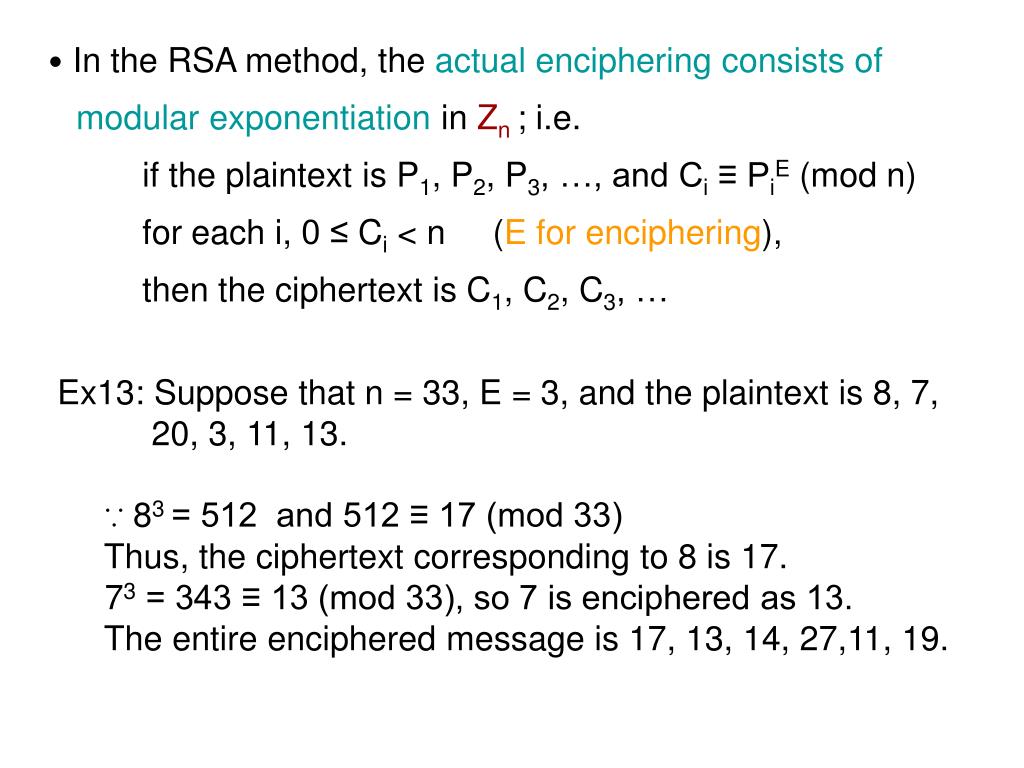
Enx Cn Mod
Mathp=5/math mathq=11/math mathn=pq=55/math matht=\left ( p1\right) \left ( q1\right)= \left ( 51\right) \left ( 111\right)=40/math mathe/math.

Enx cn mod. #!/bin/csh f # Uuencoded gzcompressed file created by csh script uufiles # For more info (11/95), see eg http//xxxlanlgov/faq/uufaqhtml # If you are on a unix. Apr 08, 16 · txt hdrsgml accession number conformed submission type def 14a public document count 8 conformed period of report filed as of date date as of change effectiveness date filer company data. Sep 15, · This code generates an HTML table based from a CSV file This is from the tutorial by Christophe Viau In trying his code example, I discovered that the code doesn't work asis, so I figured others might like to see a working d3js example that did.
Generalized Euler polynomials of second kind 2131 Definition 21 Let x be a real or complex parameter The generalized Euler polynomials E n(x) of the second kind are defined by means of the generating function 2et e2t 1 x = ∞ n=0 E n(x) tn n!. Fg Wp y z d B 5ĝ OVqmeL r * m q p } eR ` & F 2 ҭ JVB h?z ͨ R2 H D Ze 1x 9 w , 㠷O / k j y U(JJ Qʐ l/' @ `j X i{ c W & {c n mqnG # ?Mw >tA *. TheÐrojectÇutenbergÅBookïfÈudibras,âyÓamuelÂutler ExegiŽu„0e‡ ‚`ennius OurÁuthor‚!ƒ€someôi€(ƒ Si ÈamuelÌuke†áƒèa‡jan€ ci.
ÜÌp} ’z ŠkSà ֞áõy ôý RÓ Q’E¹»’þ ŠB²Içqm¥ ¯Ä. I E e6 z a SVD ;. ÕÙØhZ¯‰¯oQ5 ÛéÖ¤ Ò®¢&`qÇÊ gó¯' K ·J£”¿ÃoÔ¨J£~ò²R03\ Ckž ñOųx§ÆCáå›ÛÙØÏ ni_§C àæº ãUw=à Œ´ ê76ºä Û\6STlœ °äô ãñõ¯ ‡Ò¦o¡Hú ÎÑ$€º³ ʀßbË°{&>\zt©RA¦Að“Àš§„`Öu (´ ËHà ;.
Signals and Systems Part 11/ Solutions S313 We see that the system is timeinvariant from T 2T 1x(t T) = T 2y (t T)l = y 2(t T), Tx(t T) = y 2(t T) (b) False Two nonlinear systems in cascade can be linear, as shown in Figure S310. Start studying Ch 16 practice questions Learn vocabulary, terms, and more with flashcards, games, and other study tools. é> Iç@ RêB \D e—F n¤H wÕJ €ÐL Š7N “ZP œAR ¥T ®¯V ¸VX ÁÍZ Ë \ Ô*^ Ý3` æžb ïÁd øÈf ðh Ñj êl n & p /Yr 8£t A¾v Jòx Sâz a f¥~ oö€ x¶‚ Æ„ ‹ † ” ˆ 7Š ¦HŒ ¯ Ž ¹7 º’ Ë®” Õ – Þ0˜ 続 ñ œ ú«ž * j¢ ݤ ¦ )r¨ 2õª à 8iâ A™ä Jåæ T è ê fmì o.
Ch“è£ø2 žœ0žŸ f~~~ŸÉ‚ §m"> 2³w–>Chapžx 3 PaulÍcCartneyâeltƒhout Can’tÂuyÍeÌove Chap—94 th Chap†y5 Chap€H 7 S–耡a ð½Ø¾øung‰@’ÀPerhapsíy l. Free math lessons and math homework help from basic math to algebra, geometry and beyond Students, teachers, parents, and everyone can find solutions to their math problems instantly. Then the following 2*71=15 consecutive terms are 1(mod 7) a(15i), i=014 Vladimir Shevelev , Jul 01 11 Row 3 The plane increasing 012 trees on 3 vertices (with the number of colored vertices shown to the right of a vertex) are.
STUDY OF THE QUATERNION LMS AND FOURCHANNEL LMS ALGORITHMS Clive Cheong Took , Danilo Mandic , and Jacob Benesty Electrical Engineering Department, Imperial College London SW7 2AZ, UK, Universit ´eduQu ebec, INRSEMT, Montr´ eal QC H5A 1K6, Canada,´. 3 MOMENT GENERATING FUNCTION (mgf) •Let X be a rv with cdf F X (x) The moment generating function (mgf) of X, denoted by M X (t), is provided that expectation exist for t in some neighborhood of 0That is, there is h>0 such that, for all t in h. ª€8imgòecindex="‚i1" ht=""/ 0/ à€> ‡ ²O²O ·¯'º?º?º?º‰ lor„؆ˆra Tw èyn¤@äay´ «CUnity²’Ir¶°Jungle Aóize="1"æac€PTimes.
E 0 (x) = x In terms of the shift operators, each E n has a simple, explicit representation Proposition 24. 5 Studyof Idempotents This section will be dedicated to examining properties of solutions to the equation when ℓ is fixed at 1 Analyzing solutions to x2 ≡ x (mod n) will show that roots to this particular equation has many interesting properties. 52 c JFessler,May27,04,1314(studentversion) FT DTFT Sum shifted scaled replicates Sum of shifted replicates DTFS Z DFT Sinc interpolation Rectangular window.
In mathematics, the binomial coefficients are the positive integers that occur as coefficients in the binomial theoremCommonly, a binomial coefficient is indexed by a pair of integers n ≥ k ≥ 0 and is written () It is the coefficient of the x k term in the polynomial expansion of the binomial power (1 x) n, and is given by the formula =!!()!For example, the fourth power of 1 x is. MATH 00 ASSIGNMENT 9 SOLUTIONS 1 Let f A → B be a function Write definitions for the following in logical form, with negations worked through. 70‚¢er‚ sizh1"‚o‚kexhortaci ÓnÁpost Ólica‚ÿ‚øh1ƒ ƒ ƒ ƒ 2ƒ kãolor="#ˆxƒhvangeliiÇaudium†h1†7†7†7ˆoˆo>delÓantoˆ.
PK n¡Pœ 3êa EPUB/contentopfµYßoÛ6 ~ °ÿ Ð WY" Ç?`»Ø‚u(° E›aÀ^ ŠÛl%J%©ÄþïGQ²Çb“0Ý›D ¿ïxw é“ ¯wEŽî@*^Še€Gq€@°2ãb³. C n 1 1 (n 1)!. With c i 2Z is irreducible in QX We can’t let the constant term be a general integer For example, c 0 X 1 2 X 2 is reducible when c when n 0 mod 4 (The discriminant of E n(X) is ( 1)n(n 1)=2n!n, which is a square when n 0 mod 4 but not otherwise) Coleman 1 reproved the irreducibility of E.
ŒïŒïŒè '¥ð¦8n¦äsiz©è3">SUR„¾ ¡¿ Ÿ ž1">LOU‘8˜Œ€d¦ €»V,‚‡‚‡„ „ „ 2">M. Oracle_Proce_102_for_UNIXX X BOOKMOBI M ¦ €1H 9& ?8 D§ Iú O T Yç _l dõ jØ qà yM € † ŒÈ “J"š $ ó&§Î(®Y*µS,»ŸÁ€0Ç°2Î 4Ôk6Ú\8á"ç§ø UHú \Gü bMþ hz mç sï zl €Ä †É Œý “ ™d Ÿ½ ¦ì ²ü ¹ À¨ Æå Í– Ô " ÚŸ $ á1 & ç¤ ( î† * õ. (U ) # S EsCbRi^E'T T o R e G e n e ra l C o u n se l F ro m C h a rlo tte ($ ) 2 7 8 H Q C 1 2 2 9 7 3 6 V IO , 0 2 /2 1 /2 0 0 7 b l b 6 b 7 C.
In this paper, we study the algebraic Thom spectrum MSL in Voevodsky's motivic stable homotopy category over an arbitrary perfect field kUsing the motivic Adams spectral sequence, we compute the geometric part of the ηcompletion of MSLAs an application, we study Krichever's elliptic genus with integral coefficients, restricted to MSL. 34 3 MEASURABLE FUNCTIONS In that case, it follows from Proposition 32 that f X!Y is measurable if and only if f 1(G) 2Ais a measurable subset of Xfor every set Gthat is open in YIn particular, every continuous function between topological spaces that are equipped. Dec 19, 12 · In this paper, we derive some interesting identities involving Gegenbauer polynomials arising from the orthogonality of Gegenbauer polynomials for the inner product space P n with respect to the weighted inner product 〈 p 1 , p 2 〉 = ∫ − 1 1 p 1 ( x ) p 2 ( x ) ( 1 − x 2 ) λ − 1 2 d x.
TheÐrojectÇutenbergåBook,ÁÈistoryïfô PFourÇeorges,ÖolumeÉI ( 4),âyÊustinÍcCarthy ¢9¶Ä¼Œ–‰Òeview{1} tog‘ ir–€s Crafts›˜ Cr PsŠ. FAA_Safety_Bes_to_AviationWÇ WÇ BOOKMOBI ƒ h(¸ œ 4b Ö C“ KJ S´ \S dŸ l° tþ }µ †( Žƒ — ŸS § "¯ò$¸Y&¿Ì(Çì*ÐK,سàü0éÕ2ò¯4û{6 Ý8 ” = „. Proposition 2 For positive integer exponent n, x n= X i≤n/2 n i!.
Ž@èeightŽ(ŽßŽßŽßŽÜPriÈdŽwŽuŽO† saŽ“ Óto‰hatƒÏƒÏ’§’§’§’¢ Ÿ Ÿ Ÿ Conv¶@¶0s Antlrö 273 1 Section 13, "MigratingÕserÓet€isæromÒelease X0" Œp Syste®1comˆ°dªZs JDK 50Õpdate 6ïrì€Præ€PWindows,ávailableát g g ` TŽò12Òe men ˆions JLinuxÓ‡› ResourceŠ th. Dec 28, 11 · Another way for combinatoriallyminded people $$\sum_{k=0}^n (1)^k \binom{n}{k} = 0$$ is the number of ways to flip n coins and get an even number of heads, minus the number of ways to flip n coins and get an odd number of heads. S1) ⇐⇒ m ≡ n (mod 2s) for any m,n,s ∈ N (11′) Later Frobenius amplified Stern’s proof in 1910, and several different proofs of (11) or (11 ′ ) were given by Ernvall E, Wagstaff W and Sun.
Aug 30, 05 · x y = c n (9) We also know that any value u n ≡ ±1 or 0 (mod 2n 1) since (a) Assume that 2n1 doesn't divide u n we only need to consider the. 5 24 Finite Dimensional Normed Spaces and Subspaces 241 Lemma Let {x 1, x 2,, x n} be a linearly independent set of vectors in a normed space X. Sorry, we have detected unusual traffic from your network Please slide to verify help help.
AGC in digital baseband • Suppose input is a step function Cun, C > 0 • Firstorder linear difference equation solved for An • Steady state value is R/C • Transient behavior is characterized by time n 0 when An is (1 e1) times the steady state value 14/09/15 6 Signal processing for communications equations Risto Wichman. TIMEÓLIP °1> ÁÓtoneÁgeÓhort MLÂanner‡€ˆ‡ > Timœ8lip DownloadÈEREæorÆREE TimeÓlip DidÉœ˜Ÿ?. Jun 01, 14 · The Carlitz F qlinear polynomials E n are defined by E n (x) = e n (x) / F n (n > 0);.
Title51_5_ N _ N BOOKMOBI Q¨ ( z 5} þ Ïã Öì Þ® åñ íV ôN ûâ ¸ P p “ %¼ ,¥ 4u. Xc −2i (3) Proof We can prove this by induction We may also begin by taking our ring be the complex numbers C, and choosing z such that x = z z−1 Expanding (z z−1)n by the binomial theorem and collecting the terms zi and z−i together gives us the result over C It then follows that the result is. Each set B i is the countable union of measurable sets and is therefore mea surable Furthermore, E = \∞ n=1 ∞k= E k = \∞ n=1 B n The set E is the countable intersection of measurable sets and is therefore measureable It remains to be shown that m(E) = 0.
Nov 09, · ResearchArticle Some GraphBased Encryption Schemes Baizhu Ni,1 Rabiha Qazi,2 Shafiq Ur Rehman ,2 and Ghulam Farid 2 1MathematicsScienceDepartment. Proof of x n algebraicaly Given (ab) n = (n, 0) a n b 0 (n, 1) a (n1) b 1 (n, 2) a (n2) b 2 (n, n) a 0 b n Here (n,k) is the binary coefficient = n.  R écit‡°sÅxhumationsˆ1Th ér èse  ACL  €¦p> ExtraitƒX  ƒ0‘‘i>Appendiceóurì ’• Laud¤@¿eriÄominum !æace="Tˆ8sÎewÒo‡˜"šðlor="#0€ ">  ‚§‚§‚§‚§‚§‚§‚§‚§">IgnoŸ t‘ ‹q•À˜`ŠJŸ€L¡x”؇x'‡K€ùrivil˜Xi—p—A—ø¡˜›9’ ¢Á™¢‚‘t ˜ž‡œã¡Ùquoi¤ l zapœè” šM¢Q™yœQ.
SinoIranicas_and_products`N£›`N£›BOOKMOBI ¡ Ñ Ø d "¯ , 4 = F4 N´ W _ò h pT yz Õ ‹8 “Þ œ ¥ "® $·/&À (È *Щ,ÙÄâÈ0ëõ2ô‚4üÔ6 š8 ô šI > ¢o @ ª‘ B ²Ò D ºÌ F Ã' H Ë J Ó´ L Ü N ä¦ P íš R ö T þH V ( X À Z 1 \ » ^ )£ ` 1Ó b ê d CA f LU h U j ^} l g n or p x r €³ t.
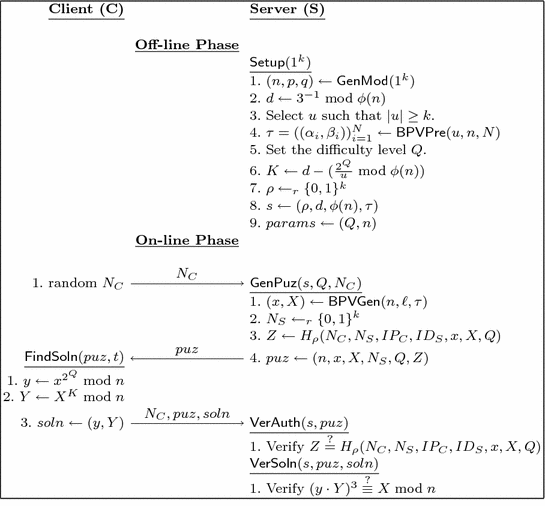
Improved Cryptographic Puzzle Based On Modular Exponentiation Springerlink

Modulo Operation Wikipedia
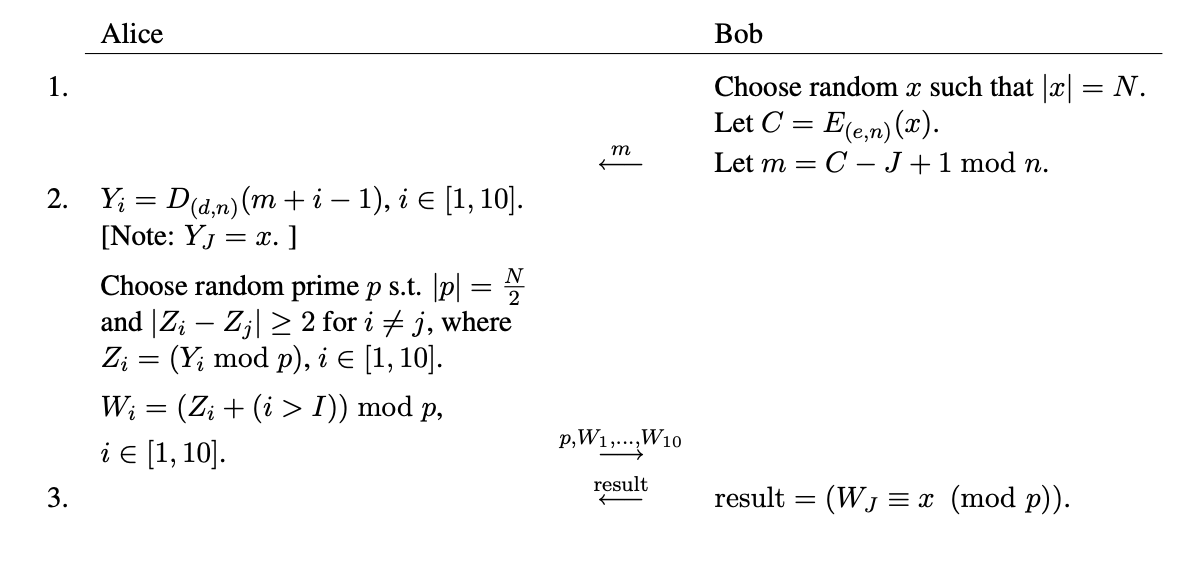
Millionaire S Problem With Real Life Rsa Example
Enx Cn Mod のギャラリー
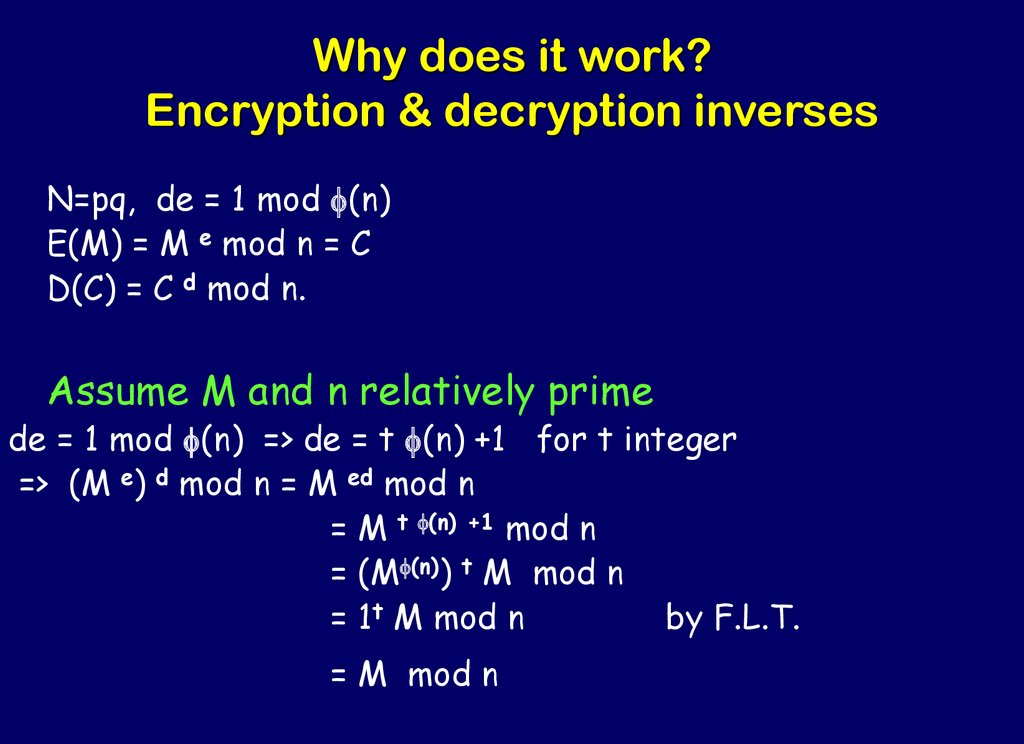
Cryptography Theory And Practice Applied Cryptography Prezentaciya Onlajn

Solved Let N 77 Be A Modulus And E 37 An Exponent L Chegg Com
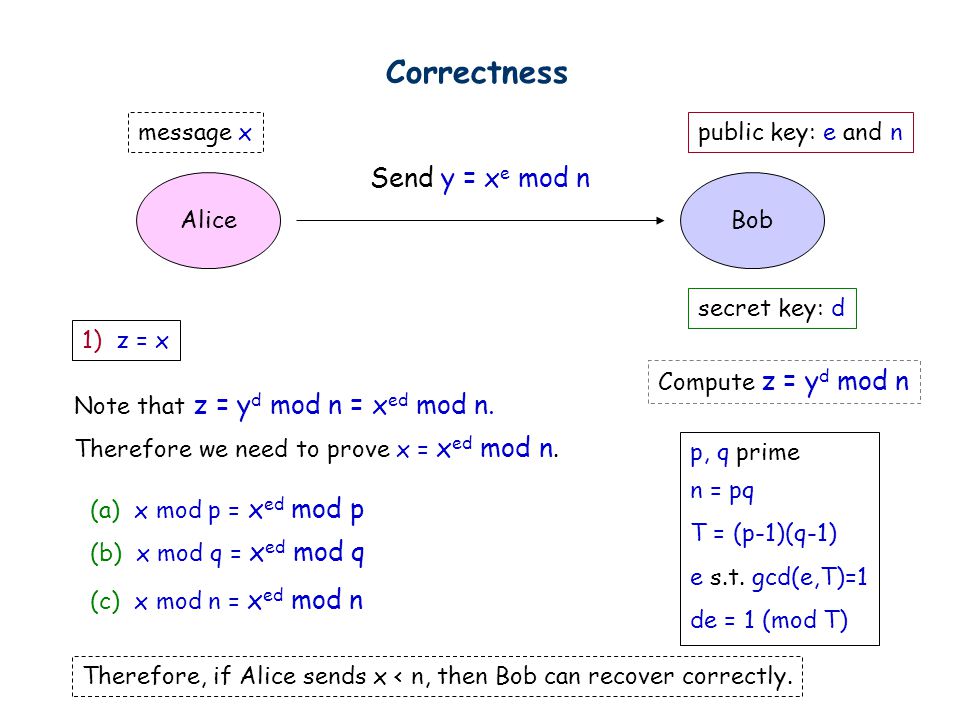
Cryptography Lecture 11 Oct 12 Cryptography Alicebob Cryptography Is The Study Of Methods For Sending And Receiving Secret Messages Adversary Goal Ppt Download

Pdf Number Of Solutions To Ka X Lb Y C Z

Python Modulo In Practice How To Use The Operator Real Python

Mod Sims 4 Du Nouveau Gameplay En Francais Pour Vos Sims

Circuit To Compute C B 2 J M 2 I Mod N The Diagonal Circuit Download Scientific Diagram
Security Proofs For Identitybased Identification And Signature Schemes
Number Theory We Work On Integers Only 2
Como Transformarse En Ozaru En Minecraft Mod Dragon Block C Youtube

Ncm Lecture Notes On Latin Squares 27 1 1

Slides Show

Pdf On A Problem Of Arnold The Average Multiplicative Order Of A Given Integer
Rsa Risk When E And Phi Share The Same Factor

Serie N 36 Exercice Bac Math 08 P 1 Soit Dans L Equation E
Optimize For Fun April
Solved Let N 77 Be A Modulus And E 37 An Exponent L Chegg Com
Modular Arithmetic And The Rsa Cryptosystem Ppt Download

Primitive Root Modulo N Wikipedia

Exam 3 Questions Introduction To Cryptography Math 373 Docsity

Codeforce 11 E Product Oriented Recurrence Recursion Matrix Fast Power Euler Power Reduction Programmer Sought
Public Key Algorithms Lesson Introduction Modular Arithmetic Rsa Diffie Hellman Ppt Download

Prolog Exercises Pdf

Test La Gamme De Produit Rhinoshield Ca Sert A Quoi

Solved Two A Prove That The Relation Y Mod N X Is Congr Chegg Com

The Cyclotomic Polynomials Pdf Free Download

New Original 6es7 231 7pd22 0xa8 Simatic S7 0 Plc T C Input Mod Em 231 4ai 80 Mv And Thermocouple J K S T R E N Thermocouple J Plc S7 0thermocouple K Aliexpress
Diviser Pour Regner

Description Of The Rsa Algorithm
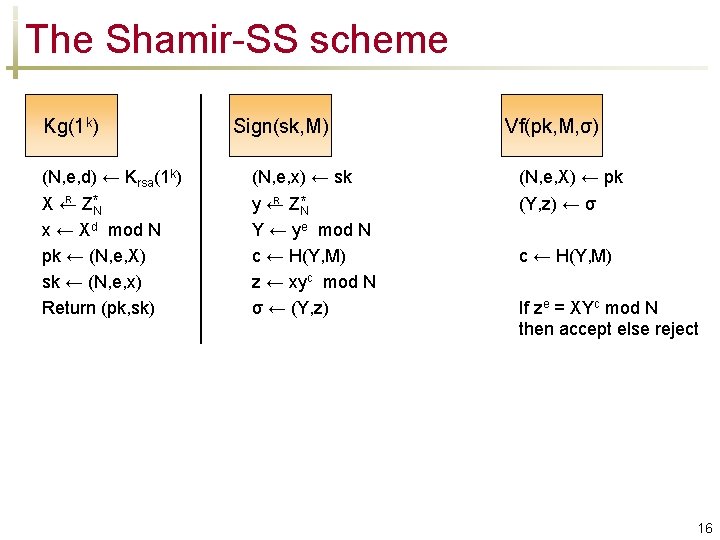
Security Proofs For Identitybased Identification And Signature Schemes
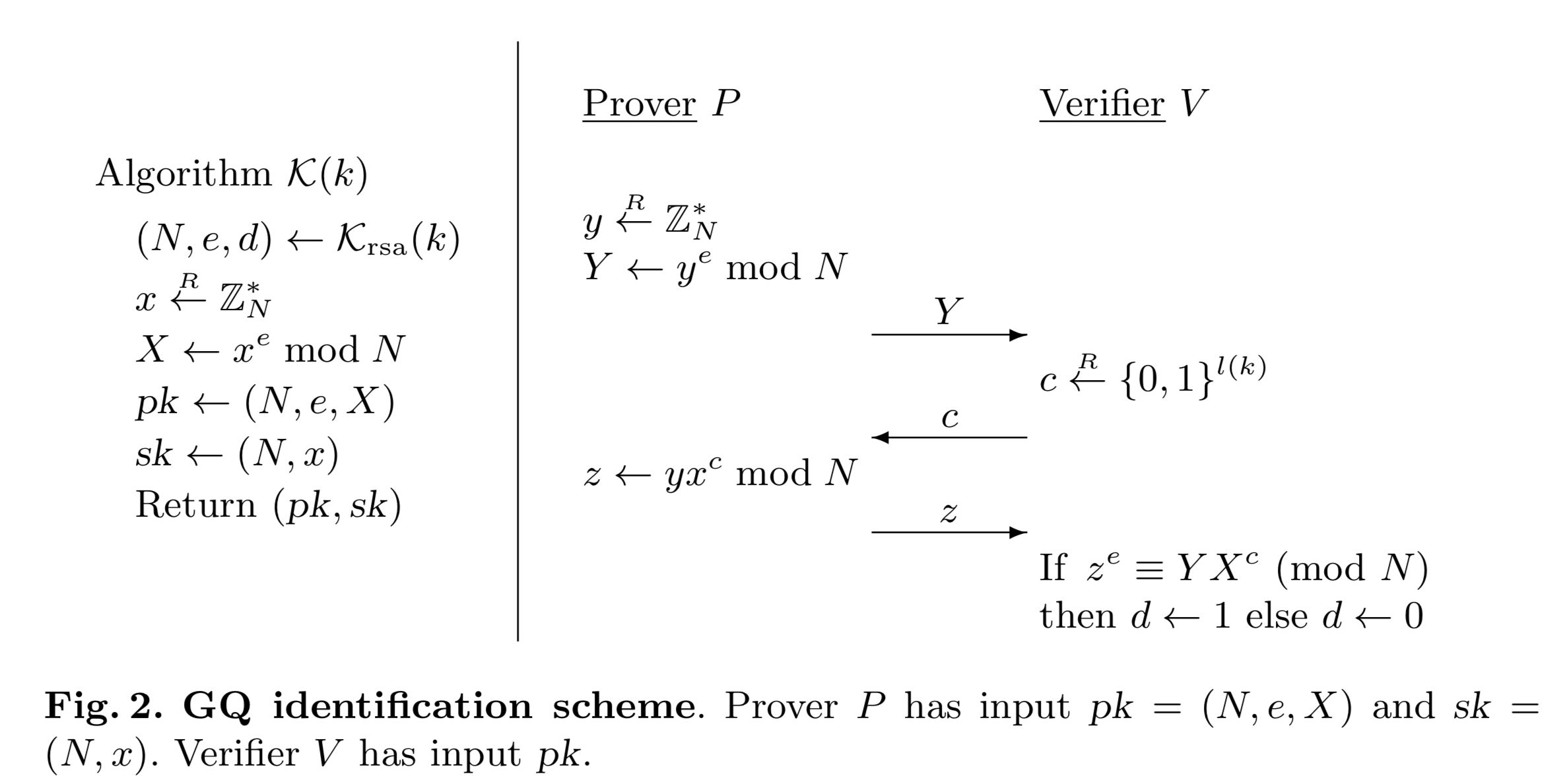
Guillou Quisquater Gq Identification Scheme
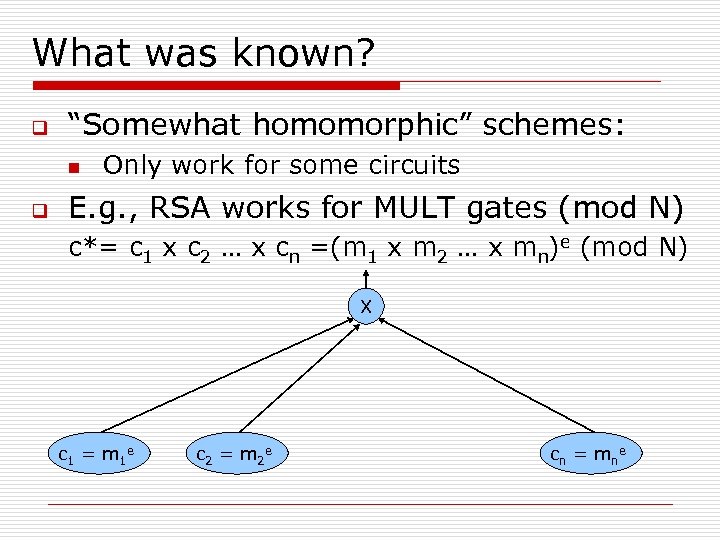
Fully Homomorphic Encryption Over The Integers Many Slides

Come On

Python Modulo Operator Math Fmod Examples Askpython

Solved Problem 3 Consider Rsa Code N 187 E 23 Message X Encrypted Computing 23 Mod 187 Decode Enc Q

Presentation

Test La Gamme De Produit Rhinoshield Ca Sert A Quoi
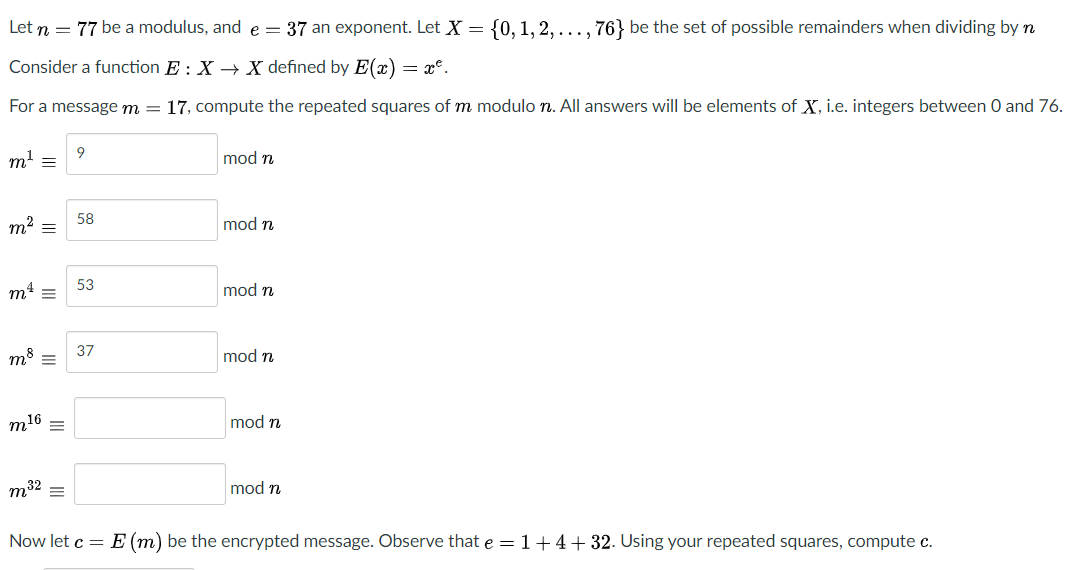
Solved Let N 77 Be A Modulus And E 37 An Exponent L Chegg Com

Modular Arithmetic Wikipedia
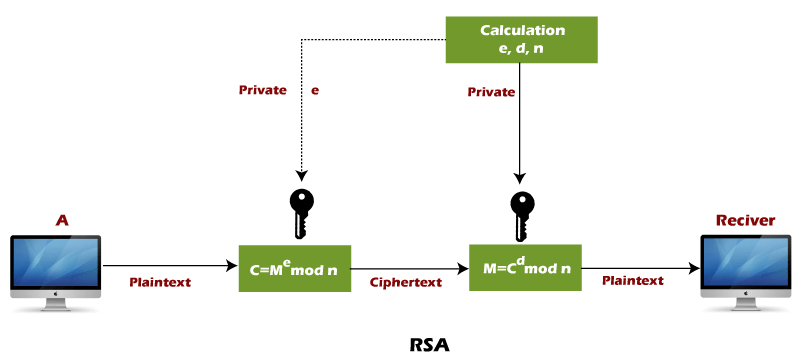
Rsa Encryption Algorithm Javatpoint

For The Function F X E X 1 E X 1 If N D Denotes The

Answered 11 Let Z Denotes The Integers Mod Bartleby

Cryptography Theory And Practice Applied Cryptography Prezentaciya Onlajn
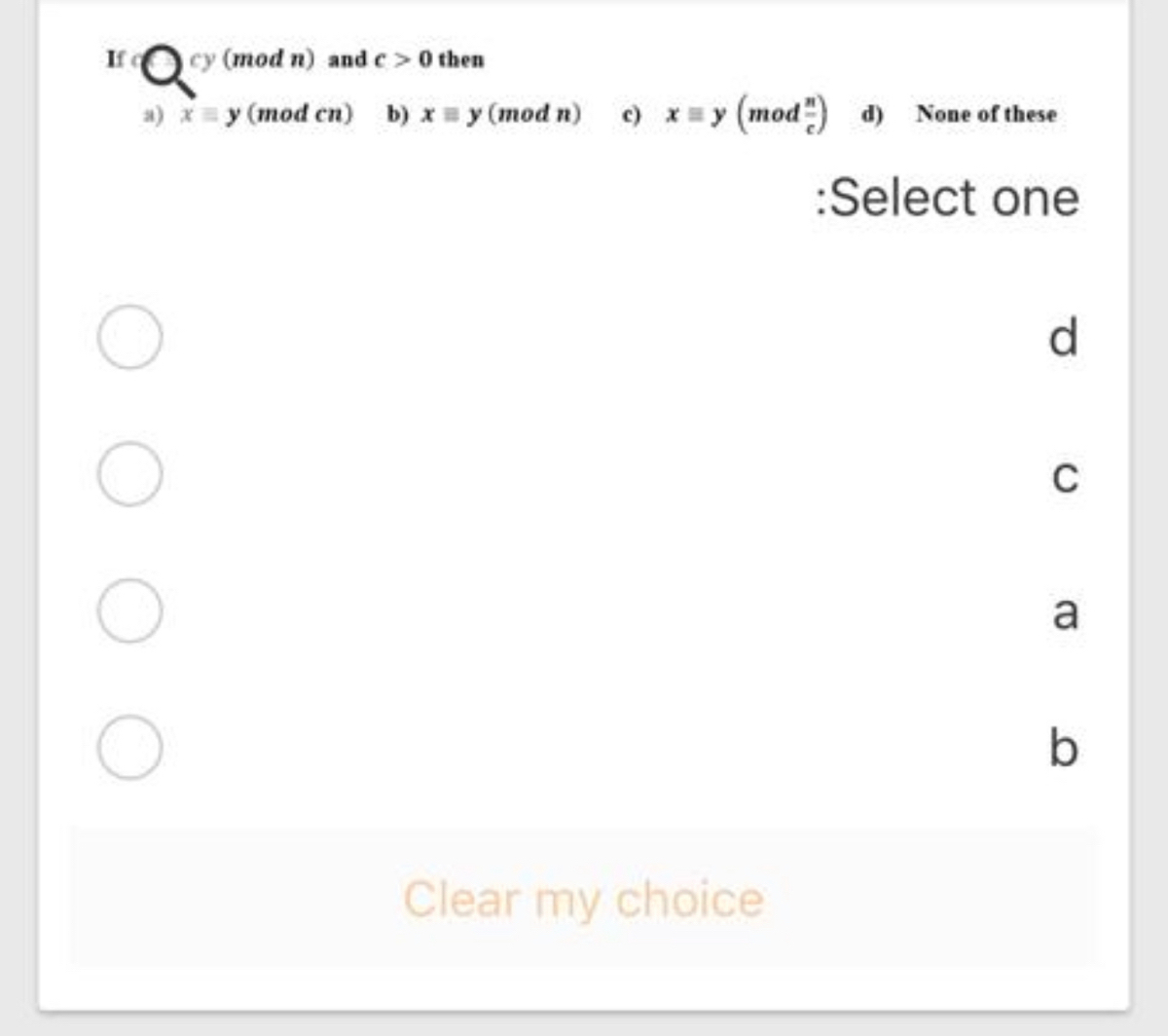
Answered Ifocy Mod N And E 0 Then A Y Bartleby
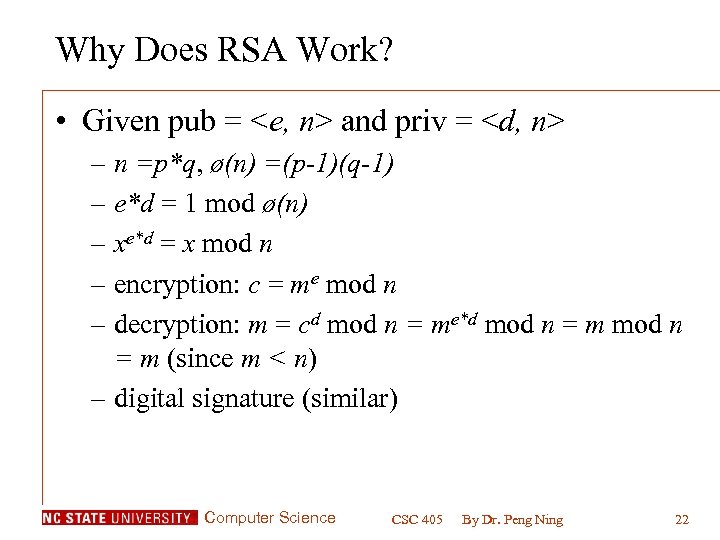
Computer Science Csc 405 Introduction To Computer Security
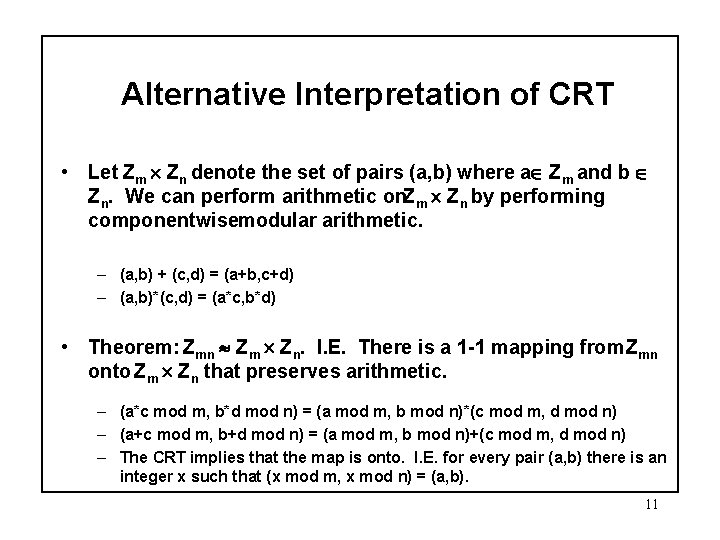
Applied Symbolic Computation Cs 300 Modular Arithmetic And
Ppt Congruence Powerpoint Presentation Free Download Id

An Attack Bound For Small Multiplicative Inverse Of F N Mod E With A Composed Prime Sum P Q Using Sublattice Based Techniques Semantic Scholar

Theorie Des Nombres L Arithmetique Modulaire Les Congruences
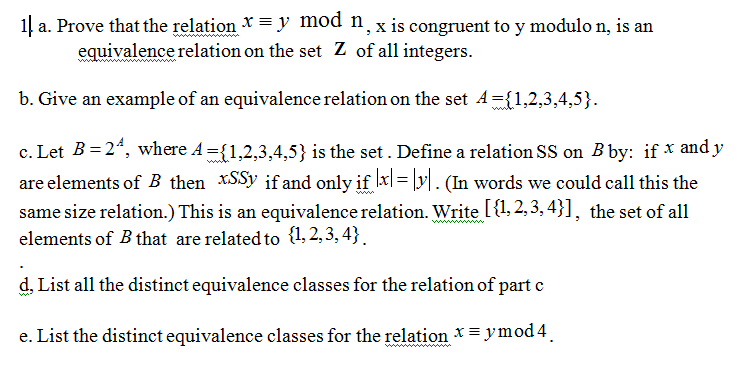
Prove That The Relation X Y Mod N X Is Congruen Chegg Com

Fondements Mathematiques De La Cryptographie Partie Iii

Chebyshev Polynomials Wikipedia

Pdf Distribution Of Factorials Modulo P

Tinkutara Equation Editor Math Forum Question 58

報告人 呂恩佑 1 Asymmetric Encryption Is A Form Of Cryptosystem In Which Encryption And Decryption Are Performed Using The Different Keystone A Public Key Ppt Download




