Bhxg Mod
ModsBasecom is mods sharing service With our powerful network your popular mods will be always reachable.

Bhxg mod. ࡱ > 5 6 !. Download new mod and update them Store and manage all your mods!. Upload multiple mods at once and keep them forever on this site We do not remove inactive mods, your mods is always safe It's absolutely free Share your mods with everyone!.
Group Action Wikipedia

How To Fix Garry S Mod Issues On Windows 10

Shmqv An Efficient Key Exchange Protocol For Power Limited Devices Pdf Free Download
Bhxg Mod のギャラリー

A Comprehensive Formal Security Analysis And Revision Of The Two Phase Key Exchange Primitive Of Tpm 2 0 Sciencedirect

A Consider The Following Key Exchange Protocol W Chegg Com

Solved 2 7 Points F X X Mod 7 G X 2 H X Lg X Chegg Com
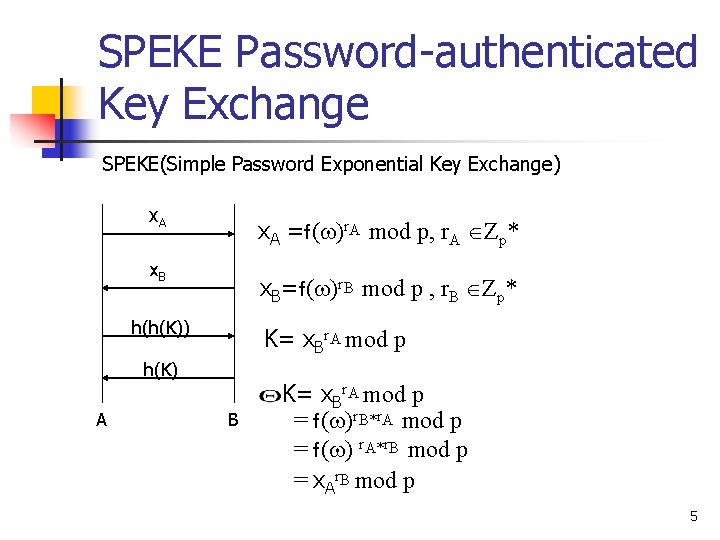
Analysis Of The Speke Password Authenticated Key Exchange

Zufe Mathematical Problems That No One Can Solve Programmer Sought
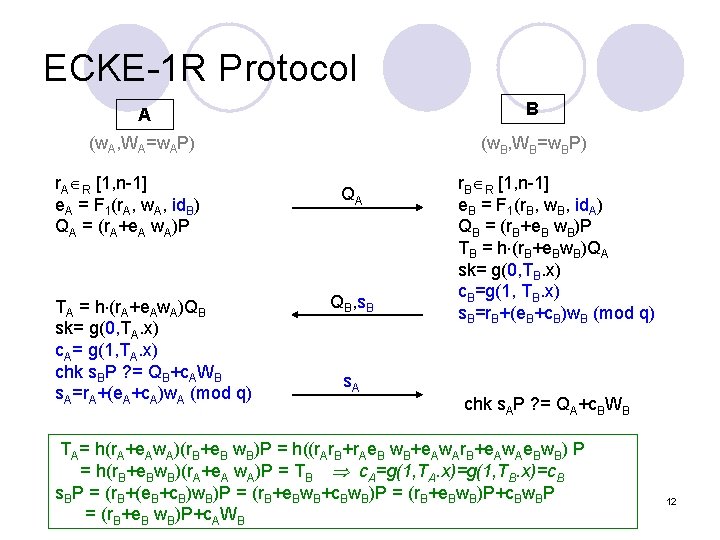
Cryptanalysis And Improvement Of An Elliptic Curve Diffiehellman

4 Key Agreement Ike 10 5 10 Points A Conside Chegg Com
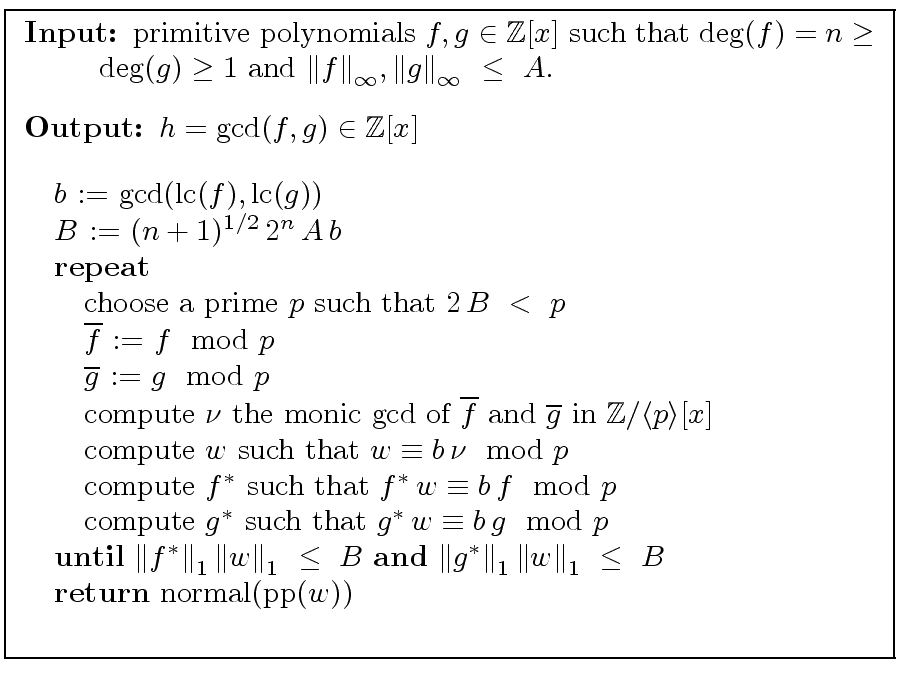
Modular Gcd Algorithms In

Consistent Hashing Hashing E G H X A X B Mod P Mod B Where P Is Prime P U A B Chosen Uniformly At Random From Z P X Is A

Pdf Projectivity Of Lp G W As A L1 G Module
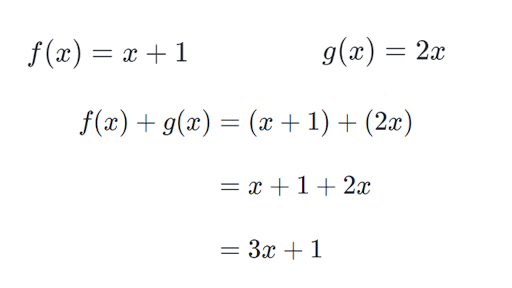
Intro To Combining Functions Article Khan Academy
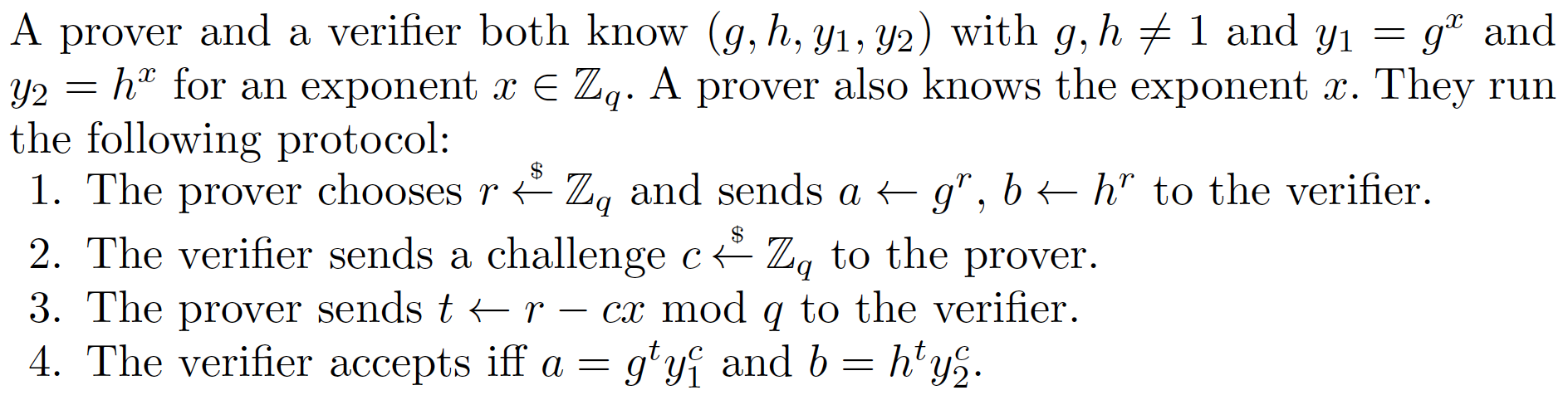
Non Interactive Zero Knowledge Nizk Proofs For The Equality Eq Of Discrete Logarithms Dl
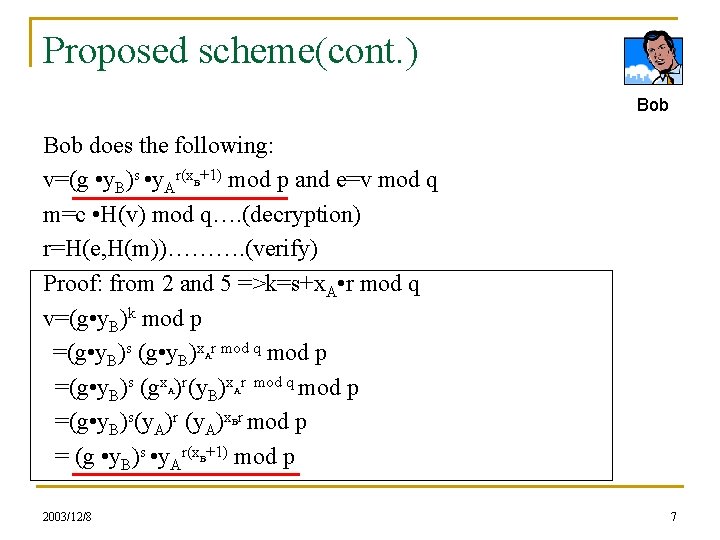
Publicly Verifiable Authenticated Encryption Author Changshe Ma And
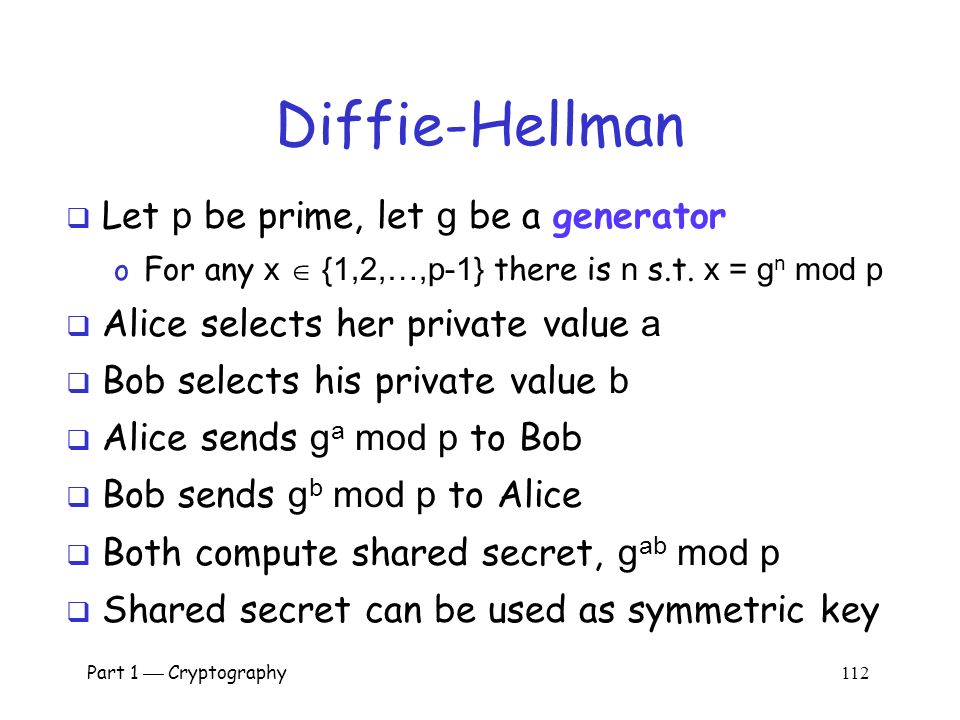
Part 1 Cryptography 1 Part I Crypto Chapter 2 Crypto Basics Mxdxbvtzwvmxnspbqxlimsccsgxscjxbovqxcjzmojzcvc Tvwjczaaxzbcsscjxbqcjzcojzcnspoxbxsbtvwjc Ppt Download

Kosniowski Topologia Algebraica Pdf Txt

Gmod Guess Who Hyperdimension Neptunia 15 Youtube

Solved 1 Define The Functions F X X Mod 10 G X X Chegg Com

Fujifilm X T3 Mirrorless Digital Camera Xt3 Camera Body Black B H

Garry S Mod Wikipedia
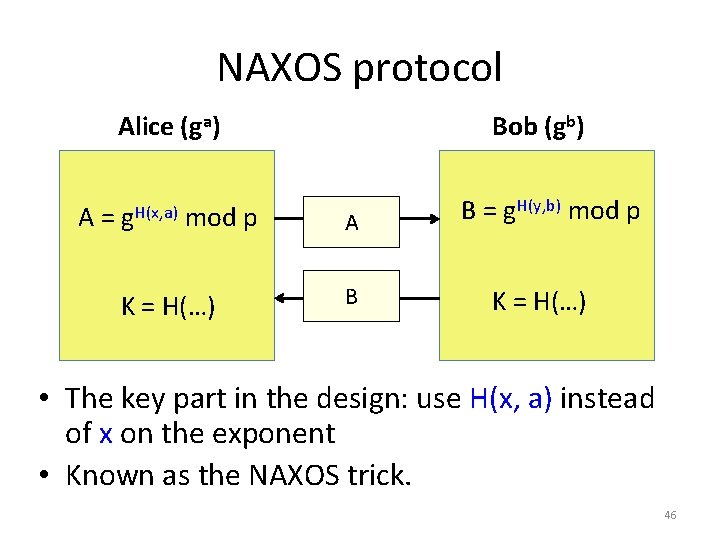
Robust Key Exchange Feng Hao Dependability Group Tech
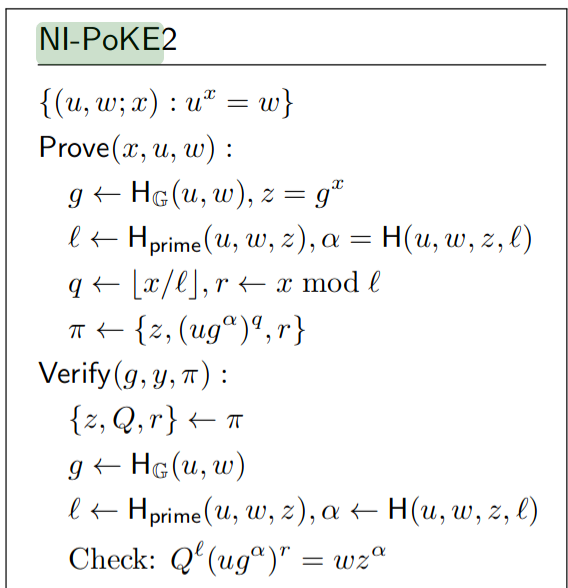
Rsa Accumulators For Plasma Cash History Reduction Plasma Ethereum Research

Solved Questions On Introduction To Cryptography Assignment 3 Math 373 Docsity

Quadratic Forms On Finite Groups Ii Wall 1972 Bulletin Of The London Mathematical Society Wiley Online Library

Convert Rgb Image To Hsv Image Hsv Image To Rgb Image Programmer Sought
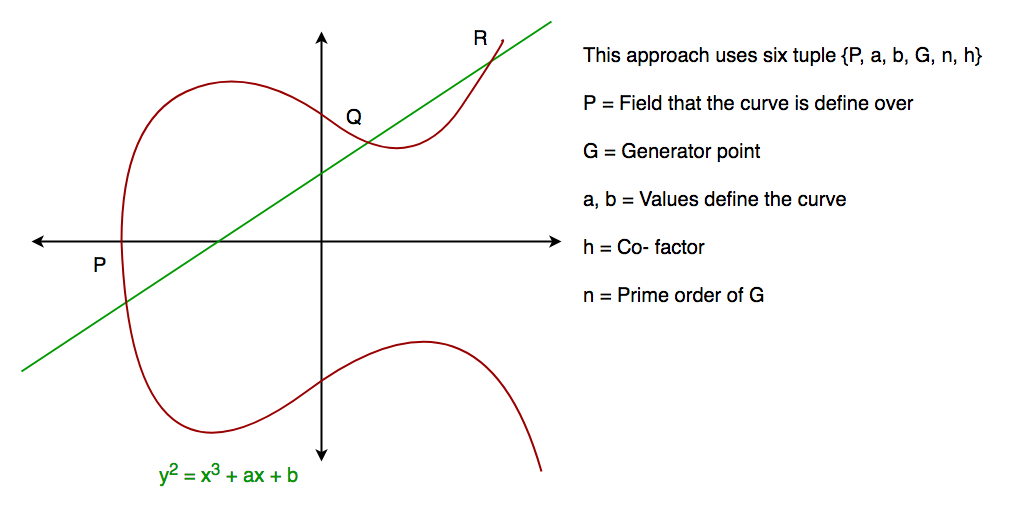
Implementation Of Diffie Hellman Algorithm Geeksforgeeks

Properties Of The Dft 1 Preliminaries A Definition B

Practice Problems On Hashing Geeksforgeeks

Our Identification Scheme Based On The Schnorr Identification Scheme Download Scientific Diagram

Gmod Amy S Black Magic 3 By Gflationmaster On Deviantart

1 L Functions Let N Be A Positive Number Z Nz The Ring Of Residues

Pdf Fpga Based Implementation Of Ecdsa For Secured Its

Even And Odd Functions Equations Video Khan Academy

Cryptography Notes Or The Reason I Will Not Be Seeing Day Flickr
.jpg)
Propac Medicines With Care Bags H 279 X W 3 X G 76mm Valley Northern Limited

Pdf Security And Privacy Using One Round Zero Knowledge Proofs Semantic Scholar
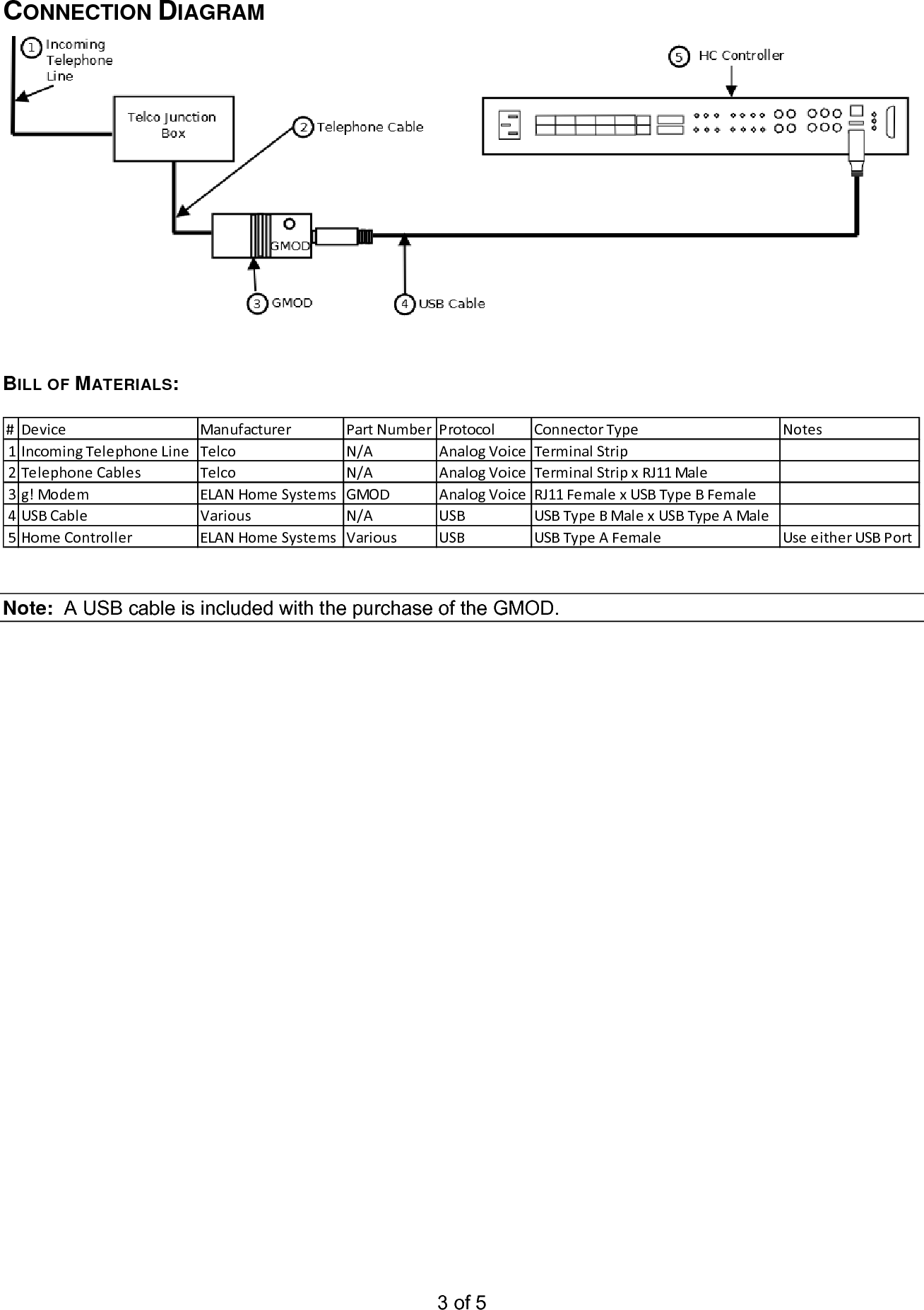
Pdf Gmod Integration Note User Manual
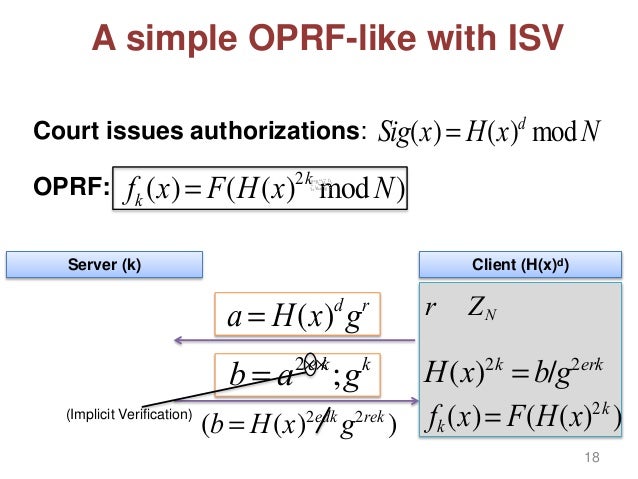
Privacy Preserving Information Sharing Tools And Applications

26 Hashing Concurrency Fall 21 Diderot
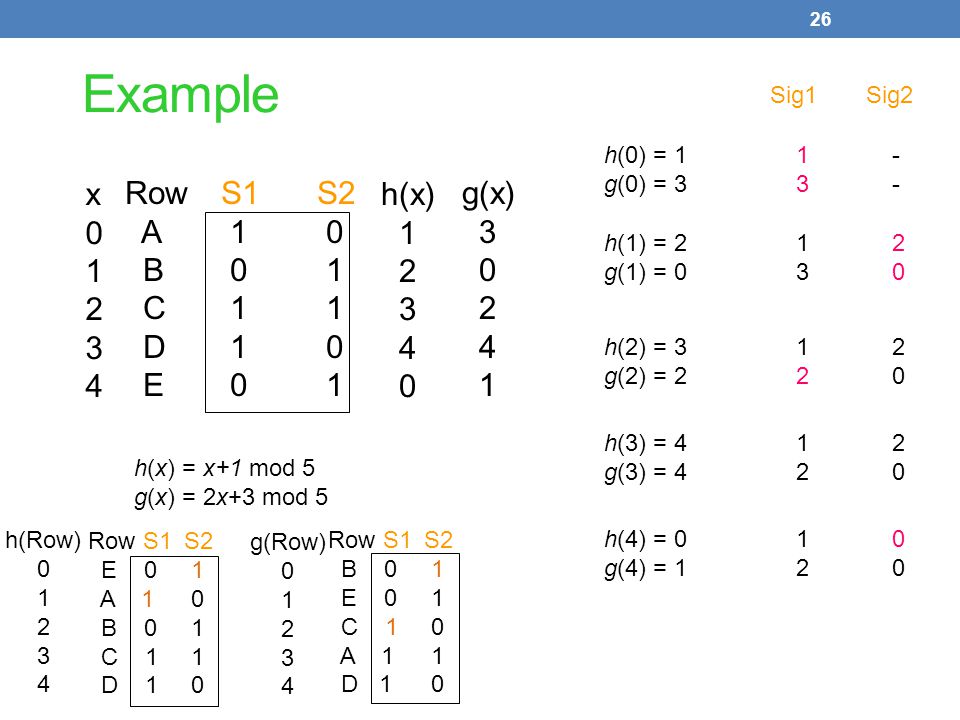
Min Hashing Locality Sensitive Hashing Clustering Ppt Video Online Download
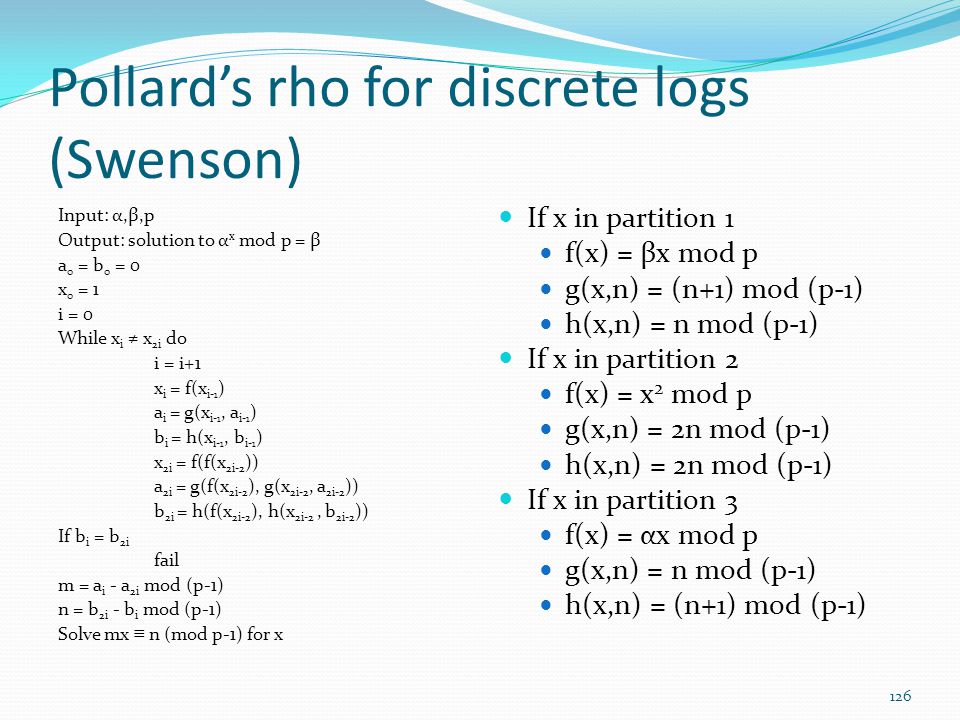
Instructor Name Dr Kerry A Mckay Date Of Most Recent Change 4 23 Ppt Download
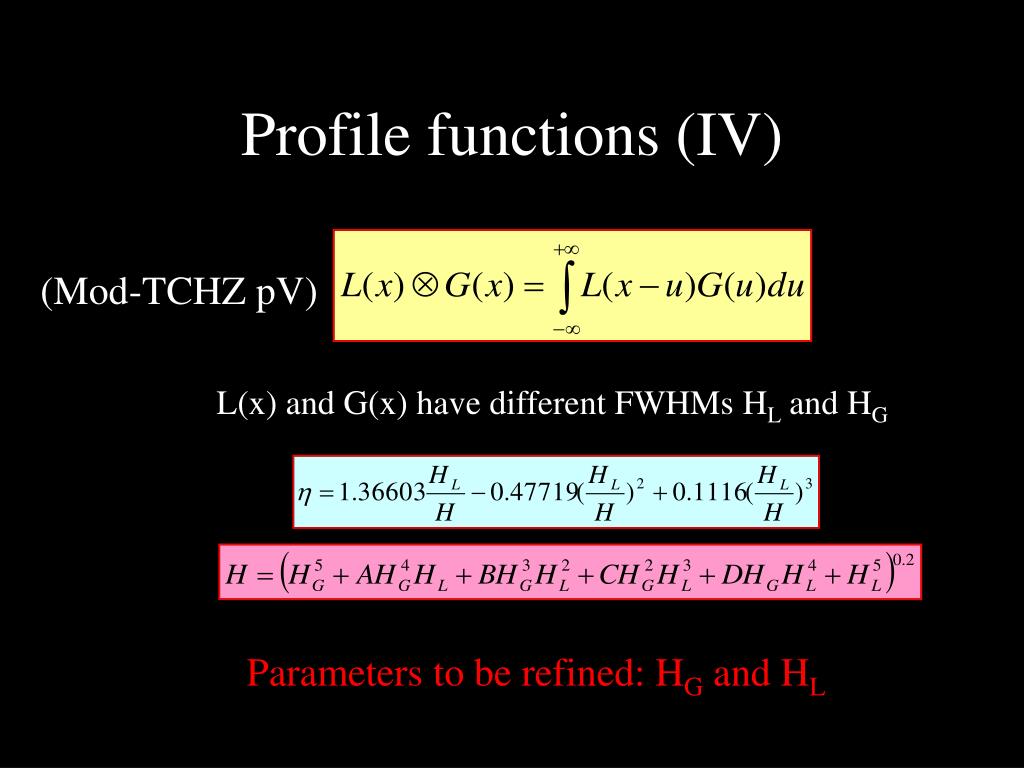
Ppt 陈小龙 中国科学院物理研究所 06 10 杭州 Powerpoint Presentation Id

Primitive Root Modulo N Wikipedia

Pictures Coding Crypto I 17 Dec 13
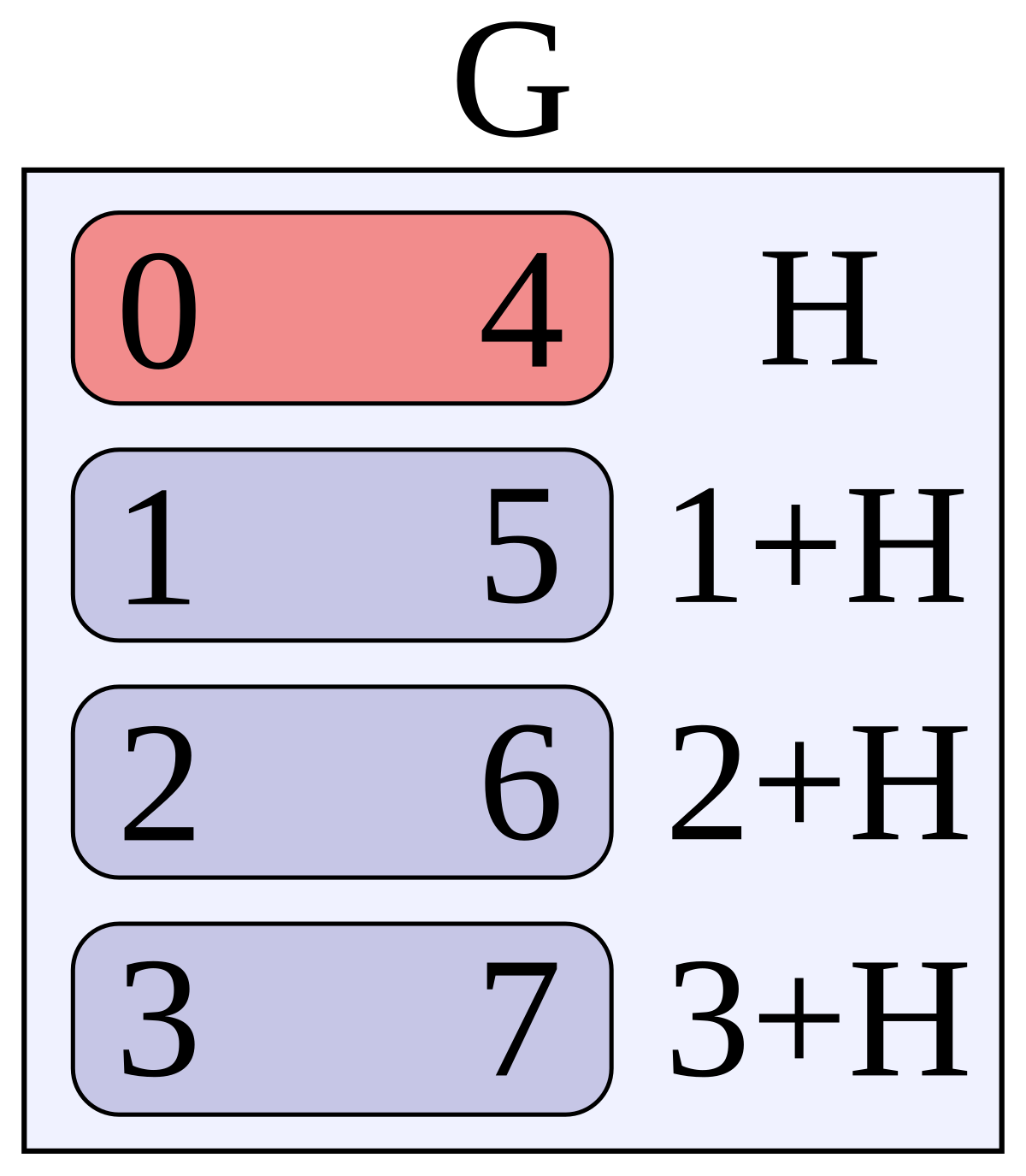
Coset Wikipedia
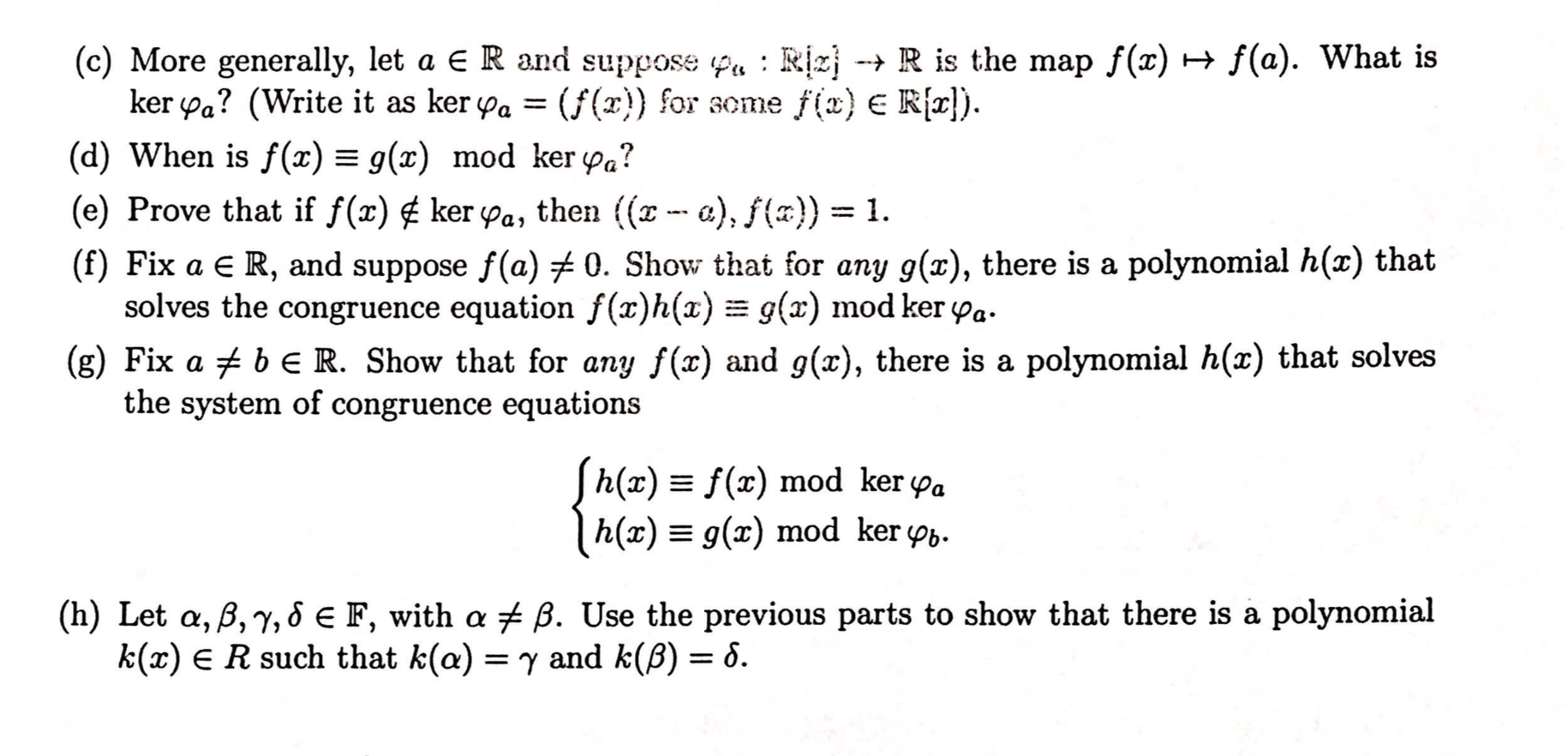
Solved 5 Recall That We Have Proved That Ker Y Is An Ide Chegg Com

Why A B Assumed Coprime Mathematics Stack Exchange
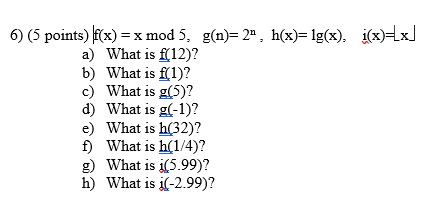
Solved 6 5 Points F X X Mod 5 G N 2 H X 1g X Chegg Com
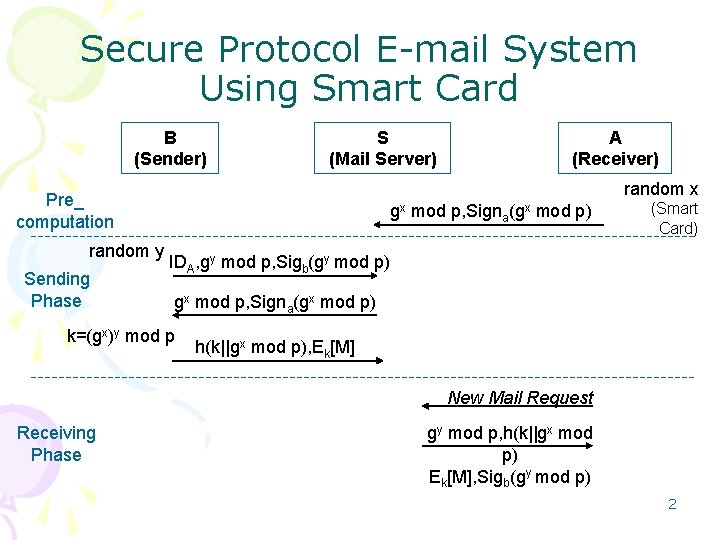
Secure Email Protocols Providing Perfect Forward Secrecy Authors

Pdf Singular A Computer Algebra System For Polynomial Computations

Midterm Exam For Introduction To Abstract Algebra Math 444 Docsity

4 Key Agreement Ike 10 5 10 Points A Conside Chegg Com

Cryptography Based On Quadratic Fields Cryptanalyses Primitives And Protocols Semantic Scholar
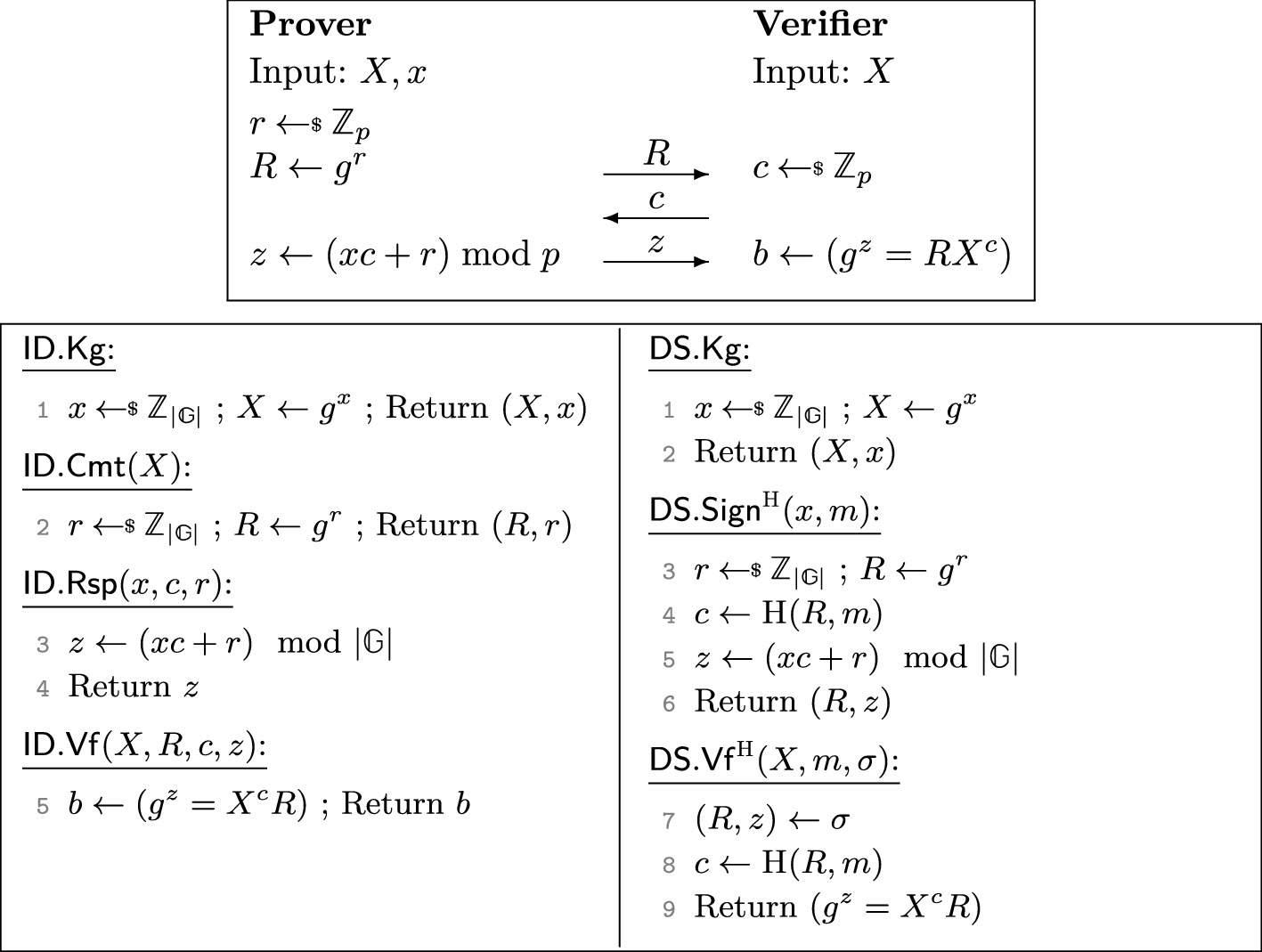
The Multi Base Discrete Logarithm Problem Tight Reductions And Non Rewinding Proofs For Schnorr Identification And Signatures Springerlink

Funciones Compuestas Y Sus Dominios Youtube
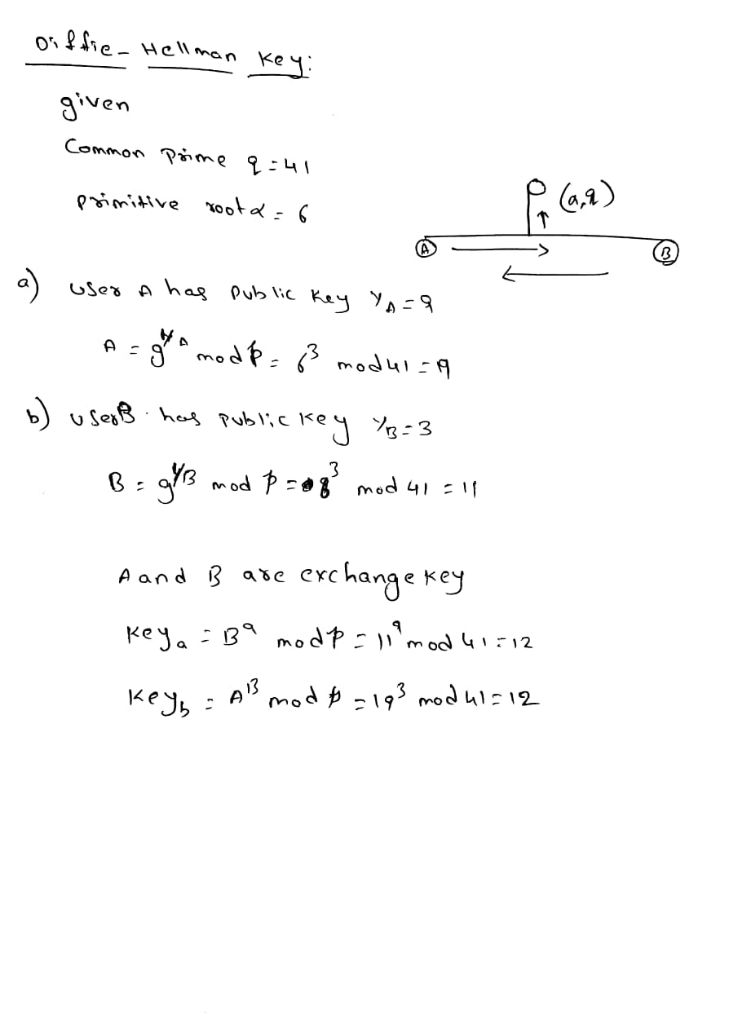
Solved Pls Give Answer Questions Dont Know Cause Stuck Solve Equation Like 6 X Mod 41 9 Need Step Q

Robust Off Line E Cash Scheme With Recoverability And Anonymity Revocation Wang 16 Security And Communication Networks Wiley Online Library
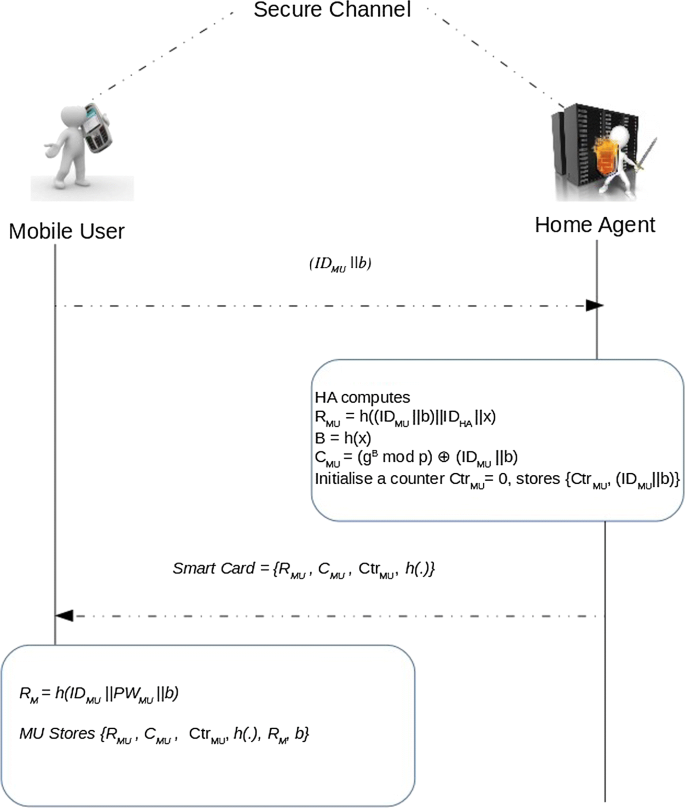
Mobile User Authentication Protocol With Privacy Preserving For Roaming Service In Glomonet Springerlink
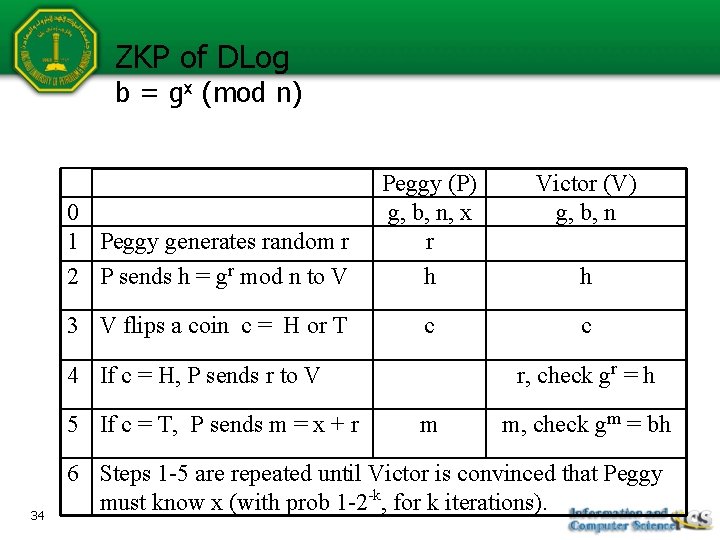
King Fahd University Of Petroleum Minerals College Of

Pdf A Secure Proxy Signature Scheme With Fault Tolerance Based On Discrete Logarithm Problem Semantic Scholar

Bk Gmod Minge 2 Hd Darkrp Youtube

Garry S Mod

Theorem 6 12 If A Permutation Of Sn Can Be Written As A Product Of An Even Number Of Transpositions Then It Can Never Be Written As A Product Of An Odd
Gale Academic Onefile Document An Advanced Encryption Standard Powered Mutual Authentication Protocol Based On Elliptic Curve Cryptography For Rfid Proven On Wisp

Borderland Weapon Mod 1 Revan657 Flickr
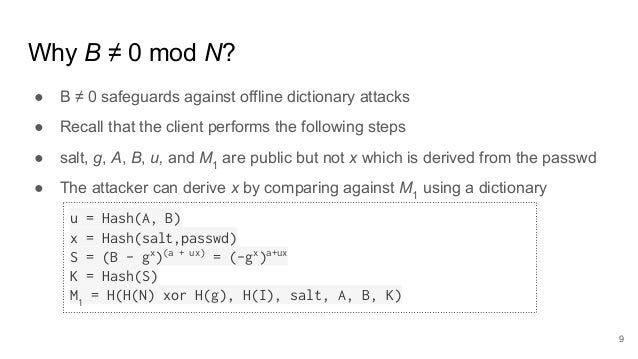
An Analysis Of Secure Remote Password Srp

Distributed Additive Encryption And Quantization For Privacy Preserving Federated Deep Learning Deepai

Enhanced Three Party Encrypted Key Exchange Without Server Public Keys Sciencedirect
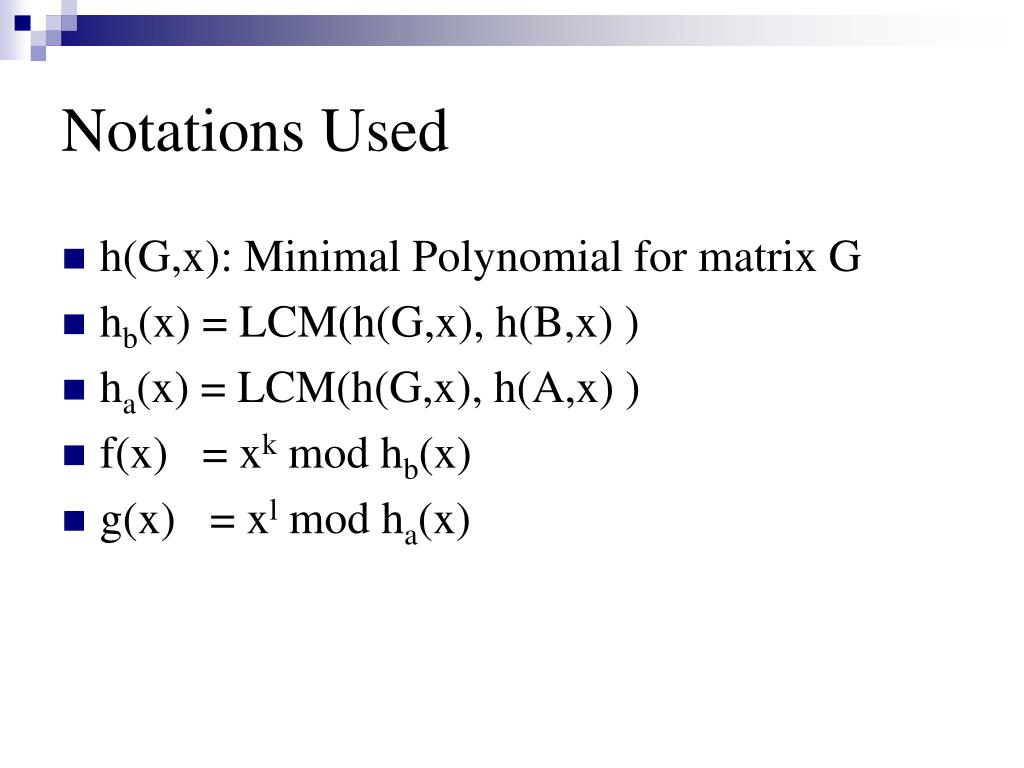
Ppt Weak Keys In Diffie Hellman Protocol Powerpoint Presentation Free Download Id

Dsc Thermograms Of A Pure Pvdf Hfp B P Mod S P Mod S E X Hybrid Download Scientific Diagram

Course 311 Part I Number Theory Problems Michaelmas Term 05




