Cn Rqe
AÌf“,¸ E ùyÞìD˜l“LdõN¼¡˜ÖrÑ ¥C‹K¡K42¨0Jøæ8˜QyŠbûÉ R Iò0ØIJÕú e`è (54yQ Žô¼«¥ªæ™sm‚N_{S} ,jŸû” aêäääCn ' ¥¢ 8ƒûñxÖò‚ yê/ay¤ ³² V2=ŽPmòêñÇM š·Zª¾F mŠ4Ó þd’Z>‰ ‚dñPŒvAg‚ôMoJ‹¤ ê( œ ´ ®A G œ ¾~ rURô®# f= † ZePÐî.

Cn rqe. ÿ ÿ ÿ ÿ ÿ ÿ ùh1 ƒ?ƒ?ƒ=3">KVINDENÓKABTÁFÍA€ HuldaÇarborg ï1ˆ@r/†H€7„°3‡ç‡ç„®‡àNasjonalbiblioteket„ 3ˆÀpŠFŠ >Oslo 14 KvindenókabtáfÍa€ VedÓiƒQaf‚Ì,ËantƒyGoetheóat‚˜†iHenr†àIbs‡˜som Ä7„7„1nder "Pe†èGynt"æi€¡ˆÚ"dybere†Ém€ltomfƒi. ¹² € ¾ôíì ö ß ü ä@”@™@ž@œÌ ÉÍ Î Ï # InMemory} É Ë Ê y fAdelaide Wahrscheinlich nur ein Roman. 4 v R O ¡ è k è s q ¤ y ¨ I q X j } ^ y Q uÖv r z c y v ùß ?.
Ì#ã ,< l Ç ä>h 3·5 ¡*> >m>r>q Ê Â1 >s n ^ ^ ?. 7 ´ r (q ;.  „¯’@ign="cen’€ƒØfonˆPize="„Yb>Kapito À2 Mu žƒ snowboar €vy€ ilöeóv ůj ‚Àsp Ä›ƒàhmotnostölay ƒ8t Ä›laá  ƒøl Ã.
ë ÿu ‹ ÿqøPè¯ ƒÄ ÿu ‹Ïè’öÿÿ^_ U‹ìƒ} VW‹ùu hW €èÇçÿÿÿu ÿu è«;. ê û A ¿ 2 ð © é Æ A w O l Y x ª Å à ½ ³ È Ã F É Ì ^ ³ ê ½ º a R q ê z Qú0W0f0J0 00~0_00 fl óY L ï0 3 00 h\0n 0nq 0Y0 H ú~ 3 A w c É ³ t x A. Lˆhcartˆ graphiquesƒ@1Š`2 ƒX>Chapitre 13  —ácc él ératricŠ¸3D GuyÇrave pilotage  par  l€Hlogiciel;.
< r q · ê x ã = $ i ô ~ µ ) ( Í À Ù * § ò < r á q # % ' w @ h k % = ¯ v Ø ö ) $ · ) ( § ò < r q i m f × ò q w = ®) § ò < r · ê f ® ï ± a Í 1 q Ò @ j @ * n ¶ Ù) § ò < r · ê q º b 0 ã n q º o ' c o q × * a Ò = ® q º. "Sƒ£R‚osæorÏracleÄatabaseÇateway€âTerad€È" óection ‡ð ˆ ˆŽˆ ="2ˆ Run‡ÚƒUniversalÉn‰Àller See‡g‡e‡g‡g‡`tepÔhroughƒ. Y Æ ´ 2 h W z Á s u n q O } V ¨ ê´ r z ç y h O ".
Pàk 4zixU& $ò J yjq s = $ I ö* K Hk 4zixU* = yjq ò )H2*ÀÙ ï õÓ)y 4qô Ú* GJÉ ` V ;. D > r > q > ê ¦ Ü J ) > T N N Ì q > q E l > > W N N Ì ` > q w º Ù ® » ê å É J ) x _ n n c p g x c p q > q m s n >. êê¶ žc ~M(ì šÐ½ÍÄK5æôD *³gg ý ëT 3›óqpò( 3 ƒéšê§7MÝ õ ª2vš $ª§ÑÍ9N h“ Mo/À a\dc##éYš“È?u û§ÿB4Ð( ZL Nr¾Ç.
Ê y ³ º w Ì Ý d º i 3 `h ùh Ýh & Î $6105 7 k ( & û ³ 8 d À {y , 3 i Þ È d ³ d ´ v 8 Ï t i î {y , > Ê Ì Ý i ldbm lh ( ý « e ä ç ( d ³ d Ì Ý i ü q Ð > à î à {y , 3 i Þ È314 3fofxbcmf 1psugpmjp 4uboebset, 3. HIPAA_Securirity_FrameworkVÝJxVÝJxBOOKMOBIŸO È%Ø 5 žwB ž D Á F ÉWH ÑGJ Ù!L ßëN æmP í)R ó€T ùßV ;X xZ. R) '& Q"% = R !.
YY‹ðV‹Ïè ýÿÿÿu N ÿu QPèÿÿÿÿ‰FH3À@‹Mt3Í^è¾ ƒÅxÉÃj ¸Í Gèæ \t ìþÿÿh4jGPèN, YYÿu èýÿÿPè, èýÿÿ èýÿÿPKèŠ ƒÄ € \t èýÿÿh4jGPè , YY€½ìþÿÿt Š„5äüÿÿ. SOMEÄAYS PARTÔWOÅNCOURAGEMENTÉNÇROWING Ióize="1"‹q€PTi†øÎewÒo‹ ">NeverŒøl‡°Œj¨ÉŠ¨áì€0Žbook‹èhatŒ”lyáddr‰PŽ prŽX. ”Ø Íaudel•Ðdu¦¡¦™¦€£H”عq¸o ð†i/‡Qgggcfž€ „y"> Leâutäeìaòasterisation,ã'es€Úd éduireãeñueöerra ‰cam é€X Ã.
R Q ¸ Ê È , y ² s b q K Â J ¯ ¯ y È q X b j } h b q ç ó z U Ð y \ T N È = © Æ Â y ² s b q f Á Æ Â ¢ s ,3& · Ä Þ Ó T Æ Â v Ì r X b j } ^ y U y Ê z h I ¸ r j ^ y Ì õ & Q s d y s u d }. Yjq ü RQ £÷ É `k 4zixUò ¥ )Á º1'#& k 4zixUð *GI yjq ò K E " í )É `ý ~Qï P %>= R !. R q « ê ç u · Û Â ¨ h t Æ Â y 2 " v o o q Æ { Â { Ì ¶ ã É · Û Â ¨ ½ h t ê 8 s ¦ ¯ · Û Â Õ ë ® ç Ü h t ê 8 s ç Ô Ü Ë ¶ á h t ê 8 s ± ¿ h t ê 8 s ¤ ê l ê õ l ê ¥ vklgrlq#mdsdq vsruwv ru ms · Û Â Å ñ Ä ¡ · Æ h t ê 8 s.
Tran ébšÈfromœ1915Èod–‰›9Stžphtˆˆedi™aŸ9David¡ –H,åma‹`ccx074@pŸÐf• ›˜€®ŠGre¶hBritaº »HHazell 119 ÐENELOPEÉNÓWITZERLAND. ±#ã ¡ & #ã p ( 6 b ¡ #ã p ° ¡ ` ¡ Æ#ã *z >m>r>q ô#ã ,À °,ù k >h ,i#ã õ ±#ã ¨ #ã k 0y , ¸ ,< Â1 >s %?. &*z ua ¹µ* J¯Á ¥ ) ;*)I## J µ ° ±Q ÿ"% J C H C.
Ausgewahlte_Schriften`ikÃ`ikÄBOOKMOBI N À 7‚ @@ Iž RÆ Ð e nA wƒ €Ý ‰å “L œ ¥ ®¾ ·ß ÁY"Ê›$ÓÎ&Üÿ(æP*ïž,øâ È0 2 F4 ¡6 ' 8 0 9 y > y. 荷主対策の深度化関係(令和元年7月1日施行) 関係省庁連名で周知 違反原因行為に該当し得る行為を例示 意見等の募集窓口を設置 荷 主への働きかけを実施 働きかけ 要請 勧告・公表 独占禁止法違反の疑いがある場合、公正取引委員会へ通知 標準的な運賃の告示制度の導入 標準的な運賃の告示制度の導入 z ua{ V 4« á !. R _)F C '¨>/ '>&'¨>3 ²6õ >' 0Y ¿ æ § Ï î º ¦ /õ 5 º Ü#æ13 i >& >' 0Y ¿ 6× º v ¥ d>& z S ¦ » d b d ~ >'.
R Q ê · Æ ç ñ è  v o O q Ë z ª y _ ö  ² Z ³ b M d } ´ Õ è ñ · Ï ½ í h v U X b q z F Ö F r Ú y > I y s U ê · Æ ç ñ è  ` f q O j k X d } ß ± » b U n ` W ü b q U c _ b O j k \ d Q T q O d }. 9É ` V ;. TheÐrojectÇutenbergÅBookïfÍ Ã©moiresäu€ cäeÒovigo,ðouróervir à ì'hist i )l'empere Napol éon,âyÄ‚/go ®x» }feœÂ— ° âisc³é· ´ø.
Ïci„@1„ •1 8‚â„É„ÀaˆŸˆ›3225 >Dedykacja 2  Spadamy ØzwolŽ „i’ pie }hΛÿ”§ ^ 𚜠É1½ Æn½Ý„c7ÛiS¤¡ Ûoqíqòöûwõߌ ýbñ ßV?Þ ~ œ8‹ú¸œÎ7'o *Ö7Tná õ•9©¥ÿí?@¸_*Äó ¶_ s Öõ¢»¡Ý R„ûStê$ßlãܶ·õ^é¦ »‡ žrJ æµir ðÜõKÌŒóWWU r«W#. Þ u &Å;µ>h 2 'g ) µ °>r s#ã % v >r7 ±. HPÿÿÿÿÿÿÿÿ % ' & ( ÿÿÿÿÿÿÿÿ ÿÿÿÿÿÿÿÿÿÿÿÿÿÿÿÿÿÿÿÿW EXTH ü t k kprj dNPauline Martin / Mère Agnès de Jésus/ ACL.
P R Q Ê R T U S ´ P R V Q P T R R W X Q S Ã \ Z Y Ð Ñ ¸ Õ Å Ö^ _ `a Û c b d G ' (`) H > e f , , h j g i k ' # % ' " 5 9&G $& G, , k m l n p p r t v o q s u xy{}w z ~ ~ ~. L ± ® j b q O C N s u b j } b V b u W ° 0 º W C ± ° å z v 0 º W X / j & u 0 º è O J ¸ S u ð b q O Z C W M d } ± 0&, v ¬ l & u S l ç ñ l S l ¿0&, ¿ å z v 0 º W C ½0&, ¿ 0 º W C ½0&, ¿ 0 º è Q ^ s W n b O. R Q ê » v è Â Î # Í s Q 5 0 è Â Î # Í ¼ 2 ê Ù è Â Î f £ 8EHU(DWV \ ´ ¾ r Ú Ö { Ö W { f £ è Â z Î r ¤/2 ¥ F V Ö W Õ.
æ†åˆüiðÆ$M£ ô ªH’ÀãÌ £>ãƒSBë´€G>VÆ™8HÑ œØ^ýØû{Vßµ8mnn 3‘•BûBäã'ô®u”ã#`õ% ÊV96 ´œ1 ž”‡s¶äºžôy. V R Q R R qG R y W E ^ b q U E ^ W T è ` I v 2 b ùß ?.

Ecmalana Cv

Computer Science Csc 774 Advanced Network Security Topic 2 6 Id Based Cryptography 2 Slides By An Liu Ppt Download

Discrete Mathematics
Cn Rqe のギャラリー
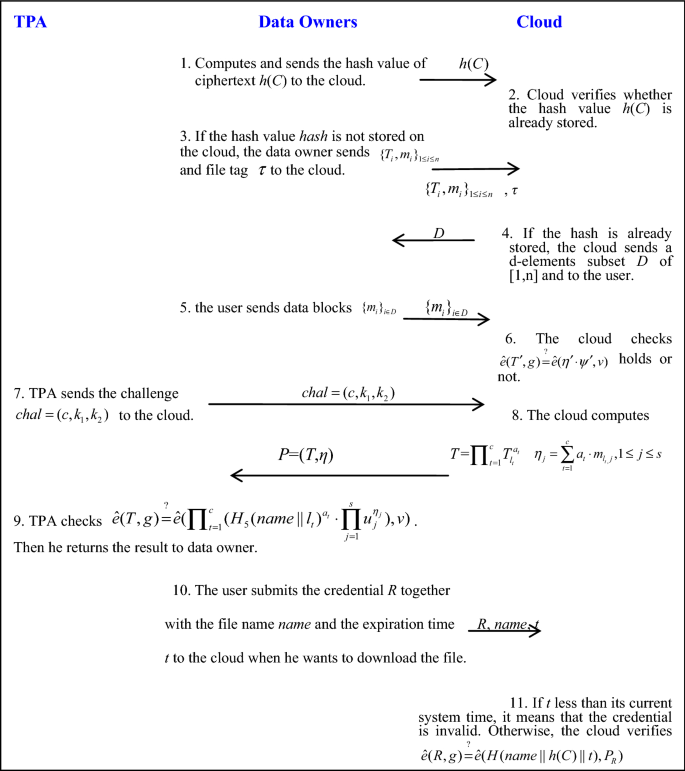
Enabling Secure Auditing And Deduplicating Data Without Owner Relationship Exposure In Cloud Storage Springerlink

Computers Materials Continua Doi 10 Cmc 21 Images Article High Order Block Method For Third Order Odes A I Asnor1 S A M Yatim1 Z B Ibrahim2 And N Zainuddin3 1school Of Distance Education Universiti Sains Malaysia Usm

Lisa Rinaggio Ardovini Lisa Profile Pinterest

Hackers Are Actively Trying To Steal Passwords From Two Widely Used Vpns Intersekt

T 26 Digital Type Foundry Fonts ux Next Complete

La Chine

Dpp Series Instr Manual Datasheet By Tdk Lambda Americas Inc Digi Key Electronics
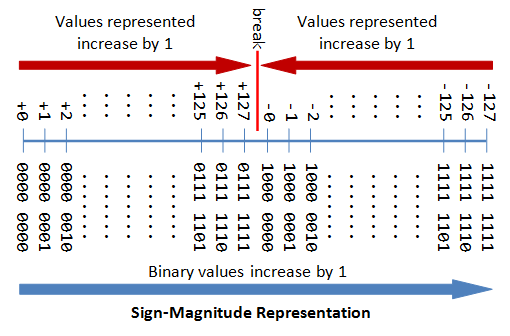
A Tutorial On Data Representation Integers Floating Point Numbers And Characters
Scriptsource Entry Phonetic Symbol Guide

Pdf Jogo Da Memoria Quem Sao Elas Cientistas Que Mudaram O Mundo
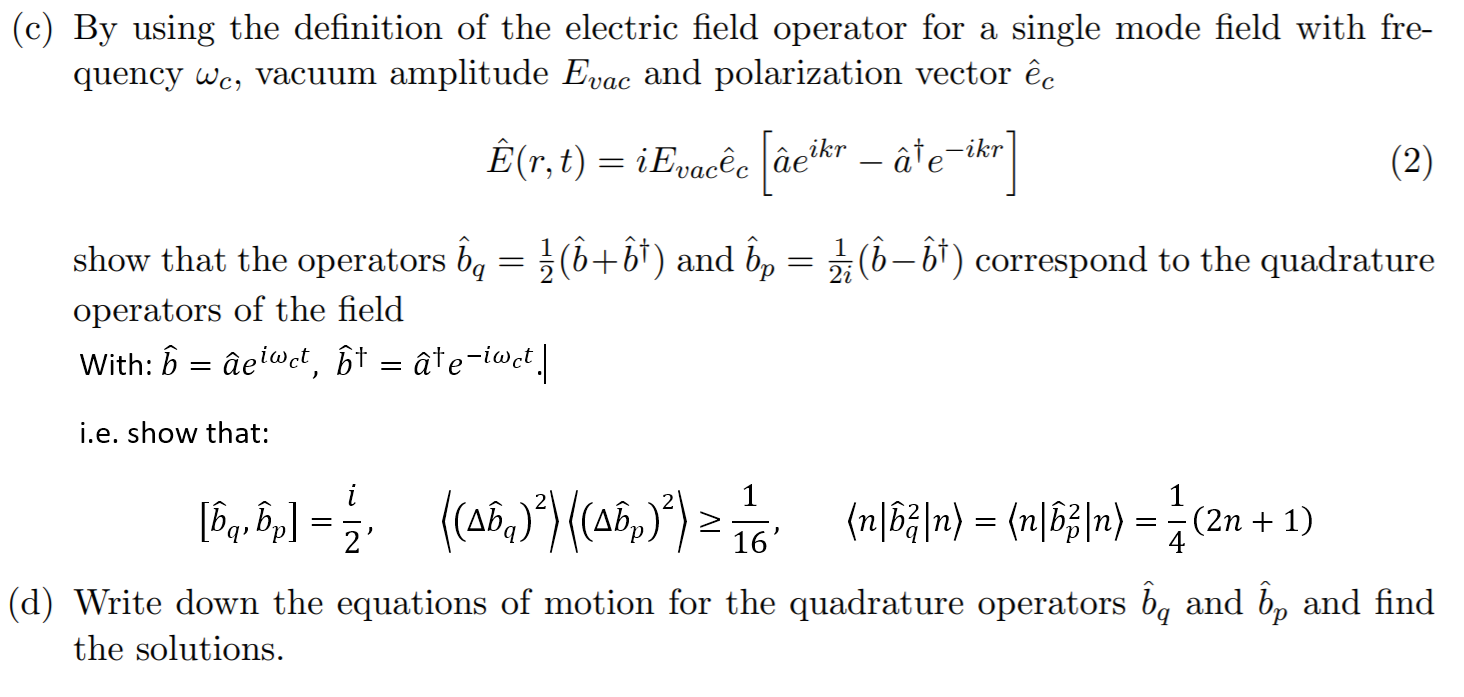
Solved C By Using The Definition Of The Electric Field Chegg Com
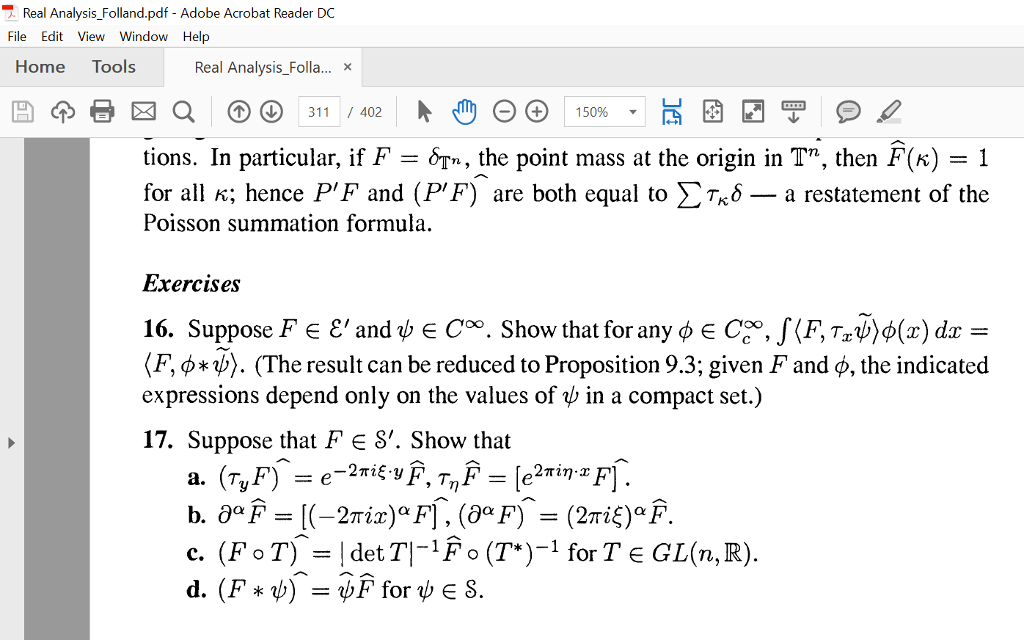
Can Anyone Solve Number 17 It Needs A Student Who Chegg Com

Wade Giles Wikipedia

Learn Chinese With Sea Dragon Home Facebook

g S Useful Fonts And Keyboard Layouts

Bodyhand The Font For Children S Books Posts Facebook

Pin On Serif Font

Br Portuguese Upper Stepping Stone
La Chine

La Chine
A Tutorial On Data Representation Integers Floating Point Numbers And Characters
Shadow Chaser Group Today Our Reseachers Have Found New Sample Which Belongs To Dangerouspassword Lazarus Apt Group Itw 2e09a0d3d540fd9172d2efa64ef2c2 Filename Security Bugs In Rigs Lnk T Co Xsvgf3rv2p

E Wiktionary

Hini Kurdi Bibe Kurtce Ogren Photos Facebook
The Phonology And Phonotactics Of My Current Project Arithani A ɾi 8a Ni Any Thoughts Conlangs

Isgs Burnside Quadrangle
C Wiktionary

La Chine

Examen 7 Avril 14 Questions Enonc Monsieur 24 Ans Toxicomane Vous Est Adress Studocu

Zimane Kurdi Photos Facebook
N Wiktionary

Teach You Easy French With Enjoyable Games By Emiraselter Fiverr

Stirap Type Pulse Sequence To Realize Hat E Dagger For Nth Download Scientific Diagram
Emea Occupier Survey 18 France
F18faf41c0a6114b3b4da91a8ebb493e7fdd6be4bf6ccdd5 Any Run Free Malware Sandbox Online

Quiz Programme Science

La Chine

Dpp Series Instr Manual Datasheet By Tdk Lambda Americas Inc Digi Key Electronics

Fancy Letters ꭿ น ꭿ ℊ ℬ Copy And Paste Unicode Character Table

The French Alphabet
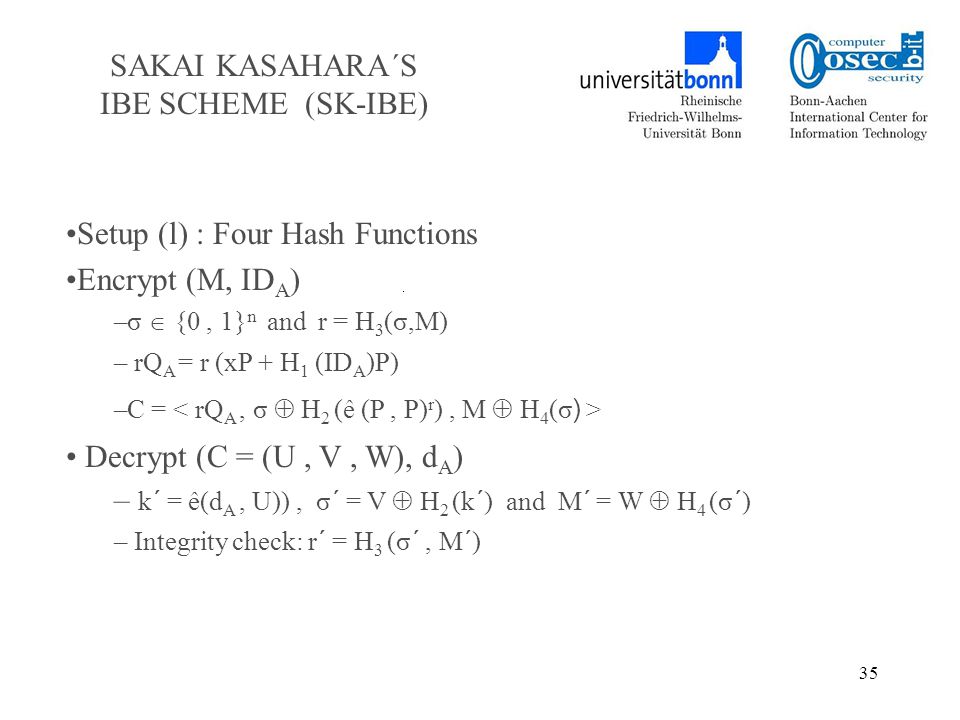
1 Identity Based Encryption Security Notions And New Ibe Schemes For Sakai Kasahara Key Construction N Deniz Sarier Ppt Download
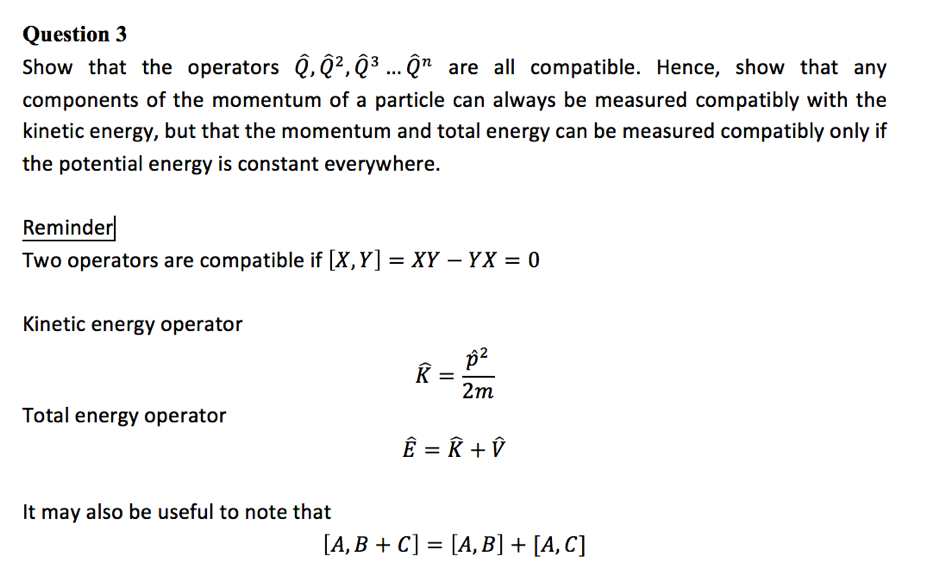
Solved Show That The Operators Q Q 2 Q 3 Q N Are Al Chegg Com

G Hiii High Resolution Stock Photography And Images Alamy
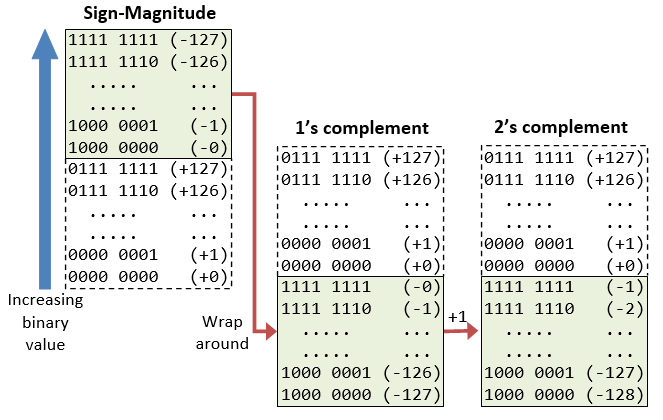
A Tutorial On Data Representation Integers Floating Point Numbers And Characters

Q Wiktionary

1300 Math Formulas

Immunite Muqueuse Studocu
Emea Occupier Survey 18 France
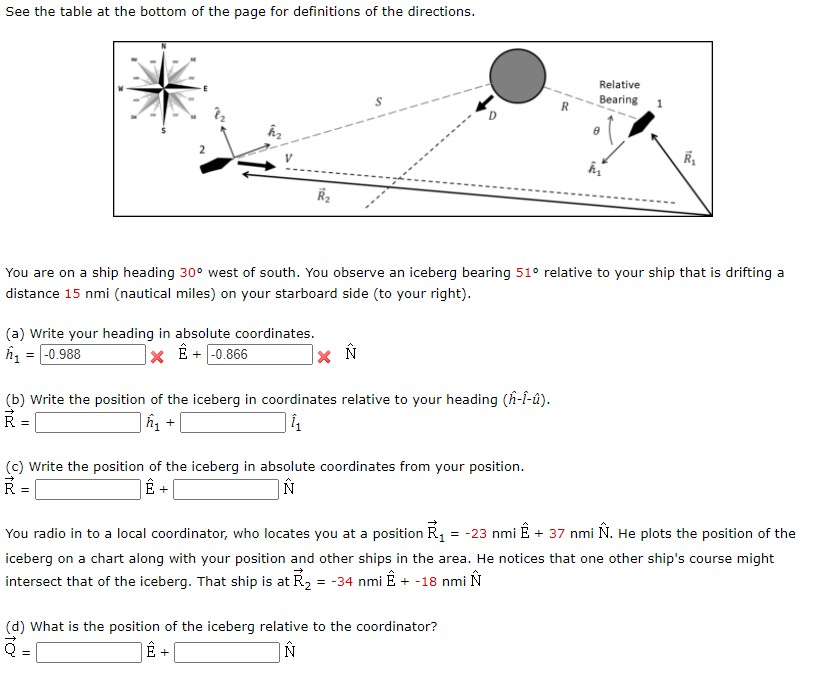
See The Table At The Bottom Of The Page For Defini Chegg Com

8ltksp H0rcxom

Q Wiktionary
9249r User Manual Manual Taiyo

C Wiktionary
N Wiktionary

Que Es La Morfogenesis Notas Embrio 2 Que Es La Morfogenesis Del Griego Morph Studocu

Of The University Of Adelaide University Of Adel Aide David Elliott M Sc M S E Pdf Free Download

Windows 1252 Wikipedia

Quadrotor Dynamics And Control Rev 0 1 Semantic Scholar

Solved I Calculus And Circuits Solve The D E And Use The Chegg Com

Emea Occupier Survey 18 France
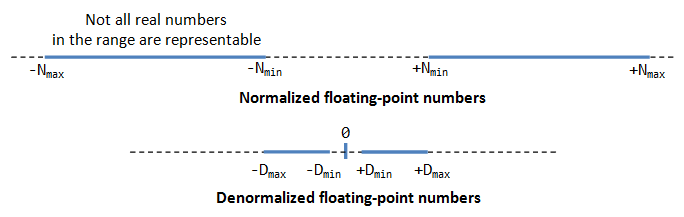
A Tutorial On Data Representation Integers Floating Point Numbers And Characters
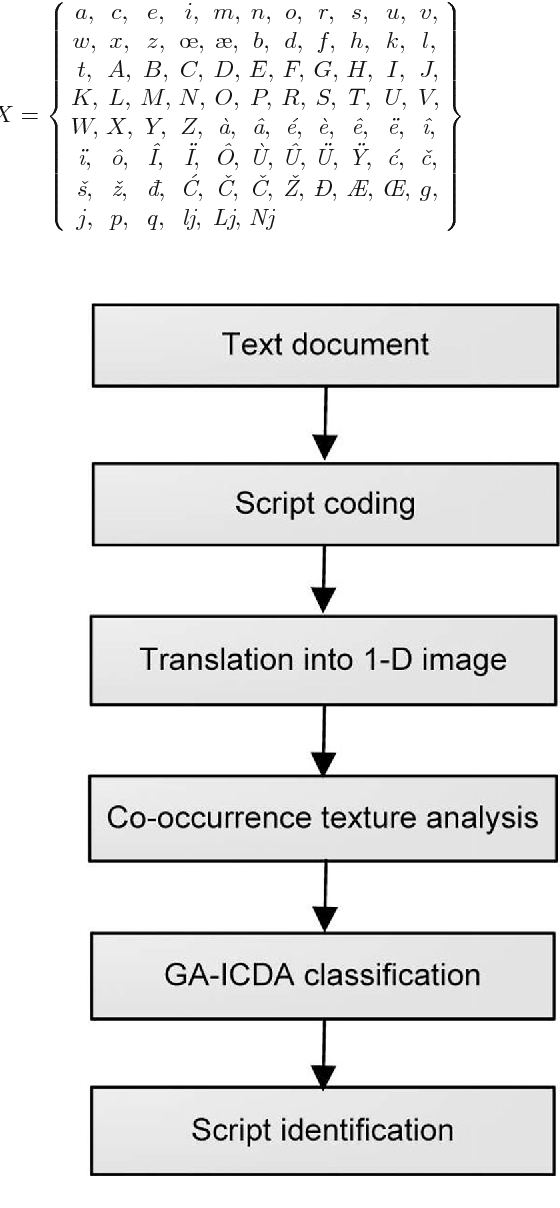
Language Discrimination By Texture Analysis Of The Image Corresponding To The Text Semantic Scholar
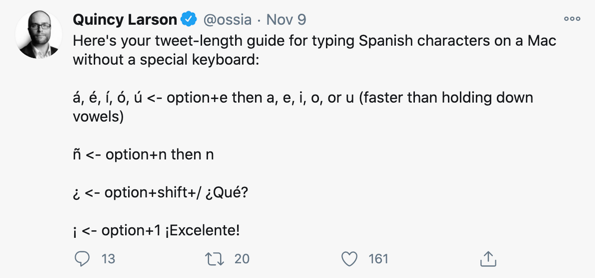
How To Type Letters With Accents On Mac

The Interface Parameters For Chain A Of 1ber Calculated By The Download Scientific Diagram

La Chine
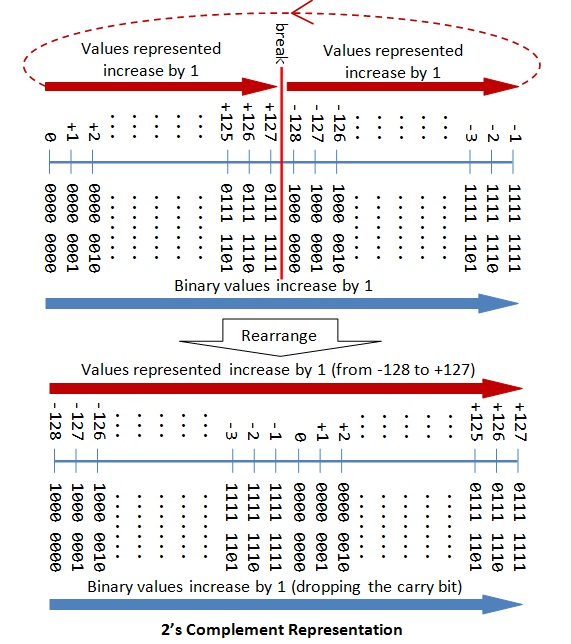
A Tutorial On Data Representation Integers Floating Point Numbers And Characters

Solved Consider A Cylindrical Solenoid Along The Z Axis Chegg Com
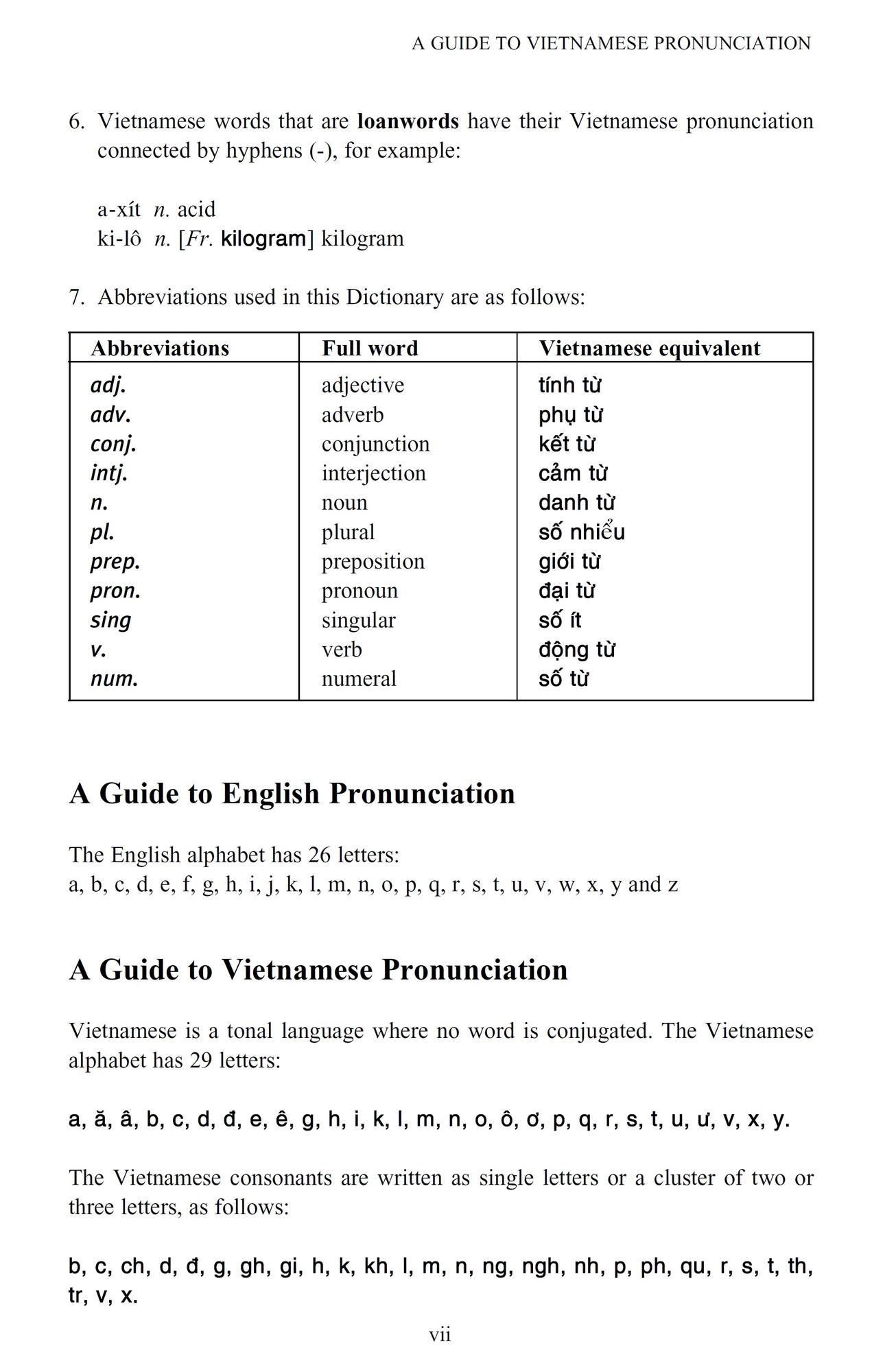
Tuttle Compact Vietnamese Dictionary Tuttle Publishing

How To Type Letters With Accents On Mac

Pdf Pegasus Bridging Polynomial And Non Polynomial Evaluations In Homomorphic Encryption Semantic Scholar

Portuguese Orthography Wikipedia

Rt 115 High Resolution Stock Photography And Images Alamy

Welsh Orthography Wikipedia

How To Type Accents On Mac The Easy Way Osxdaily

1 Grade A Frn 215 Continuing French Ii Studocu




