Cn Kxubn Id
More formally, the number of k element subsets (or k combinations) of an n element set This number can be.

Cn kxubn id. ∗) (valid for any elements x , y of a commutative ring), which explains the name "binomial coefficient" Another occurrence of this number is in combinatorics, where it gives the number of ways, disregarding order, that k objects can be chosen from among n objects;. C n d r s x n, Oklahoma City, Oklahoma 148 likes 18 y/o producer drumline DJ @LND_RNRS. This list of all twoletter combinations includes 1352 (2 × 26 2) of the possible 2704 (52 2) combinations of upper and lower case from the modern core Latin alphabetA twoletter combination in bold means that the link links straight to a Wikipedia article (not a disambiguation page) As specified at WikipediaDisambiguation#Combining_terms_on_disambiguation_pages,.

Solved 3 30pts Let X N Mo Find The Constant K A P Chegg Com
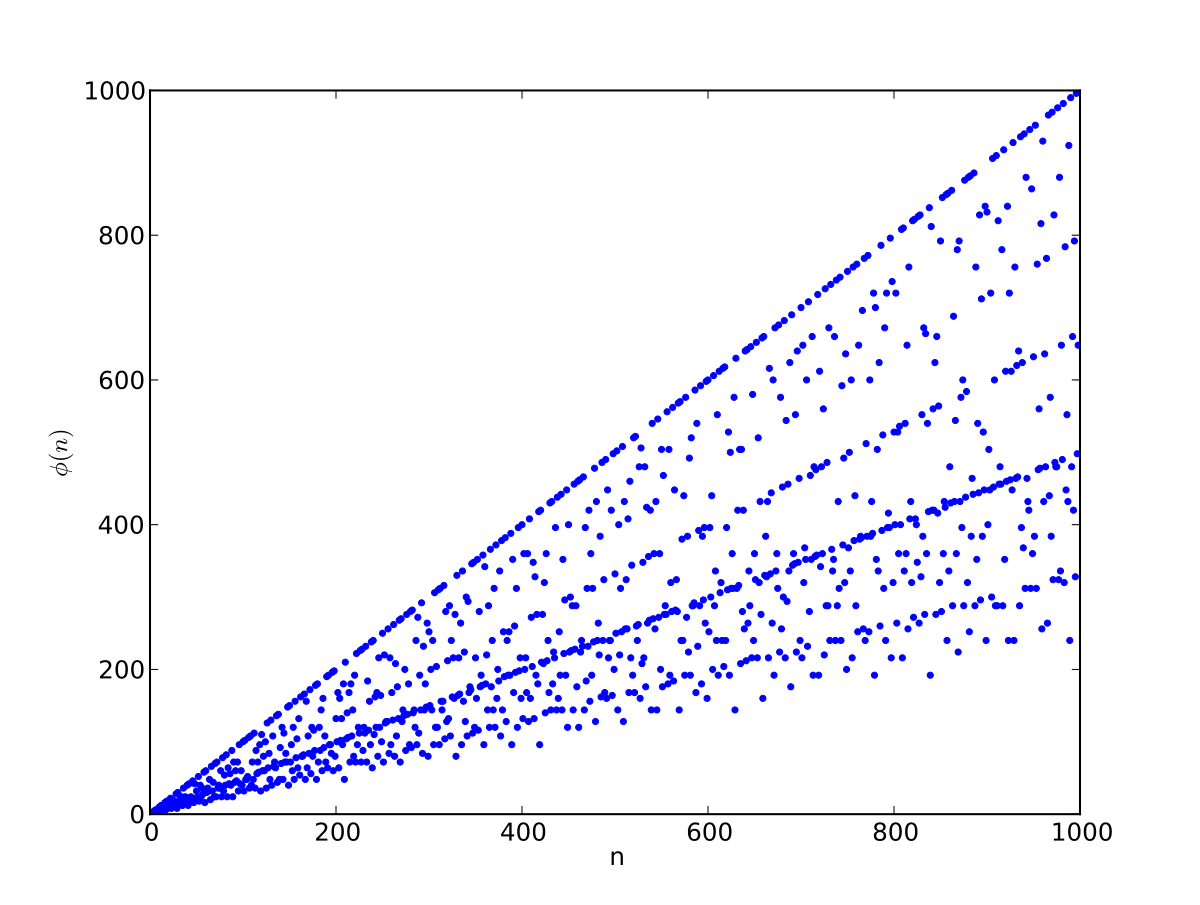
Euler S Totient Function Wikipedia

Ppt Function X Solsup U B N M Size U X Zeros N 1 If Abs U N N Eps Powerpoint Presentation Id
Cn Kxubn Id のギャラリー
Pdf Two Trichodinid Ectoparasites From Marine Molluscs In The Yellow Sea Off China With The Description Of Trichodina Caecellae N Sp Protozoa Ciliophora Peritrichia

A Formal Specification And Verification Framework For Timed Security Protocols

Pdf Identity Based Encryption Tightly Secure Under Chosen Ciphertext Attacks Semantic Scholar
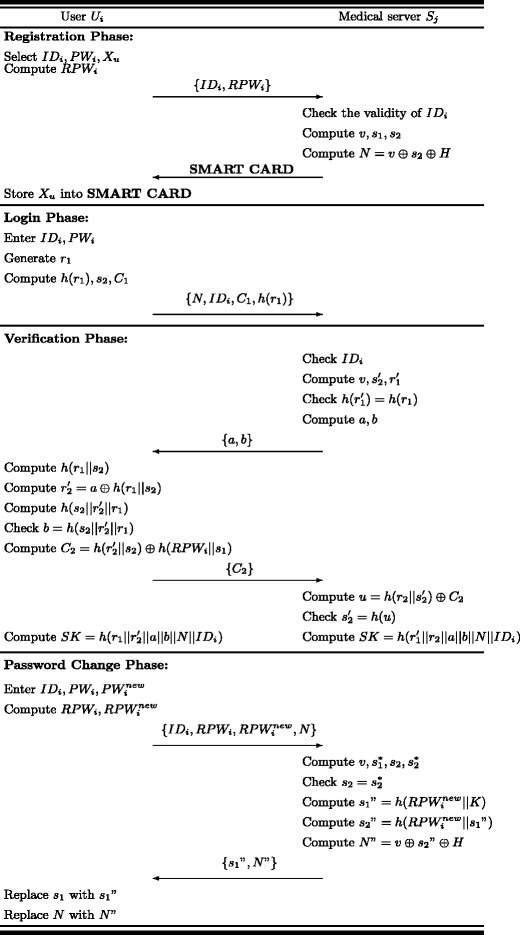
A Hash Based Remote User Authentication And Authenticated Key Agreement Scheme For The Integrated Epr Information System Springerlink

An Unmanned Helicopter Model Identification Method Based On The Immune Particle Swarm Optimization Algorithm Scientific Net
Plos One Knowledge Reuse In Software Projects Retrieving Software Development Q A Posts Based On Project Task Similarity
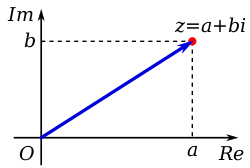
Complex Number Wikipedia

Phase Velocity Wikipedia

Proof That P Is Irrational Wikipedia

Silent S Le A P T Ass Kn 0 T 0 W 00 D
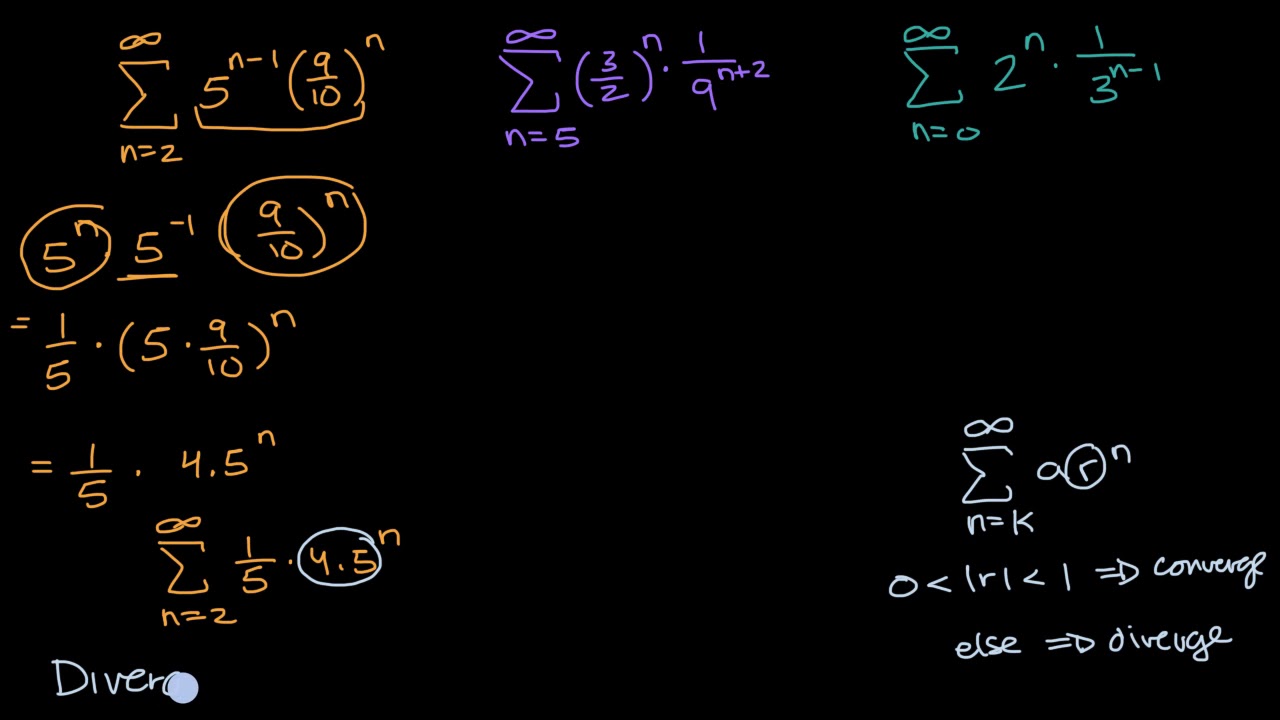
Convergent Divergent Geometric Series With Manipulation Video Khan Academy
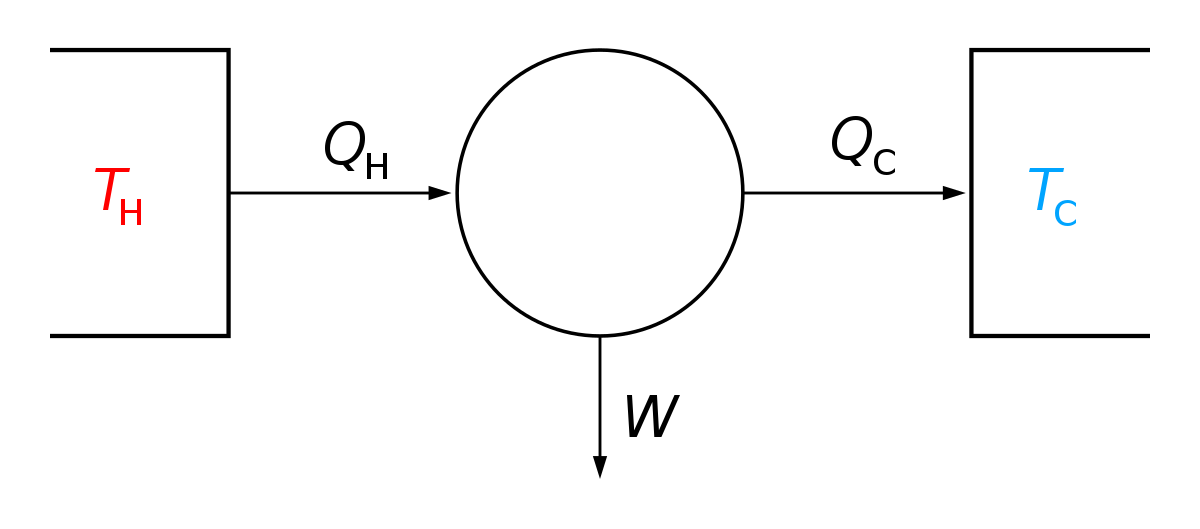
Table Of Thermodynamic Equations Wikipedia
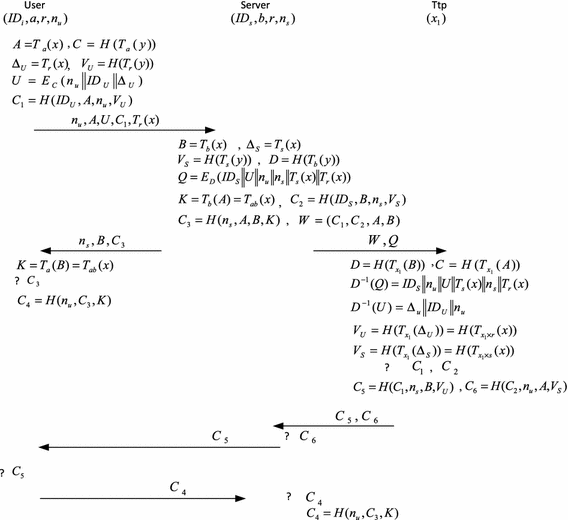
An Efficient And Secure Key Agreement Protocol Preserving User Anonymity Under Chebyshev Chaotic Maps Springerlink

Pdf Identity Based Encryption Tightly Secure Under Chosen Ciphertext Attacks Semantic Scholar

2 Pi Sampling Across A 96 Condition Plate Layout Well A1 Is On The Download Scientific Diagram

Annual Report Of The Director Of Animal Industry For The Year Ending November 30 19 1934 A Uu T Ui R Oj N A L C O Ur Gt U 3 Gt O
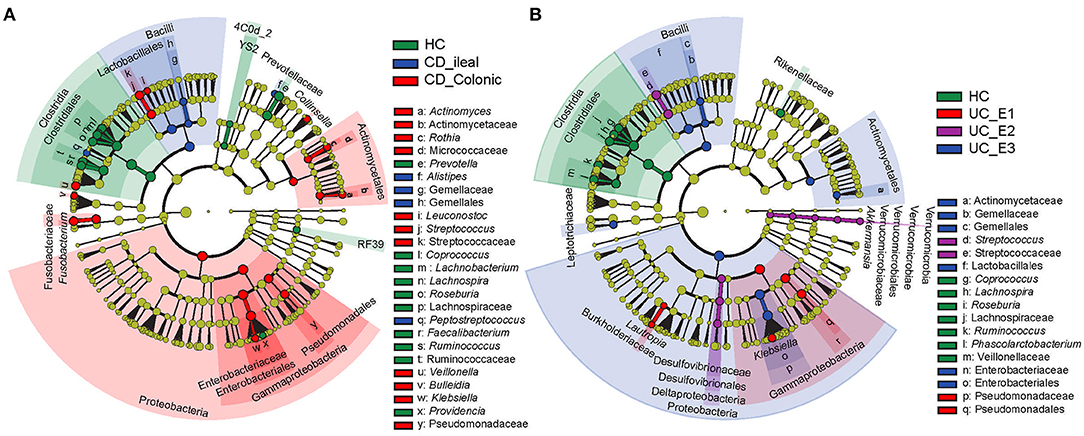
Frontiers Alterations In Gut Microbial Communities Across Anatomical Locations In Inflammatory Bowel Diseases Nutrition
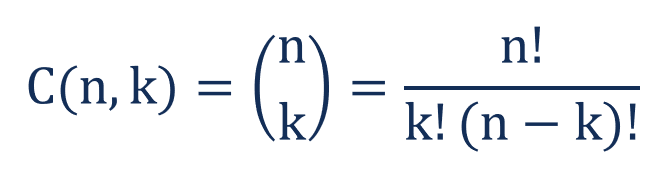
Combination Definition Formula And Practical Example

Pdf Effective Elimination Of Nucleic Acids From Bacterial Protein Samples For Optimized Blue Native Polyacrylamide Gel Electrophoresis

Apgar S Plant Analysis Adapted To Gray S Botanies Plants Ls U F Id Ja Crtl 4 Amp Lt Iifa A F I Lt L H Viv I 4 Rtc L R R Lt L Remarks R T Lt U Lt F A Lt I A Class 2i
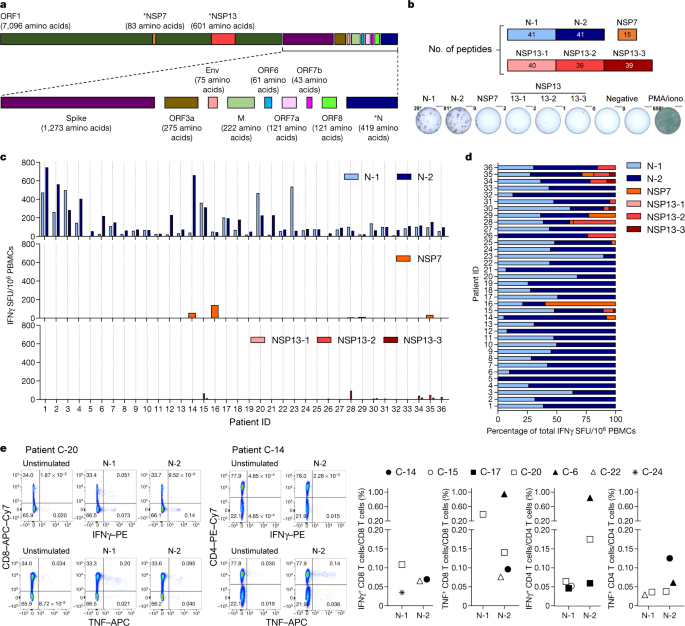
Sars Cov 2 Specific T Cell Immunity In Cases Of Covid 19 And Sars And Uninfected Controls Nature
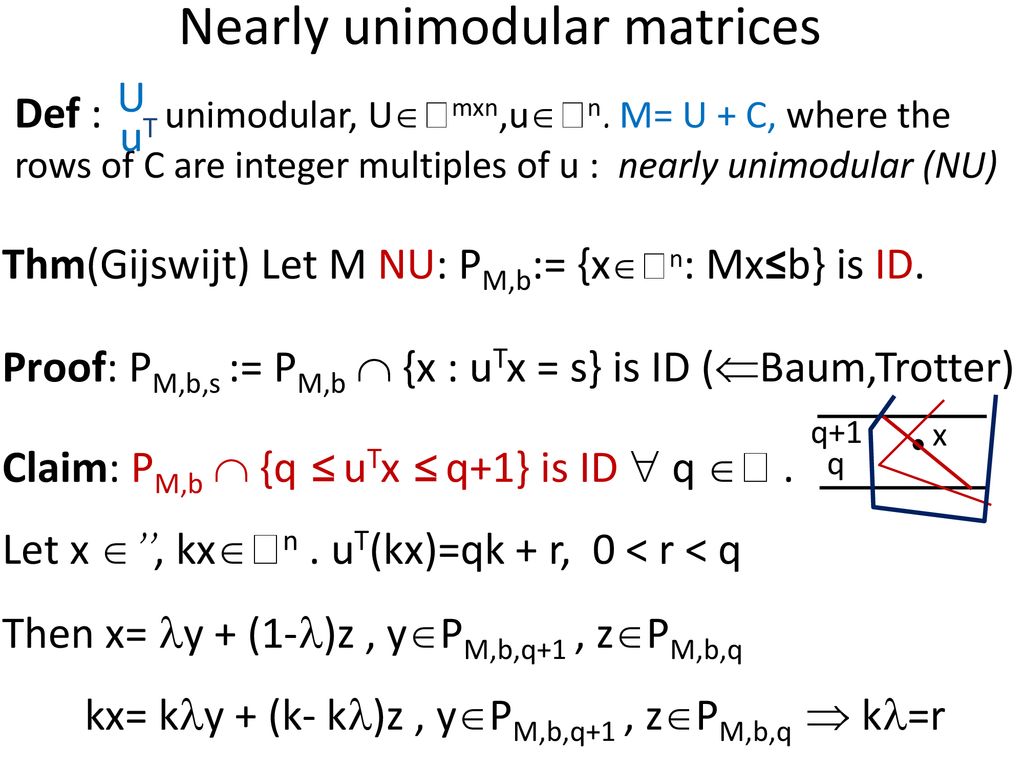
Andras Sebo Cnrs G Scop Grenoble Ppt Download

Binomial Theorem Formula Definition Britannica

Efficient And Secure Content Dissemination Architecture For Content Centric Network Using Ecc Based Public Key Infrastructure Sciencedirect
Dietary Amino Acid Requirements Of The Almond Moth Cadra Cautella Walker Based On Radiometric And Carcass Analysis Techniques Moths Amino Acids In Animal Nutrition 56 A Tyr X Origin 2 Dimension

0 Master
Pdf Unilateral Global Interval Bifurcation For The Hessian Equation And Its Applications

The Binomial Distribution
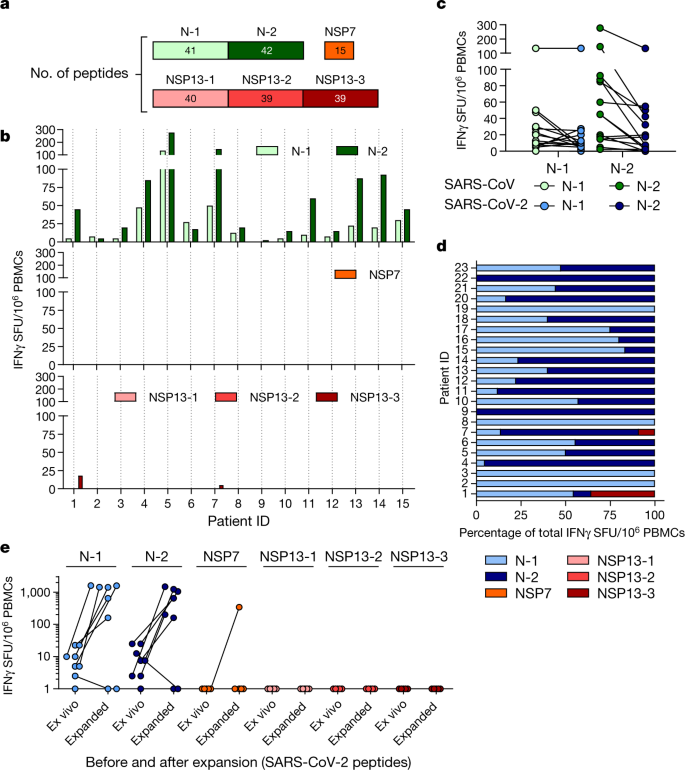
Sars Cov 2 Specific T Cell Immunity In Cases Of Covid 19 And Sars And Uninfected Controls Nature
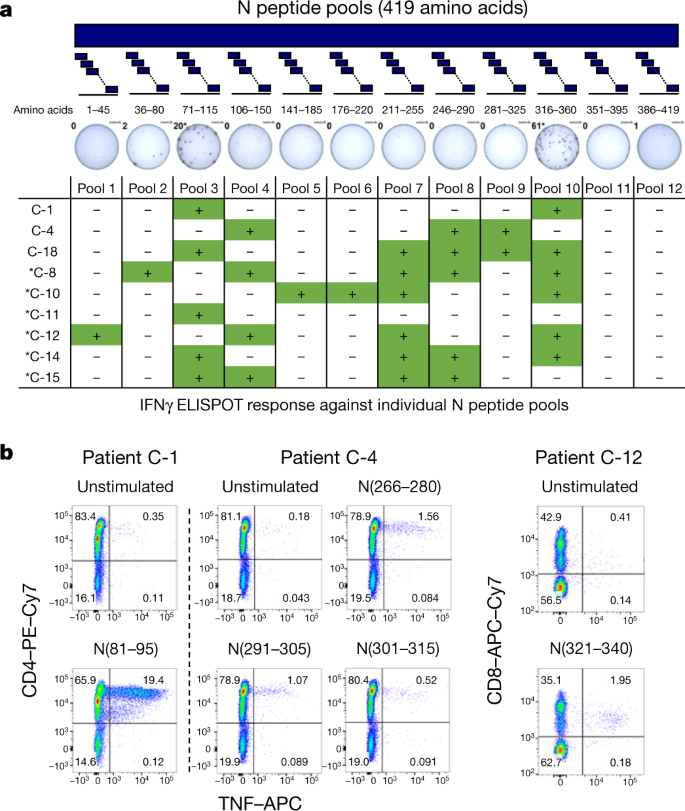
Sars Cov 2 Specific T Cell Immunity In Cases Of Covid 19 And Sars And Uninfected Controls Nature

Telescoping Series Video Series Khan Academy

S Safahkhanx Tiktok Watch S S Newest Tiktok Videos

A Familial Cluster Of Pneumonia Associated With The 19 Novel Coronavirus Indicating Person To Person Transmission A Study Of A Family Cluster The Lancet
Commercial Turpentines Their Quality And Methods For Their Examination X 1 1 Ecooojtjcooc Udo Co 1 Co Cd I J Cc Id Ih 00 C4 Co E4 Jj Ex 00 3 5

Iso 3166 1 Alpha 2 Wikipedia

Ibe With Tight Security Against Selective Opening And Chosen Ciphertext Attacks Springerlink

Solved Air Is Compressed Isothermally From 13 Psi A And 5 Chegg Com

Pdf A Unified Analytical Model For Proof Of X Schemes

Genomic Characterisation And Epidemiology Of 19 Novel Coronavirus Implications For Virus Origins And Receptor Binding The Lancet

Pdf Security Analysis Of A Single Sign On Mechanism For Distributed Computer Networks Semantic Scholar

Pdf Dynamic Biological Modelling A Language Based Approach Semantic Scholar
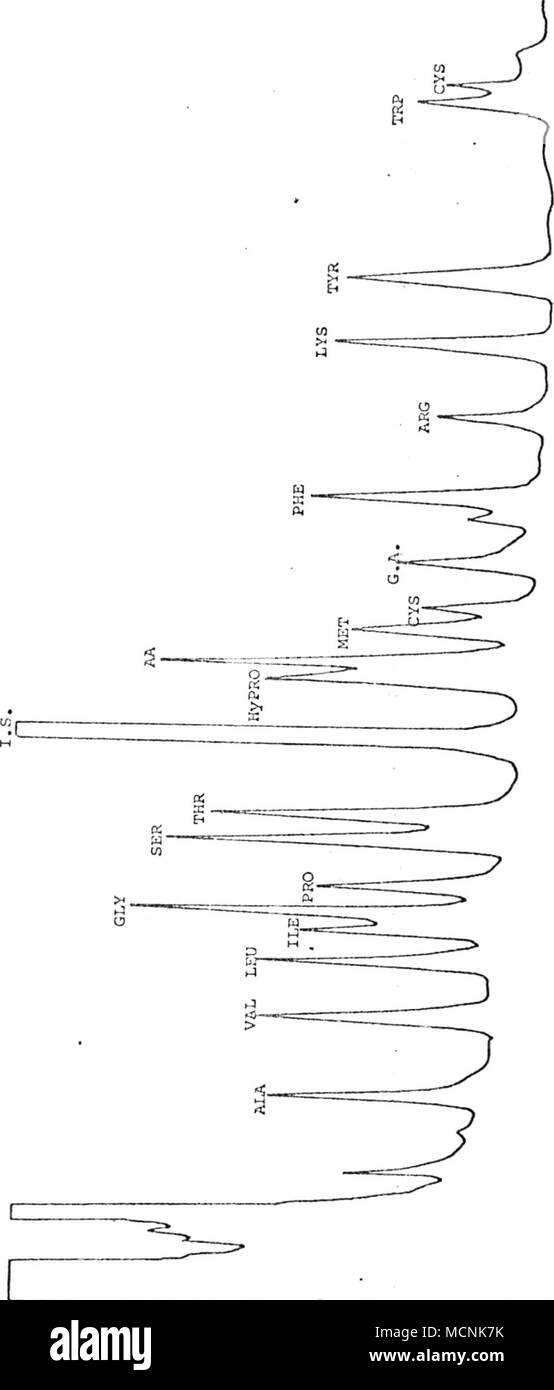
T1 B High Resolution Stock Photography And Images Alamy
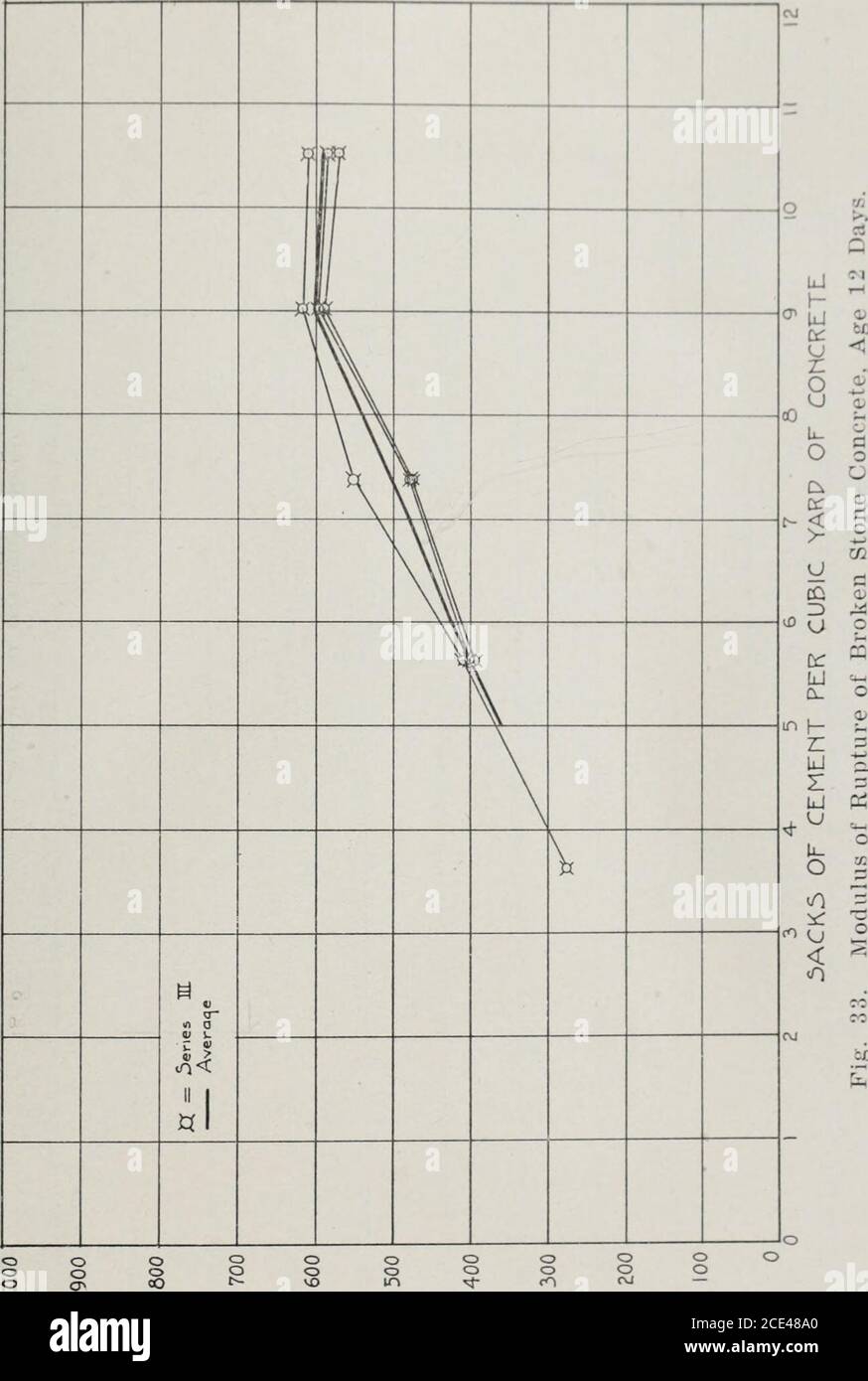
Engineering Research Series Id 02 Gt Gt H Ci Uj W T 1 L O 0 U Wj 1 B O O Gt T J C Ex O Lt Ciop U 0

Systematic Phenomics Analysis Deconvolutes Genes Mutated In Intellectual Disability Into Biologically Coherent Modules Abstract Europe Pmc

Pdf Cryptanalysis Of Three Password Based Remote User Authentication Schemes With Non Tamper Resistant Smart Card Semantic Scholar
/w-9-form-4f788e54c74c4242a4e88dc1183361f5.jpg)
Form W 9 Request For Taxpayer Identification Number Tin And Certification Definition

Proof That P Is Irrational Wikipedia

Euler S Totient Function Wikipedia

R H And H 0 M E I D E B T H B 0ug Ht

The Binomial Theorem Boundless Algebra

Complex Number Wikipedia
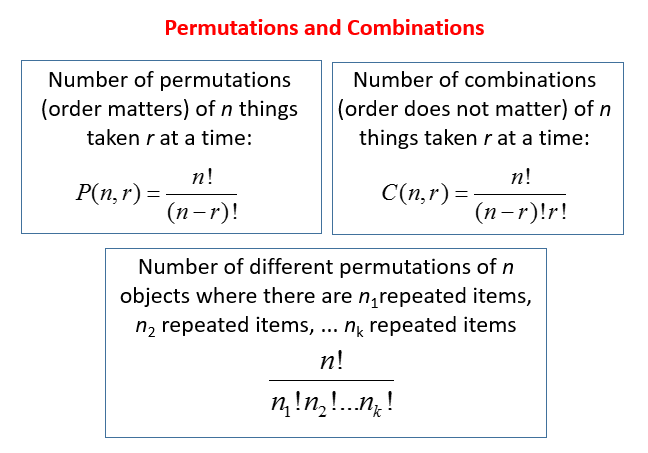
Permutations P N R Video Lessons Examples And Solutions




