstrate the use of URLConnection class to send a HTTP GET request yo get the https URL content and certificate detail PS You may interest at this example – automate login a website with URLConnection. · JRex is a Java Web browser component with a set ofAPIs for embedding the Mozilla Gecko engine withina Java application mehr Info. 1310 · Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability does not apply to Java deployments, typically in servers, that load and run only.
Configuring the Director Of all the configuration files needed to run Bacula, the Director's is the most complicated, and the one that you will need to modify the most often as you add clients or modify the FileSets For a general discussion of configuration files and resources including the data types recognized by BaculaPlease see the ConfigurationConfigureChapter chapter of this manual. · Java Web Basic;. · In this article In the world of microservices, every logical operation requires work to be done in various components of the service You can monitor each of these components separately by using Application InsightsApplication Insights supports distributed telemetry correlation, which you use to detect which component is responsible for failures or performance.
Let's dive right into the basics of AWS so that you get a quick overview over what AWS actually is and what you can do with itJoin the full AWS Serverless c. Desktop (Java Platform SE 8 ) javalangObject javaawtDesktop public class Desktop extends Object The Desktop class allows a Java application to launch associated applications registered on the native desktop to handle a URI or a file Supported operations include launching the userdefault browser to show a specified URI;. · Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability can also be exploited by using APIs in the specified Component, eg, through a.
Write a program that replaces each line of a file with its reverse. 1 Overview In this. · C is a compiled language that is it converts the code into machine language so that it could be understood by the machine or system Java is an Interpreted language that is in Java, the code is first transformed into bytecode and that bytecode.
· Java Multiple Choice Questions And Answers 21 Here Coding compiler sharing a list of 60 core java and advanced java multiple choice questions and answers for freshers and experienced These java multiple choice interview questions asked in various java interview exams We hope this list of java mcq questions will help you to crack your next java mcq online test. · Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability does not apply to Java deployments, typically in servers, that load and run only. 1504 · Note Applies to client and server deployment of Java This vulnerability can be exploited through sandboxed Java Web Start applications and sandboxed Java applets It can also be exploited by supplying data to APIs in the specified Component without using sandboxed Java Web Start applications or sandboxed Java applets, such as through a web.
Text Form of Oracle Critical Patch Update April Risk Matrices This document provides the text form of the CPUApr Advisory Risk Matrices. 1504 · This vulnerability can be exploited through sandboxed Java Web Start applications and sandboxed Java applets It can also be exploited by supplying data to APIs in the specified Component without using sandboxed Java Web Start applications or sandboxed Java applets, such as through a web service CVSS 30 Base Score 37 (Availability impacts) CVSS Vector (CVSS30/AVN/ACH/PRN/UIN/SU/CN. Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability can also be exploited by using APIs in the specified Component, eg, through a web.
· Here's another vote for JMeter JMeter is an opensource load testing tool, written in Java It's capable of testing a number of different server types (for example, web, web services, database, just about anything that uses requests basically). View N C N PRASAD KOTI’S profile on LinkedIn, the world’s largest professional community N C N PRASAD has 4 jobs listed on their profile See the complete profile on LinkedIn and discover N C N PRASAD’S connections and jobs at similar companies. 2 Example 21 pomxml;.
Java SE Embedded 8u261. Was this post helpful?. · Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability does not apply to Java deployments, typically in servers, that load and run only.
· Microservices are an architectural solution for designing complex software by breaking it into small independently deployable modular servicesIt is often contrasted with the traditional monolithic architecture where software is built as a single unit. He is Master of Computer Applications with expertise in Java , Web Technologies, Computer Network (CCNA) , Digital Marketing & Cyber Security MrAnand is presently working as an Assistant Professor at Computer Science & Engineering Department in Allenhouse Colleges , Rooma , Kanpur Previously worked as an Assistant Professor in Maharana Pratap Engineering College ,. · Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability does not apply to Java deployments, typically in servers, that load and run only.
· The Arduino sketch must change % in the text back to spaces Processing the String in the Arduino Sketch The function GetText() is used to get the text box string from the incoming HTTP GET request The HTTP_req array holds the beginning of the incoming GET request as shown in the above image — starting with GET /ajax_inputs&txt The GetText() function first. · To access the values embedded within the data query string parameter value, in your webpage web resource you can extract the value of the data parameter and then use code to split the string into an array so you can access each name value pair individually When the page loads the getDataParam function is called. This vulnerability can be exploited through sandboxed Java Web Start applications and sandboxed Java applets It can also be exploited by supplying data to APIs in the specified Component without using sandboxed Java Web Start applications or sandboxed Java applets, such as through a web service CVSS 30 Base Score 37 (Availability impacts) CVSS Vector (CVSS30/AVN/ACH/PRN/UIN/SU/CN.
· Note This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets (in Java SE 8), that load and run untrusted code (eg, code that comes from the internet) and rely on the Java sandbox for security This vulnerability can also be exploited by using APIs in the specified Component, eg, through a. Spring boot cloud eureka client example January 6, 18 Spring Boot No Comments Java Developer Zone Table of Contents 1 Overview;. 0101 · (2) Operational feasibility T e system is based on the Windows ti g system, the entire system int rface is simple and uncomplicated, with good interactivity, users can find their own needs at a glance6 The requirements for the operator are very low, and t e user c n q ickly and proficiently operate according to the prompts (3) Ec nomic feasibility The software used in this.
Laravel, Angular, Node JS, ionic, CodeIgniter, Python, HTML, CSS, PHP, jQuery, and Java Web Design Programming Video and Animation Video and animation services that will bring your brand to life studio quality presentations that will speak to your customers eBook Design & Writing Ebooks could be written about nearly all subject, for just about any niche Logo Design Get. Well organized and easy to understand Web building tutorials with lots of examples of how to use HTML, CSS, JavaScript, SQL, Python, PHP, Bootstrap, Java, XML and more. 2110 · CVE Published 21 October Vulnerability in the Java SE, Java SE Embedded product of Oracle Java SE (component Serialization) Supported versions that are affected are Java SE 7u271, 8u261, 1108 and 15;.
The Java Virtual Machine dynamically loads, links and initializes classes and interfaces Loading is the process of finding the binary representation of a class or interface type with a particular name and creatinga class or interface from that binary representation. Answer (a) Bytecode is executed by the JVM Explanation The output of the Java compiler is bytecode, which leads to the security and portability of the Java code It is a highly developed set of instructions that are designed to be executed by the Java runtime system known as. Text Form of Oracle Critical Patch Update October Risk Matrices This document provides the text form of the CPUOct Advisory Risk Matrices.
· Here is a simplest Java Program to read a file line by line in reverse order using Java8 APIs Try it out and let me know if you see any issue with this java program to reverse the contents of a file;. Java is a highlevel object oriented programming language and some users may find it tough However, these sets of programs will make you comfortable with the Java programming language and its basic concepts You will see a set of programs mentioned below that ranges from a simple “hello world” application to searching for a number.

Beginning Jsp Jsf And Tomcat Web Development
Matlab Function Reference Volume 2 F Manualzz
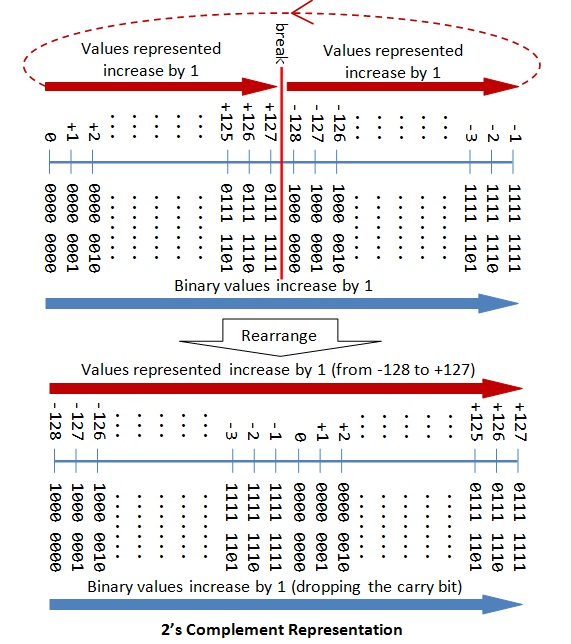
A Tutorial On Data Representation Integers Floating Point Numbers And Characters
Cn Java W のギャラリー

Language Detection Using Neural Network Java Developer Zone
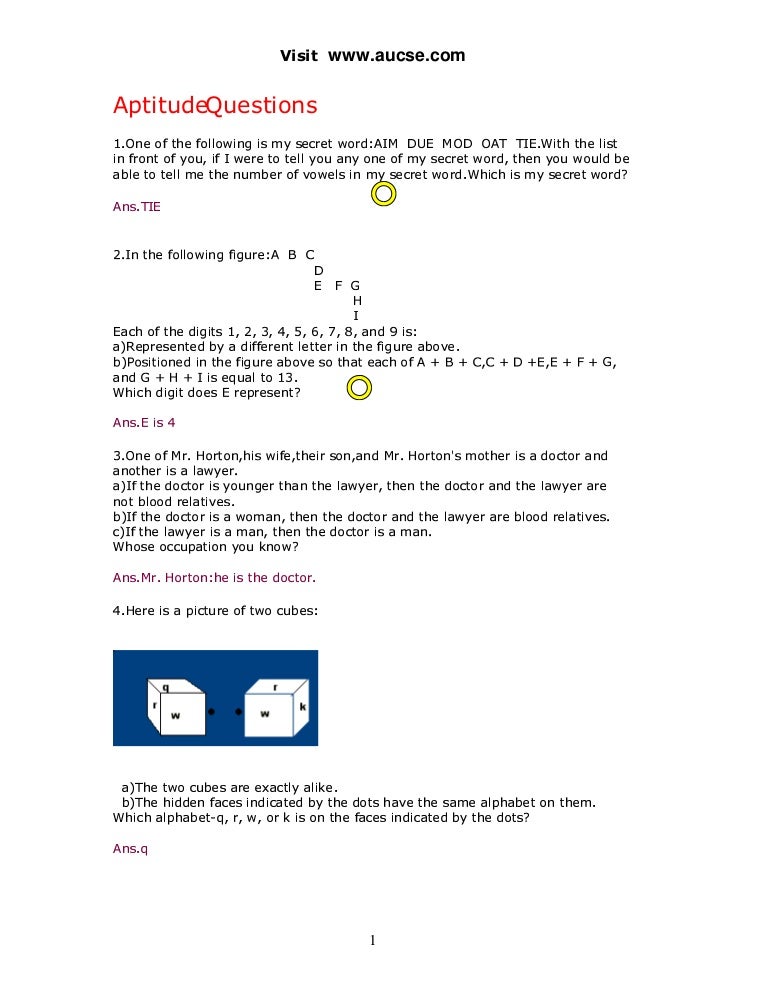
Aptitude

Object Oriented Circuit Generators In Java Of Kolja Sulimma

Pdf A Real Time Garbage Collector With Low Overhead And Consistent Utilization

Pdf C C Java Python Php Javascript And Linux For Beginners Manjunath R Academia Edu

Open Programmable Architecture For Java Enabled Network Devices

Difference Between Compiler And Interpreter With Respect To Jvm Java Virtual Machine And Pvm Python Virtual Machine By Rahul Saini Medium
Flipdot Github

Final Review What You Learned This Semester Cmsc 131 Docsity

Using Objects And Patterns To Implement Domain Ontologies

Using Objects And Patterns To Implement Domain Ontologies
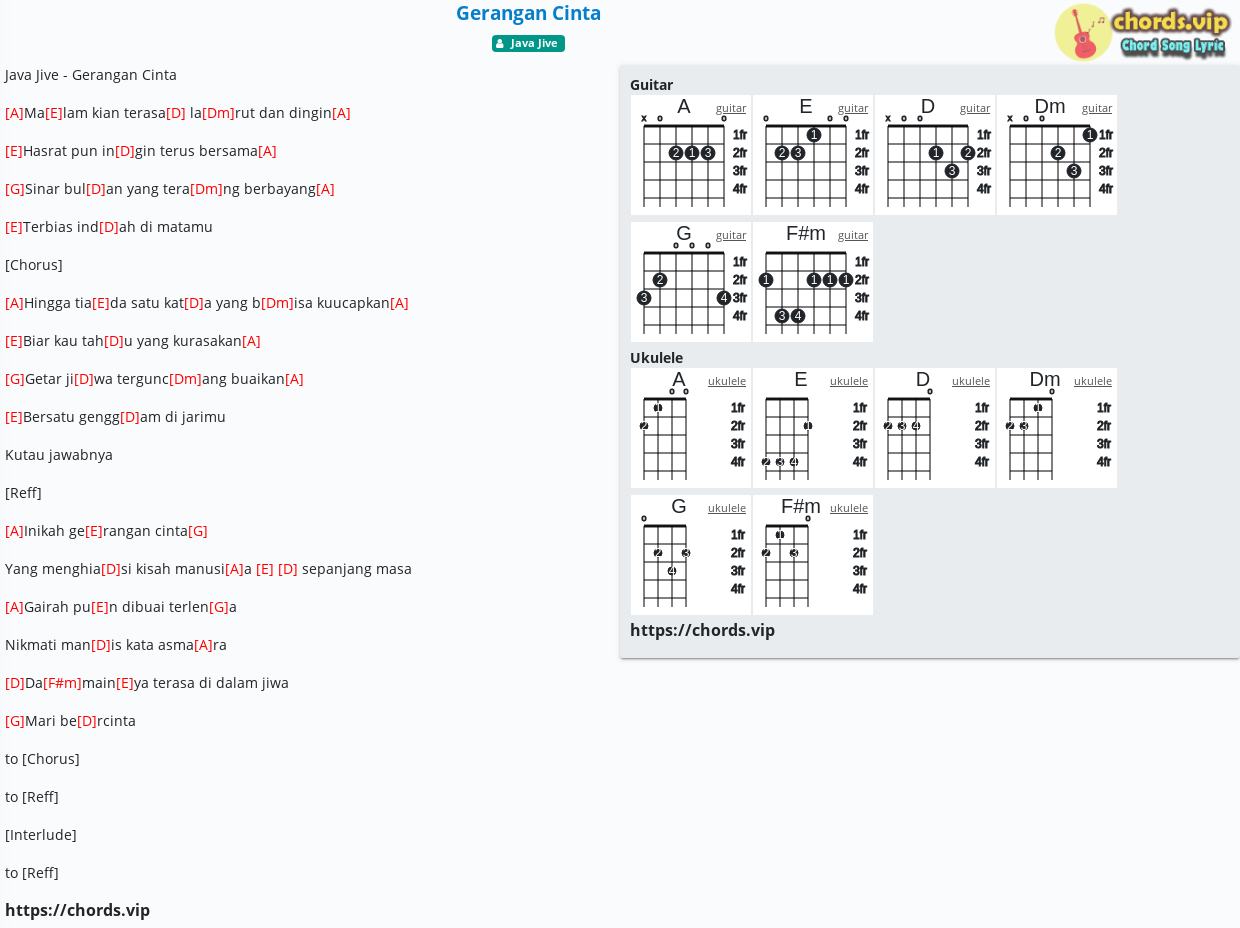
Chord Gerangan Cinta Java Jive Tab Song Lyric Sheet Guitar Ukulele Chords Vip

Y Latin Capital Letter Y With Acute U 00dd Graphemica

Pdf Implementing Influence Analysis Using Parameterised Boolean Equation Systems

Java

Alias Analysis For Java Design And Evaluation Georgia Institute Of

Sum Of Products Reduction Using Karnaugh Map Boolean Algebra Dyclassroom Have Fun Learning

Volley String Request Returns Random Character Stack Overflow

Pdf Object Oriented Programming And Data Structures Dylan Mars Academia Edu
Cs 61b Part 6 Hashing Pqs And Heaps Forkercat Blog

Java Servlet Programming 1998 80kb Feb 19 12 03 33 51 Pm Manualzz

Sum Of Products Reduction Using Karnaugh Map Boolean Algebra Dyclassroom Have Fun Learning
Peb Yhyt7jbifm
Ppt Pdf 1 5 Powerpoint Presentation Free Download Id

Pdf C C Java Python Php Javascript And Linux For Beginners Manjunath R Academia Edu
A Tutorial On Data Representation Integers Floating Point Numbers And Characters

Using Objects And Patterns To Implement Domain Ontologies

Cs440 540
Github Aspose Ocr Aspose Ocr For Java Aspose Ocr For Java Examples And Sample Projects

Aptitude

Java Javascript123uo00es0270 Pdf Html Cascading Style Sheets
Download Font Awesome Java
A Tutorial On Data Representation Integers Floating Point Numbers And Characters
Cs 61b Part 6 Hashing Pqs And Heaps Forkercat Blog
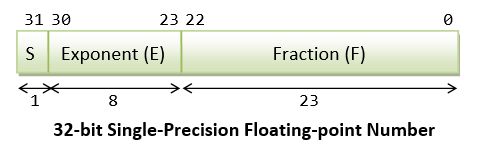
A Tutorial On Data Representation Integers Floating Point Numbers And Characters

Como Programar A Java 2 Pdf

Solved Skills Loops Else Statements Random Numbers Cumulative Sum Printf Statements Optional Wr Q

Iso Iec 59 1 Wikipedia
Pdf A Real Time Garbage Collector With Low Overhead And Consistent Utilization
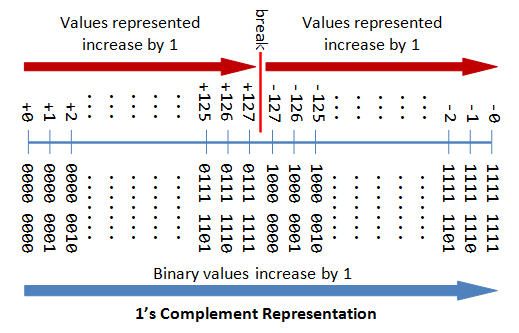
A Tutorial On Data Representation Integers Floating Point Numbers And Characters
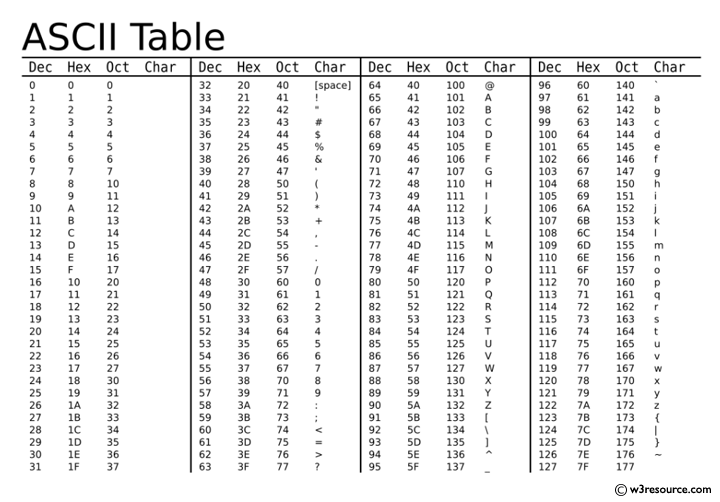
Python Get The Ascii Value Of A Character W3resource

Awesome Java Font Free Download Similar Fonts Fontget

Q 2 3 Simplify The Following Boolean Expressions To Minimum Number Of Literals A Abc A B Abc Youtube
Cloudhopper Commons Gsmcharset Java At Master Twitter Cloudhopper Commons Github

Arrays In Java Exercise 5 Youtube
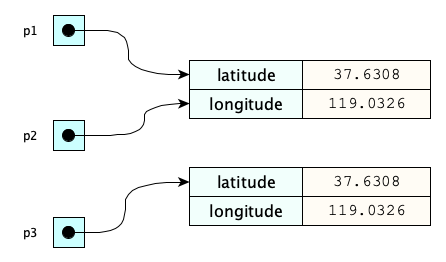
Java Basics

Bakiyanathan Java In Tamil தம ழ ல ஜ வ

Alias Analysis For Java Design And Evaluation Georgia Institute Of

Using Objects And Patterns To Implement Domain Ontologies

Java Text Areas Of Computer Science
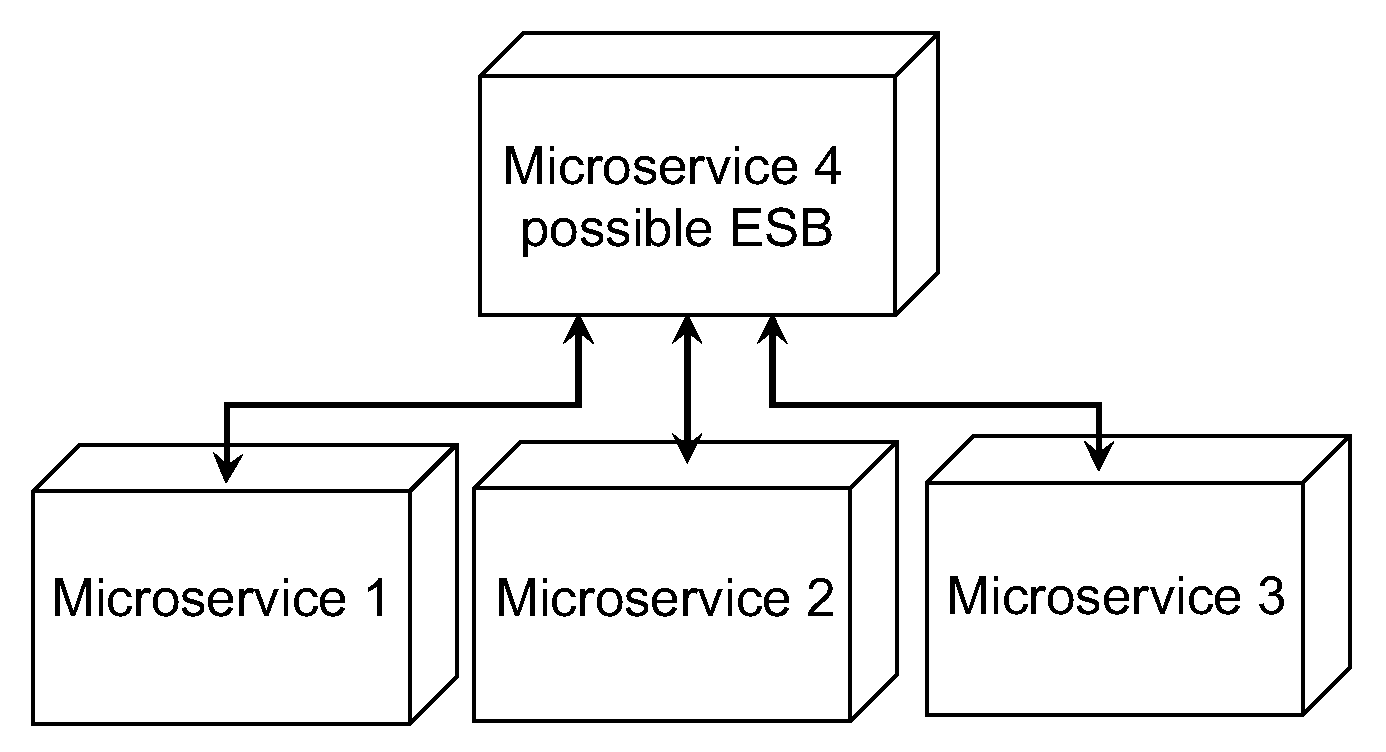
Applied Sciences Free Full Text Automated Code Smell Detection In Microservices Through Static Analysis A Case Study Html

0 1 2 3 9 A8b C 9 D E Fg 6hpi Q R6sut Manualzz
Manual

Object Oriented Circuit Generators In Java Of Kolja Sulimma

Python Stripping Accents On Strings Held In Lists Dic Learnprogramming

Design Overview

Java

Longest Path In A Directed Acyclic Graph Geeksforgeeks

Mojibake Wikipedia

Character Classes In Regular Expressions A Gentle Introduction

Accurate And Fast Sun Moon Ephemerides Suitable For Android And Ios Projects

Using Objects And Patterns To Implement Domain Ontologies

Pdf Operational Pnml Towards A Pnml Support For Model Construction And Modification Luis Gomes Academia Edu

Using Objects And Patterns To Implement Domain Ontologies

Difference Between Compiler And Interpreter With Respect To Jvm Java Virtual Machine And Pvm Python Virtual Machine By Rahul Saini Medium
Pdf A Three Phase Approach To Efficiently Transform C Into Kdm
Glazedlists Latindiacriticsstripper Java At Master Glazedlists Glazedlists Github
Learnopengl Text Rendering
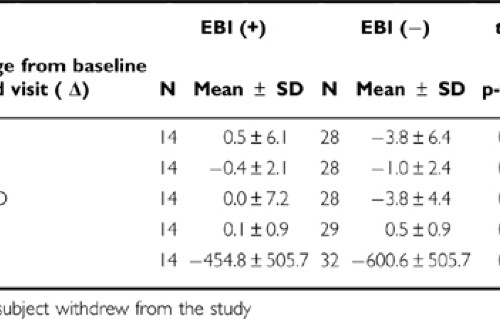
Poster Session Iii Neuropsychopharmacology

Page 2 C 4r High Resolution Stock Photography And Images Alamy
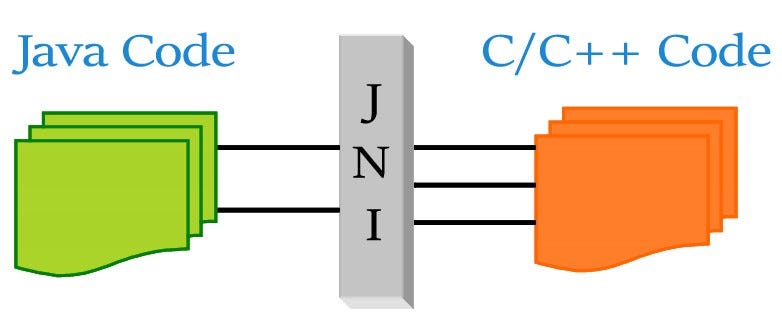
Introduction To Java Native Interface Establishing A Bridge Between Java And C C By Yigit Pirildak The Startup Medium

Java




